Monitoring of Radio Advertisements
|
Workplace Communication
In today's workplace where there is a strained balance at best between computer security and employee privacy, steganography could be used as a very effective way of bypassing normal communication channels. Employees should have no expectation of privacy with respect to use of computers in the workplace.
Typically, Hotmail or other Internet-based meeting places are being used as ways of communicating outside and around the firewall. With security and privacy policies at the forefront, steganography may become the next big obstacle security officers have to face when it comes to controlling communication within their networks.
DNA Microdots
Taking what we know about microdots, we will explore the realm of hiding information in a strand of DNA. This provides the sender with a mechanism for hiding a message among a staggeringly large number of similar molecules while keeping the size down to a standard microdot.
A single strand of DNA consists of a chain of simpler molecules called bases, which protrude from a sugar-phosphate backbone. The four varieties of bases are known as adenine (A), thymine (T), guanine (G), and cytosine (C). Any strand of DNA will adhere tightly to its complementary strand, in which T substitutes for A, G for C, and vice versa. For example, a single-stranded DNA segment consisting of the base sequence TAGCCT will stick to a section of another strand made up of the complementary sequence ATCGGA. The links between pairs of bases are responsible for binding together two strands to form the characteristic double helix of a DNA molecule.
| A = CGA |
| B = CCA |
| C = GTT |
| D = TTG |
| E = GGC |
| F = GGT |
| G = TTT |
| H = CGC |
| I = ATG |
| J = AGT |
| K = AAG |
| L = TGC |
| M = TCC |
| N = TCT |
| O = GGA |
| P = GTG |
| Q = AAC |
| R = TCA |
| S = ACG |
| T = TTC |
| U = CTG |
| V = CCT |
| W = CCG |
| X = CTA |
| Y = AAA |
| Z = CTT |
| _ = ATA |
| , = TCG |
| = GAT |
| : = GCT |
| 0 = ACT |
| 1 = ACC |
| 2 = TAG |
| 3 = GAC |
| 4 = GAG |
| 5 = AGA |
| 6 = TTA |
| 7 = ACA |
| 8 = AGG |
| 9 = GCG |
They used the encryption key to encode a message reading "JUNE6_INVASION:NORMANDY" as a sequence of 69 bases and synthesized the following DNA strand (Figure 8.1):
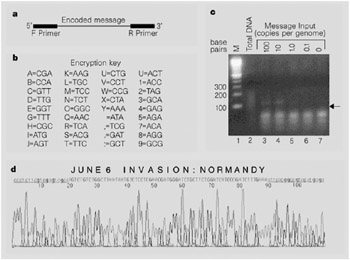
Figure 8.1
AGTCTGTCTGGCTTAATAATGTCTCCTCGAACGATGGGATCTGCTTCT
GGATCATCCCGATCTTTGAAA
Because DNA is a very stable molecule under normal conditions, and PCR is a very sensitive analytic technique, a DNA message can be hidden almost anywhere, Risca notes.
In their proof-of-principle experiment, the researchers dripped a small quantity of DNA-containing solution onto a small dot printed on filter paper. They cut out the dot, taped it over the period in a typed letter, and mailed the letter. The recipient recovered the dot, performed the analysis, and successfully decoded the secret message. Our technique could therefore be used in a similar way to the original microdots: to enclose a secret message in an innocuous letter.
|
EAN: 2147483647
Pages: 220