Chapter 4: User Account Control
User Account Control (UAC) is probably one of the most visible, and most talked about, security features in Windows Vista. Whenever you attempt to take an action that only administrators can perform you get a dialog box asking whether you really want to do this, as shown in Figure 4-1.
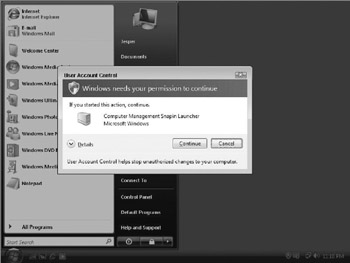
Figure 4-1: UAC approval dialog box for administrator in admin-approval mode
Despite the visibility of, and all the opinions about, UAC, we do not believe that most of the discussion is carried out in light of what UAC really is. In fact, there seems to be some real confusion out there. It is very clear that many pundits have not bothered to fully understand UAC, what it is, and how it works. They write blog posts, newsgroup postings, and articles with titles like "Vista's most annoying feature" and they pontificate on how many people will turn it off, and why it is so annoying in the first place.
Unfortunately, much of the advice to turn off UAC is based on an initial experience. You should expect that, while you are configuring your computer, you will have a very different administrative experience than you will have once the computer is in a steady state. The first few weeks will be quite different from the following few weeks.
Introduction
UAC is Microsoft's long-awaited solution to the problem that 90+ percent of end users on the Windows platform run with administrative privileges. That means that malware that attacks the users themselves, or the applications they run, will have the run of the computer on 90 + percent of the systems they see. On Windows XP, you can run as a regular user, but for many of us, it is plain painful. For instance, if you travel across multiple time zones you find that as a regular user it is unable to modify the time zone.
UAC is actually a collection of technologies that Microsoft developed to achieve several different goals. In this chapter we introduce you to UAC. We tell you what it is, and why it is implemented the way it is. We attempt to answer some common questions about it, and finally, we give you our recommendation for how to manage it. We should be honest up front: We do not hate it, and both of us believe it is an important security feature. We both leave it on for ourselves and our users. We do not have any illusions, however, that it is a panacea. Between the two of us, we have run our computers with it turned on for over a year and a half, through various betas. While this may not seem like a great deal of time, it has given us a fair amount of experience with it. Given how controversial it is, we try to be as objective as we can, presenting you with the facts so that you can make your own decisions about how to manage UAC.
Before we jump into our discussion, here are a few facts about UAC:
-
While sometimes it's frustrating, it is not deliberately designed to be the most annoying feature in the history of Windows.
-
It will not stop really good attackers, or those that have the help of really good attackers. UAC is designed to set us on a path where users do not need to expose their system to potentially malicious code as often as they do today. That does not mean that successful privilege elevation attacks will not occur. If the bad guys can't think of any other way to defeat UAC, they will almost certainly resort to asking the user to do it for them. Given the choice of dancing pigs and security, we know from experience that the dancing pigs will win every time. UAC does not provide foolproof security. In fact, it makes the good old local privilege elevation attack interesting again. These attacks have largely been discounted because, on Windows, nearly everyone was an admin anyway so elevating to some other admin was quite pointless. That being said, UAC definitely changes the nature of such attacks, and to that end, changes the rules of the game to ones similar to what we have had on Unix for 20+ years.
-
It will not stop bad guys from stealing your personal data. A user's personal data is accessible to that user, regardless of that user's privilege. As such, an application, including malicious ones, can access it. UAC does not, and cannot, change that. It does not remove the need to be vigilant, distrustful, and paranoid-attributes that we should all instill in our end users.
EAN: N/A
Pages: 163