Default Honeyd Scripts
 |
| |||||||||||
| | |||||
The Windows version of Honeyd (http://www.securityprofiling.com/honeyd/honeyd.shtml) comes with three default scripts located in the \scripts folder. See Table 7-1 for their names and descriptions.
| Script Name | Language | Description |
|---|---|---|
| Router-telnet.pl | Perl | Mimics a generic telnet logon session to a Cisco router |
| Test.sh | Shell | Mimics a SSH logon session |
| Web.sh | Shell | Mimics an IIS 5.0 default home web page with standard directories |
The default scripts that arrive with the Windows version of Honeyd have the distinct advantage of not being compressed in a Unix archive file format. Unix-style scripts are usually Gzipped and/or stored as tarballs (covered in Chapter 5), so they must be uncompressed to their plain-text script formats.
Unfortunately, every script, whether included with the Windows version of Honeyd or downloaded from the Honeyd web site, contains scripting commands that must be converted to Windows-style commands to run appropriately. Let’s start with examining the three default scripts that come with the Windows version of Honeyd.
SSH Test Script
The Test.sh service script, shown in Listing 7-1, is appropriately named. It is a short script, barely mimicking a SSH login session. (SSH command shells normally run on TCP port 23.) It prints the following line on connection:
SSH-1.5-2.40
Listing 7.1: Source Code of Test.sh
DATE=`date` echo "$DATE: Started From $1 Port $2" >> /tmp/log echo SSH-1.5-2.40 while read name do echo "$name" >> /tmp/log echo "$name" done
It then records any typed in data, potentially tracking login names and passwords entered by the intruder. The information is saved, along with the date, to a log file. This simple script can be executed as a test script to make sure Honeyd is working correctly or modified with more functionality.
Unfortunately, even this simple service script needs modification in order to work properly on a Windows system. The log file path and name need to be converted to Windows syntax. Listing 7-2 shows the change, using ssh.log as the file name.
Listing 7.2: Modified Test.sh
DATE=`date` echo "$DATE: Started From $1 Port $2" >> ssh.log echo SSH-1.5-2.40 while read name do echo "$name" >> ssh.log echo "$name" done
This script is very rudimentary.
Cisco Telnet Session Script
Listing 7-3 shows the Perl source code of Router-telnet.pl. This script was created by Dr. Provos and mimics a generic telnet session to a Cisco router. It first displays a generic privacy disclaimer warning users that all activity may be monitored. This is an important warning that should be included in all honeypot service scripts. As explained in Chapter 1, the use of a honeypot may result in additional legal responsibilities and liabilities. Without appropriate disclosure, hackers might be able to claim that their expectation of privacy was violated or that their communications were monitored without their consent. A disclosure, like the one presented in Router-telnet.pl, may satisfy the legal requirement of both claims.
Listing 7.3: Source Code of Router-telnet.pl
# Copyright 2002 Niels Provos <provos@citi.umich.edu> # All rights reserved. # For the license refer to the main source code of Honeyd. # Don't echo Will Echo Will Surpress Go Ahead $return = pack('ccccccccc', 255, 254, 1, 255, 251, 1, 255, 251, 3); syswrite STDOUT, $return, 9; $string = "Users (authorized or unauthorized) have no explicit or\r implicit expectation of privacy. Any or all uses of this\r system may be intercepted, monitored, recorded, copied,\r audited, inspected, and disclosed to authorized site,\r and law enforcement personnel, as well as to authorized\r officials of other agencies, both domestic and foreign.\r By using this system, the user consents to such\r interception, monitoring, recording, copying, auditing,\r inspection, and disclosure at the discretion of authorized\r site.\r \r Unauthorized or improper use of this system may result in\r administrative disciplinary action and civil and criminal\r penalties. By continuing to use this system you indicate\r your awareness of and consent to these terms and conditions\r of use. LOG OFF IMMEDIATELY if you do not agree to the\r conditions stated in this warning.\r \r \r \r User Access Verification\r "; syswrite STDOUT, $string; open(O, ">C:\\fff"); $count = 0; while ($count < 3) { do { $count++; syswrite STDOUT, "\r\n"; $word = read_word("Username: ", 1); } while (!$word && $count < 3); if ($count >= 3 && !$word) { exit; } $password = read_word("Password: ", 0); if (!$password) { syswrite STDOUT, "% Login invalid\r\n"; } else { syswrite STDERR, "Attempted login: $word/$password"; syswrite STDOUT, "% Access denied\r\n"; } } exit; sub read_word { local $prompt = shift; local $echo = shift; local $word; syswrite STDOUT, "$prompt"; $word = ""; $alarmed = 0; eval { local $SIG{ALRM} = sub { $alarmed = 1; die; }; alarm 30; $finished = 0; do { $nread = sysread STDIN, $buffer, 1; print O "RET: " . $nread . " BUF: " . $buffer . "\n"; die unless $nread; if (ord($buffer) == 0) { ;#ignore } elsif (ord($buffer) == 255) { sysread STDIN, $buffer, 2; } elsif (ord($buffer) == 13 || ord($buffer) == 10) { syswrite STDOUT, "\r\n" if $echo; $finished = 1; } else { syswrite STDOUT, $buffer, 1 if $echo; $word = $word.$buffer; } } while (!$finished); alarm 0; }; syswrite STDOUT, "\r\n" if $alarmed || ! $echo; if ($alarmed) { syswrite STDOUT, "% $prompt timeout expired!\r\n"; return (0); } return ($word); } The script then prompts the connecting user to log in with the text prompt:
User Access Verification Username:
This is the standard text presented when telnetting to a Cisco router, although sometimes the exact text is not presented until after the first failed login. The typed-in login name is echoed back to the user, and when an Enter keypress is detected (indicating the end of the user name), the user is prompted for her password. No matter what login name and password are entered, the result is an error message indicating an invalid login. The invalid login messages are as follows:
%Login invalid %Access denied
The script even contains a realistic timeout provision. If the connected user has not successfully typed in both a login name and password in 30 seconds, the user will be given the following message:
timeout expired!
This is also an accurate behavior of most Cisco routers. Figure 7-1 shows the screen honeypot intruders would see.
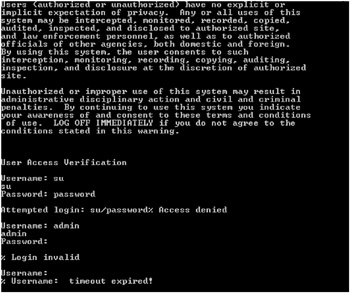
Figure 7-1: Example of the Router-telnet Perl script in action
IIS Web Emulation
The Web.sh script, shown in Listing 7-4, contains a simple emulated IIS 5.0 web page. The script looks for the following HTTP request:
GET .scripts. *cmd.exe. *dir.* HTTP/1.0
Listing 7.4: Source Code of Web.sh
#!/bin/sh REQUEST="" while read name do LINE=`echo "$name" | egrep -i "[a-z:]"` if [ -z "$LINE" ] then break fi echo "$name" >> /tmp/log NEWREQUEST=`echo "$name" | grep "GET .scripts.*cmd.exe.*dir.* HTTP/1.0"` if [ ! -z "$NEWREQUEST" ] ; then REQUEST=$NEWREQUEST fi done if [ -z "$REQUEST" ] ; then cat << _eof_ HTTP/1.1 404 NOT FOUND Server: Microsoft-IIS/5.0 P3P: CP='ALL IND DSP COR ADM CONo CUR CUSo IVAo IVDo PSA Content-Location: http://cpmsftwbw27/default.htm Date: Thu, 04 Apr 2002 06:42:18 GMT Content-Type: text/html Accept-Ranges: bytes <html><title>You are in Error</title> <body> <h1>You are in Error</h1> O strange and inconceivable thing! We did not really die, we were not really buried, we were not really crucified and raised again, but our imitation was but a figure, while our salvation is in reality. Christ was actually crucified, and actually buried, and truly rose again; and all these things have been vouchsafed to us, that we, by imitation communicating in His sufferings, might gain salvation in reality. O surpassing loving-kindness! Christ received the nails in His undefiled hands and feet, and endured anguish; while to me without suffering or toil, by the fellowship of His pain He vouchsafed salvation. <p> St. Cyril of Jerusalem, On the Christian Sacraments. </body> </html> _eof_ exit 0 fi DATE=`date` cat << _eof_ HTTP/1.0 200 OK Date: $DATE Server: Microsoft-IIS/5.0 Connection: close Content-Type: text/plain Volume in drive C is Webserver Volume Serial Number is 3421-07F5 Directory of C:\inetpub 01-20-02 3:58a <DIR> . 08-21-01 9:12a <DIR> .. 08-21-01 11:28a <DIR> AdminScripts 08-21-01 6:43p <DIR> ftproot 07-09-00 12:04a <DIR> iissamples 07-03-00 2:09a <DIR> mailroot 07-16-00 3:49p <DIR> Scripts 07-09-00 3:10p <DIR> webpub 07-16-00 4:43p <DIR> wwwroot 0 file(s) 0 bytes 20 dir(s) 290,897,920 bytes free _eof_
This connection request is often associated with attackers and scanning malware looking for insecure IIS servers. If detected, the script will respond with what looks like a directory listing of a default IIS 5.0 server installation:
Directory of C:\inetpub 01-20-02 3:58a <DIR> . 08-21-01 9:12a <DIR> .. 08-21-01 11:28a <DIR> AdminScripts 08-21-01 6:43p <DIR> ftproot 07-09-00 12:04a <DIR> iissamples 07-03-00 2:09a <DIR> mailroot 07-16-00 3:49p <DIR> Scripts 07-09-00 3:10p <DIR> webpub 07-16-00 4:43p <DIR> wwwroot 0 file(s) 0 bytes 20 dir(s) 290,897,920 bytes free
If the request is anything else, an emulated 404 (file not found) error message is sent, along with some religious bible quotations. All HTTP requests are logged to a file. If this limited script is used, the following changes should be made:
-
Convert the log file location and name to Windows style.
-
Change the Content-Location: field to reflect the correct web address.
-
Change the drive volume label to something other than Webserver.
-
Change the 404 error text to something other than the default Christian quote.
-
Change the number of bytes free and folder times and dates.
These changes should be made so that inquiring hackers don’t see the default text associated with Honeyd’s IIS Web.sh script.
None of the default scripts are overly interesting or complicated, but they are great for using as a base when creating your own service scripts.
| | |||||
EAN: 2147483647
Pages: 119