Chapter 2: How Hackers Attack
It is crucial that Windows security defenders understand how malicious hackers can attack and exploit their systems. Only when attacks are thoroughly understood can sufficient defenses be designed and implemented. Thus, this chapter focuses on the major methods of malicious exploitation.
Malicious Exploitation
Microsoft Windows is the most attacked PC desktop OS in the world, coming under attack from both dedicated hackers and automated malicious software. Regardless of whether the attack is occurring as a results of skilled human hands or pre-programmed malware, both methods use one of eight techniques to exploit a computer.
Logon credential guessing/cracking OS or application misconfiguration
Eight Exploitation Techniques
-
Logon credential guessing/cracking
-
Buffer overflow
-
OS or application vulnerability
-
OS or application misconfiguration
-
Eavesdropping/man-in-the-middle attack
-
Denial of service attack
-
Client-side attack
-
Social engineering
There are many different types of attacks, but these are the major ones. The next section of the chapter covers each of the techniques in more detail.
Logon Credential Guessing/Cracking
Logon credential password guessing and cracking are among a hacker's (or worm's) favorite attacks. Many sources call this technique "password cracking," but that name is an oversimplification of the subject. First, users don't always use passwords in their logon sequence. They can use passphrases, biometrics, smart cards, fingerprint scanning, digital certificate, or some other form of logon authentication. With that said, most logon authentication is password-based. Second, if the attacker has to guess the user's (or computer's) logon name (i.e., identity label) as well, it is more accurate to call it "credential hacking" than "password hacking." There is also a difference between guessing and cracking.
Password Guessing
Password guessing is literally guessing at the password, whether manually or by using an automated program. Guessing is done against an active logon interface. In Windows, if the appropriate services are active, it can be done against many server applications, including the normal Windows logon, RRAS VPNs, NetBIOS, Remote Desktop, Remote Assistance, Terminal Services, SMTP, POP, IMAP, MS-SQL, FTP, Telnet, and Web sites (if an HTTP authentication method besides anonymous is turned on)-basically, anywhere the attacker can get a logon prompt, including any third-party utilities (for example, PC Anywhere, VNC, Hyena, and so on).
Guessing is very common, but slow. It must be performed against a logon GUI or text-based prompt, and each guessing attempt must wait for the logon service to respond successfully or not, before starting the next attempt unless multiple sessions are used. Often the quickest logon attempt interval is 1–2 seconds at best. While that might not sound slow, it is too slow if the attacker has to guess millions of different passwords.
Automated Password Guessers
Many password-guessing crackers use software tools to automate the task. A password-guessing program can input password after password against a logon screen until the passwords it is guessing are exhausted, the account is locked out, or the cracking attempt is successful.
Another benefit of automated tools is that they can often start multiple login sessions at once. Some tools let the attacker start any number of logon sessions that the attacker wants, limited only by network bandwidth (if the guessing attempt is being done over a network connection) and the processing capability of the computer being attacked. Of course, as the attacker increases the number of simultaneous attack sessions and guesses, the chances of being detected increased. In practice, most attackers limit the number of concurrent logon sessions to fewer than two dozen. Some computer services will fail to accept more than 1 or 2 at a time. If an account lockout mechanism is enabled, the attacker may be forced to limit the guessing to 1 or 2 passwords per 5-or 10-minute period, so the attacker doesn't disable the used logon account. How many guesses and sessions are allowed depends on the service being attacked and the logon security used.
The most popular automated password guessing program in use today is The Hacker's Choice's Hydra program (http://www.thc.org). Hydra is a command-line program that is available for Windows, Linux, PDAs, and cell phones. It allows an attacker to guess at multiple user names, with multiple password guesses, against multiple servers, all at once. It supports dozens of logon services, including those Windows services mentioned previously, plus Cisco, MySQL, Oracle, and many more. Figure 2-1 shows Hydra running against a Telnet service.
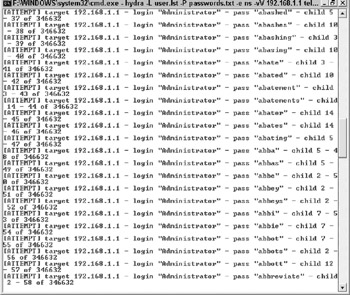
Figure 2-1: Hydra automated password guessing program being used against a Telnet service
Password guessing can be easier if the target's password policy is known. For instance, suppose the password policy says that the minimum password size is 6, must contain one uppercase letter, and must contain at least one non-alphabetic character (the same as Vista's default password complexity policy). If the minimum password size is 6, most users' passwords will be six or seven characters long. If it must contain an uppercase letter, most users will put the capitalized letter at the beginning of the password. And if a non-alphabetic character is needed, most users will choose the numbers 1 or 2, or choose among the following commonly used symbols: !@#$.
If the user can choose his or her own password (versus having a computer randomly select it), it will more than likely be a complete word or have a root that is nearly a complete word, name, or subject. This makes the password easier to remember. For example, given the preceding password policy, common passwords might be Password2, Football!, Michael1.
Types of Password Guessing
If a password attack just begins guessing by using all the possible symbols that might be in a password (for example, a, aa, aaa, ab, abb, bbb, and so on) instead of whole words, it is considered to be a brute force password attack. Brute force attacks are computationally the most difficult of password attacks to pull off.
Most users use a password with a common word root (for example, frog, password, guess, and so on). Password guessing attacks that guess using complete words that might appear in a dictionary are known as password dictionary attacks.
Often password polices force a user to include some additional characters (for example, numbers or symbols) to defeat password dictionary attacks. Most users end up with passwords that have a common word root, but contain additional characters (for example, Frog2, Password32, P@ssw0rd, and so on). Password attacks that guess using common dictionary words that are then given additional complexity are known as password hybrid attacks.
In general, brute force attacks are used only when the attacker has no idea of the potential passwords or their complexity. Password dictionary attacks are very common, and often are the only real choice when time is of the essence. Hybrid guessing attacks are mandatory when the password policy disallows simple dictionary words.
It helps the attacker considerably if he has an idea of what the password might be, such as the user's personal information or hobby. It is common for users to include their children's names or loved one in their password. If onsite at the user's computer, an attacker would look for the pictures of the people displayed closest to the user's desktop. Hobbies and sports are often used as passwords. For CEOs always try something related to golf or the car they drive. When in Washington, D.C., always try Goskins!. When in Chicago try Gobulls!. You would be surprised how often the latter two work when in those towns.
Password Dictionaries
Password guessers/crackers often use a password dictionary file, which is a collection of potential passwords to be used in automated attacks. The best password dictionaries contain all the possible complete words in the user's native tongue, plus hybrid variations that include near-spellings, mixed case-sensitivity, and so on.
The best English password dictionary the author has come across was 87,000 words. The number of total words in the English language is over 877,000 (http://www.languagemonitor.com). So, the best password guessing dictionary contains only 10 percent of the possible words. But in practical use, most users have a working vocabulary of under 10,000 words. Still, the better the password dictionary is, the more likely the attacker will be at guessing and cracking passwords.
Anyone can search for and find password dictionaries on the Internet. Once when I was having a hard time cracking administrative and root passwords on a particular network, I learned that the network administrator was a big Star Trek television show fan. I downloaded a Klingon-based dictionary file and cracked all the admin passwords in a few minutes.
Problems with Password Guessing
There are three major problems with password guessing: length of time, account lockout, and event logging. If the user account being attacked has a complex password and the attacker doesn't know the password policy or have hints about the possible password, it could literally take millions of guesses to get the correct password. Even with an automated password guessing attack, it could take years (if ever) to successfully guess a correct password.
Further complicating the issue is the password guessing defense of account lockout. The term "account lockout" describes any logon mechanism that disables an otherwise valid logon account after a predetermined number of successive bad password attempts. The lockout can be temporary (for example, 1 minute long) or remain in a locked out state until an administrator resets the account lockout password counter mechanism. Also, even if account lockout is not enabled, many operating systems and services, including the Windows logon service, will delay future logon tries for a random time period (usually only a few seconds) after multiple bad passwords have been attempted. This is known as an "anti-hammering" defense.
Any good logon mechanism should be monitored for failed logins. Often a high number of successive password failures will generate a "bad logon" event message, which the administrator can view or be notified about. When any of the three issues just described (excessive length of time, password complexity, or account lockout) is involved, most password attackers would rather crack than guess.
Password Cracking
Password cracking involves capturing the password in an obscured form (for example, hashed, encrypted, and so on) and then computationally converting the obscured form back to its plain-text original. For example, Windows logon passwords are stored as password hashes in the authentication databases. If the password hashes can be obtained by an attacker (more detail on this in Chapter 3), the hashes can be computationally attacked and converted to their plain-text equivalents. When you hear the term "password cracking," this is what they are talking about.
Traditional password cracking works by taking a plain-text password guess, hashing it using the same hashing algorithm as the captured password hashes, and then comparing it to the extracted password hashes. If the newly computed hash and captured hash agree, then a plain-text password match is found.
In order to get the Windows logon password hashes, typically the hacker needs administrative access to the computer she is attacking or local physical access. With administrative access, it is possible to obtain the hashes locally or remotely. The attacker can also obtain the password hashes by sniffing the network communications between users and computers, and their remote authentication servers. Last, if BitLocker Drive Encryption (discussed in Chapters 1 and 5) is not enabled, the hacker can obtain the password hashes by accessing the Windows computer locally and physically copying the authentication database to portable media.
The major benefit of password cracking, once the original hurdle of how to obtain the password hashes is overcome, is speed. Many password cracking tools can do tens of thousands to over a million password cracking computations a second.
Two of the most common password hash-cracking programs are John the Ripper (http://www.openwall.com/john) and Cain & Abel (http://www.oxid.it/cain.html). John the Ripper is the more popular of the two, and works on Linux, Windows, and other platforms. It is a very fast command-line utility. It can crack Windows, Linux, Cisco, and other password hashes. It also has a distributed version, Distributed John (http://www.ktulu.com.ar/en/djohn.php), which can split the overall computational workload over multiple computers.
Cain & Able is a Windows-only GUI program that is capable of cracking over 25 different types of password hashes, including Windows, Cisco, and MS-SQL hashes. Cain & Able isn't as fast as John the Ripper, but with its click-and-point GUI, it's a lot prettier and easier to use. Figure 2-2 shows Cain & Able cracking a short 6–8 character password. Trying over 2 million calculations a second, Cain & Able will be able to crack the password in 15 days if the password is only 6–8 characters long and contains only the characters Cain & Able was instructed to use in the attack.
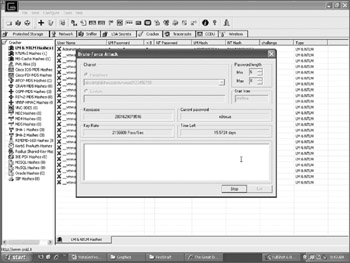
Figure 2-2: Cain & Able being used to crack Windows password hashes
Depending on the password's complexity, password crackers may have to try millions, and even millions of trillions of hash computations. Again, knowing the password policy and using a password or dictionary attack is often the best way to compromise the password.
Two relatively new techniques have made password cracking even faster. One uses pre-computed hash tables. With this method, every possible plain-text password (or likely subset thereof) is generated beforehand, hashed, and placed into a database lookup table. Then the attacker inputs the captured hash into the accompanying cracking program, it looks up the identical hash, and displays the plain-text password.
However, pre-computer hash tables can be very large, gigabytes big just to list the short ordinary password choices; and slow to generate. It then takes gigabytes of permanent storage and memory to use the table. An even better technique using rainbow tables (http://www.en.wikipedia.org/wiki/Rainbow_table) is now often used to crack certain types of captured password hashes (including Windows password hashes) faster.
Hashing algorithms are long and complex. Hashing all the possible passwords is a very time-intensive process. Rainbow tables use reduction algorithms (that are less computationally intensive) against password hashes. Essentially, Rainbow table programs are able to use the reduction function against the captured hash and compare it to other stored results of the reduction functions that were pre-computed and stored, and find much faster matches than using regular pre-computed hash tables.
Attackers can create their own rainbow tables (see http://www.rainbowcrack.com), download other people's tables (http://www.rainbowtables.shmoo.com), purchase them online, or even use an online rainbow table hash cracker (http://www.lasecwww.epfl.ch/~oechslin/projects/ophcrack). Password matches can often be made in seconds.
The side benefits of password cracking come from the fact that the password guessing is not done against an online database or against an active logon session. Hence, account lockout and event logging are not an issue. The hardest part of password cracking is obtaining the password hashes in the first place. As passwords get more complex or longer, they become increasingly resistant to password guessing and cracking.
Other Password Hacking Methods
Passwords can be compromised several other ways, including keylogging, shoulder-surfing, sniffing the network, replaying, man-in-the-middle (MitM), and social engineering. Keylogging involves placing a hardware device or a trojaned executable on a user's computer and then capturing the plain-text password as it is typed in. The captured password can then be stored in a local file and picked up by the hacker using another installed backdoor program, or sent to the hacker via IM or e-mail. A large percentage of malicious mobile code (for example, viruses, worms, Trojans, and so on) now include this functionality.
Passwords can be stolen simply by looking over the legitimate user's shoulder (referred to as shoulder surfing). Shoulder surfing is particularly useful in environments that use small passwords (for example, four-character PINs used with ATM and debit cards). Hackers have even installed hidden cameras at ATM locations to record users' PIN numbers.
The attacker can sniff the network to learn passwords or password hashes. Many protocols (for example, Telnet, FTP, POP, SMTP, and so on) will send passwords in plain text by default, with no effort made to obscure. Many password crackers, such as Cain & Able (mentioned previously), can sniff plaintext passwords or password hashes. In Figure 2-3, Cain & Able is displaying captured plain-text FTP passwords.
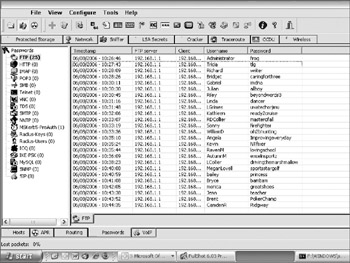
Figure 2-3: Plain-text FTP passwords caught by Cain & Able using network traffic eavesdropping techniques
It is the rare network that has very strong passwords used by all users throughout the environment. In one onsite penetration I was involved in, the password policy required long and complex passwords, and even biometric fingerprint readers for Windows logons. But a Microsoft SQL server's sa user (i.e., SQL system administrator) account had a blank password. After discovering the blank password, the author was able to take over the entire network within 15 minutes. So, even in networks requiring strong passwords, no one database holds all the logon credentials. It's hard for the defender to be perfect, but the attacker only needs to be persistent.
Sometimes the easiest way to get a password is just to ask the user. Often, with just a little bit of coaxing, end-users will give out their real passwords to complete strangers. Several studies have been done demonstrating that a large percentage of randomly chosen users will give out their real network passwords for a cheap gift, such as a $2 pen or a chocolate candy bar. Password attacks, whether guessed, cracked, or socially engineered, are one of the most popular types of attacks.
Buffer Overflow
Most applications and operating systems contain one or more buffer overflows. Attackers can discover them accidentally, or use buffer overflow finding programs (for example, static code review tools, fuzzers, and so on) as discussed in Chapter 1. Once a buffer overflow is discovered, it can be used by almost anyone with knowledge of the buffer overflow and access to a vulnerable service. A buffer overflow is normally exploitable from the time it is found until the vendor releases a patch, or the administrator takes some other offsetting steps (for example, IPS, turning service off, using alternate program, and so on).
Unfortunately, vendors are often slow to respond with patches and many users are slow to apply them even when available. It is not unusual for a vendor to take weeks to respond to a reported bug. To be fair, it might take weeks for a vendor to create and test a reliable patch. When the patch is released, most production environments have to regression test the patch before applying to make sure it doesn't break existing applications. In most cases, a mid-size or larger company might take one to two weeks to apply a new critical patch even if they are actively following vendor vulnerability announcements and testing patches. Some people and environments never install patches-ever! And until the software is patched, it is open season for attackers.
Buffer overflows often give the attacker remote access to the attacked computer within the security context of the program or service overflowed. Most Windows services run in the System context, which means a remote buffer overflow might give the attacker a highly privileged session. Once the buffer overflow is accomplished, most attackers "shovel a shell" back to their originating computer. The new command-line shell gives them a text-based logon session to the exploit computer. Then the attacker can contact the machine, upload and download files, and manipulate the victim computers however the attacker wants. Some buffer overflows create only denial of service (DoS) conditions, where the service is locked up or unavailable to legitimate users until the service is re-started.
Literally thousands of buffer overflow attack programs are available on the Internet. One of the most popular Web sites for downloading buffer overflows is http://www.milw0rm.com (see Figure 2-4). It contains buffer overflows for Windows, Linux, Unix, Solaris, and many other platforms.
Figure 2-4: Milw0rm Web site
Metasploit Framework
Many buffer overflow programs are ready to go, others you have to compile, and others are scripts just waiting to be launched. And today, buffer overflow attacks can be launched using a few clicks of the mouse. The Metasploit (http://www.metasploit.com) project has produced an easy-to-use vulnerability testing tool called the Metasploit Framework (http://www.metasploit.com/projects/Framework). It works with Windows, Linux, Unix, BSD, and Apple platforms.
| Note | If you decide to use Metasploit Framework, or any vulnerability testing tool, make sure you have the permission of the computer's owner. |
The Metasploit Framework (MSF) is a vulnerability testing environment, which comes with over 140 exploits and over 75 payloads (actions to take after the initial exploitation). MSF contains dozens of Windows exploits, and often buffer overflows will be included in the product within hours of a public exploit announcement. MFS comes in both command-line and GUI forms. The web-based GUI makes exploitation literally four clicks of the mouse (see Figure 2-5).
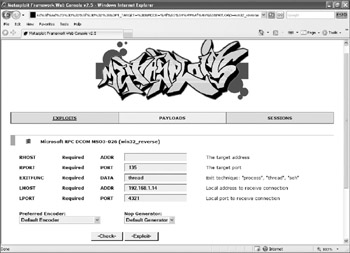
Figure 2-5: Metasploit Framework web interface
Buffer overflows can be used remotely (for remote control or DoS purposes) or locally for privilege escalation attacks. Suppose the attacker can get a local or remote logon, but only in the security context of a non-admin user. The attacker needs to get Administrator-or System-level security levels to make sure he has complete control of the exploited user and/or computer. Privilege escalation buffer overflow attacks allow the attacker to run one program and be immediately elevated to Administrator or System. If buffer overflows are possible, they are among the easiest methods to attack with. Just run the buffer overflow program and gain access. The best defense against buffer overflows is to make sure the OS and any installed applications are up-to-date with patches.
OS or Application Vulnerability
Even if the OS or application doesn't have a buffer overflow, they both can still contain bugs that allow unintended consequences that lead to new vulnerabilities. Vulnerabilities include:
-
Privilege escalation
-
Information disclosure Data malformation
-
Unintended consequences
There are many other types of vulnerabilities, but these are among the most common. The sections that follow will discuss each in a little more detail.
Privilege Escalation
Attackers often use vulnerabilities to gain a higher privilege level. Most applications run in the security context of the user, meaning that if an attacker takes over the application, they are limited to the security permissions and rights of the involved user. Malicious hackers have used hundreds of tricks to get to Administrator or system status.
A common example in Windows XP was for non-admin users to use the Task Scheduler (or At.exe command) to schedule a job to run the Cmd.exe command interactively. When the job ran, the interactive status would run it in the System context and a command-prompt session with full system access would be started.
Another common example involved opening up an application's help file. Although the application was running in a user's context, when the application's help file was opened, Windows opened the Windows Help application in the System context. Unsuspecting users would just see the displayed text file, but hackers would use the now opened help file to gain access to Cmd.exe with System access.
Another popular example is that of using one application's security features against another application. By default, non-admin users cannot change Internet Explorer's security settings. It was discovered, however, that if those same Internet security settings were accessed using older versions of Windows Media Player, they could be changed. Turns out that the Windows Media Player application accessed the Internet Explorer security settings using the System account instead of its own started privileges.
Information Disclosure
It is also common for error messages in applications to reveal too much information. It is not uncommon for web application errors to reveal the scripting language used, back-end database management system used, file names, directory paths, and more. Any of this information can be used by an attacker to gain more access and aid with social engineering situations. According to Secunia, 7 percent of all successful attacks against Windows XP Pro have been information disclosure attacks (http://www.secunia.com/product/22), and 18 percent of Mac OS X attacks (http://www.secunia.com/product/96). Programmers should take great care to make sure that application errors do not reveal too much information to unintended parties.
Data Malformation
All applications should treat all inputted data as untrusted. Inputted data should be checked for maliciousness, and abnormal data sanitized or dropped. Data malformation can interact with applications in strange ways, sometimes leading to a co-mingling of instructions in data fields, which the application then executes. Examples of data malformation co-mingling attacks include: SQL injection, cross-site scripting (XSS), and URL re-direction.
XSS attacks are very common. In an XSS attack, an innocent victim Web site or HTML-enabled service (for example, web-based e-mail) accepts as data input anything any user types and is able to render the typed in data as HTML code. A malicious attacker will type in or input scripted commands (usually Javascript) as data that then gets executed in the browser of any viewing user. The web application is expecting the user to type in text, but instead the malicious user types in scripting commands that get executed on other unsuspecting users.
In order to prevent XSS attacks, programmers must program their applications to check for, and remove, text that could incorrectly be executed as commands or scripts. For example, a web-based program can check user input for and remove </ anytime it appears. Those two symbols often precede embedded scripts.
Unintended Consequences
Software can be used in ways the vendor did not intend. Unfortunately, too many vendors don't use threat modeling to write more secure code, and even if threat modeling is used, not all the future misuses can be predicted. For example, ActiveX controls are compiled executables that can be distributed and executed using web-based browsers. When an ActiveX control is marked "safe for initialization" and "safe for scripting," it means the vendor feels the ActiveX control can't be used maliciously. ActiveX controls are frequently instructed by malicious commands to do something harmful to an exploited system.
For example, Symantec Norton Antivirus contained a control meant to be used by the application and Symantec tech support. Instead, hackers learned that anybody could call and use it (http://www.securityresponse.symantec.com/avcenter/security/Content/2004.05.20.html), and be able to launch applications and execute arbitrary code. Several other vendors allowed the same thing to happen, including HP (http://www.computerbytesman.com/acctroj/hp.htm) and Compaq (http://www.internetnews.com/dev-news/article.php/740501).
OS or Application Misconfiguration
Complexity is the antithesis of good computer security. It's easy for an administrator or end user to choose a single application configuration option and accidentally open up the computer to attack. For instance, when applying new permissions in Windows NT 4.0, it was common to get a dialog box asking if Windows was supposed to replace all files, folders, and child objects with the new permissions. In most cases, the answer probably should have been no, because doing so replaced all previous permissions with the new permissions, when the user often just meant to add one new permission. Microsoft realized that the interface was being misunderstood and re-designed the interface to prevent easy misconfiguration. Other common misconfiguration examples include:
-
Not changing vendor default passwords
-
Installing unnecessary software and services
-
Services that install themselves with too many security privileges
-
Remote logon console left unsecured
Although users are often at fault for these types of attacks, vendors can help by ensuring that healthy defaults are used. For instance, with earlier versions of Windows, Microsoft used to install IIS with every feature enabled even though most users did not intend to run a web server. Subsequently, early versions were exploited fairly frequently, often using features that only a minority of users would have ever intentionally installed. With IIS 6, Microsoft learned its lesson and didn't install it by default, and even when installed, it installs with a bare minimum of features. This strategy led to IIS 6 being proven as one of the most secure web server products every built.
Defenders can use vulnerability testing tools, such as open source Nessus (http://www.nessus.org), Metasploit Framework, or commercial products, like CORE IMPACT (http://www.coresecurity.com/products/coreimpact) to analyze and test their computer hosts before the malicious hackers do.
Eavesdropping/Man-in-the-Middle Attack
Hackers can capture and analyze network communications traffic, looking for passwords, password hashes, and program instructions. These types of attacks are most easily accomplished on local area networks (LANs), but can be accomplished anywhere the hacker can locate his network listening tool between the sender and the receiver.
One of the most common eavesdropping tools is Wireshark (http://www.wireshark.org), formerly known as Ethereal. It is a comprehensive, powerful, network sniffer and protocol analyzer. It is available for most platforms, including Windows, Linux, Unix, Mac, and BSD.
Many network eavesdropping tools can listen into traffic and automatically identify passwords and password hashes. Cain & Able (mentioned previously), LophtCrack (popular past commercial tool that is discontinued now), Ettercap (http://www.ettercap.sourceforge.net), and Dsniff (http://www.monkey.org/~dugsong/dsniff) are common sniffing tools that can easily identify passwords in network traffic. Kismet (http://www.kismetwireless.net) is one of many tools that can sniff WiFi wireless traffic.
If the attacker can listen in on traffic between two network nodes, he usually can also perform a man-in-the-middle (MitM) attack. Malicious hackers using a MitM attack can change the data sent and received between the two nodes. For instance, a MitM attack can be used to redirect a user away from their legitimate work Web site to a forged, look-alike, Web site. Many hacking tools, including Cain & Able and Ettercap, make this sort of attack trivial to accomplish on the local network. In Cain & Able, it literally takes only about 30 seconds to pull off a full-fledged MitM attack, with DNS redirection and data manipulation.
Denial of Service Attack
An attacker can cause harm without ever modifying or touching the intended victim. If the malicious hacker can bring down any network device between the legitimate customer and the intended server, it causes damage. At the very least, a DoS causes a local denial problem. Many of the vulnerabilities found in Internet Explorer are local denial of service attacks. The end-user is tricked into running a malicious file, and the file locks up Internet Explorer until the browser is restarted or the computer is rebooted.
An attacker can do the same thing remotely to a server. Early on, DoS attacks were created by overwhelming the target server with millions of illegitimate packets. Even if the packets are invalid, the server's processing time and memory can be taken up to an extent that it can no longer respond to legitimate traffic.
Often all it takes is one malformed network packet and the answering host gets immediately put into incredibly high constant CPU utilization or runs out of memory trying to handle the unusual event. In the past, it was found that sending a single unexpected ASCII character to a Microsoft SQL server port was able to DoS the entire server (http://www.ngssoftware.com/advisories/mssql-udp.txt).
Another common successful single packet attack against Microsoft TCP/IP stacks was the LAND attack. With LAND attacks, a malicious packet is sent to a server containing a source IP address and source port number that is identical to the destination host's IP address and port number. When XP Pro's IP stack was re-written to make it hardened against network DoS attacks, somehow, it became vulnerable (after years of not being) to the LAND attack. The same thing was found in the Vista beta 1 TCP/IP stack by Symantec (as mentioned in Chapter 1). I have also found Windows embedded devices, PDAs, and Microsoft-enabled IP TVs vulnerable to LAND attacks. Because LAND attacks have been around for over a decade and are programmatically easy to prevent, it is always surprising when Windows is still vulnerable to it.
Denial of service attacks are most troubling when they are able to be sent against a remote server and make it unresponsive to legitimate traffic. Local DoS attacks that lock up only a single application are less problematic. The offended user learns not to execute or launch whatever it was that caused the DoS in the first place. Still, any found DoS represents a legitimate bug and weakness in the application. Often DoS attacks are able to be elevated to buffer overflows, which can then be leveraged into a total malicious compromise.
Client-Side Attack
Client-side attacks generally involve tricking the end-user into running malicious code on their local workstation. The vast majority of malicious attacks today are client-side. If the end user can be tricked into running malicious code, no defense, no operating system, no application can be trusted to stop it-especially if the user is logged in as Administrator.
Common client-side attacks include:
-
Malicious e-mail attachments
-
Rogue Internet links
-
Malicious files sent via Instant Messaging
-
Games with embedded Trojan executables
-
Malformed multimedia files with malicious scripts and programs attached
This is the area that received the most attention from the Vista security development team. By default, even when end users are logged in as Administrator, they don't run with Administrator privileges and permissions. And if a program "escapes" out of an application, like Windows Mail or Internet Explorer, it will do so in low or medium integrity and have a hard time accessing the local system files.
Social Engineering
Client-side attacks are generally a form of social engineering, but this section refers strictly to cases where the malicious hacker sent no malicious code. They just asked for the unauthorized information, password, or access. One of my favorite social engineering stories is one I saw first hand when assisting a large university library system on the East Coast with hardening their computers against student maliciousness. While touring the library, the university host and I saw a bulletin board advertisement in the science hallway advertising a new IT support help desk phone number. At the time, I didn't think anything about it, and my host said nothing about it. A month later it was revealed to have been a student's dormitory phone number. He took calls night and day asking for the user's logon name and password to "assist" them. The student was able to collect hundreds of logon names and passwords in little over a month. When the former host called me to tell me about this social engineering attack, I asked why the host (a member of IT himself) didn't recognize that the new number wasn't a valid IT support phone number. The host replied that he often didn't know what was going on in IT and often found out about it through indirect means. He was delighted that they were getting student intern help.
Another common social engineering ploy the I use is to go to the company CEO's executive assistant and ask for the CEO's password. I introduce myself thus: "Hello, I'm Roger Grimes from XYZ Corp and I've been hired by IT to measure the password security of the company. I need the CEO's password." How often has it worked? Every time over the last 5 years.
Another common social engineering scheme is to leave "infected" media around the company. Many penetration testing companies have used this ploy. One left USB flash memory drives scattered through out a smoking area. My favorite is to leave a CD-ROM disc labeled "Pending 2007 Layoffs" in the IT or management area. The left media contains a proprietary "Trojan" that is not detected by any antivirus scanner, and "phones home" using port 443 using an SSL tunnel. Firewalls never stop it. IPSs, IDSs, and antivirus scanners never detect it. And certainly the end user and IT never detect it. When the media is run, it installs a remote access back door. If you allow your end users to install any software they want, then your company is also susceptible to this type of social engineering.
These types of maliciousness can be done by a dedicated manual attacker or using malware.
Dedicated Hacker Methodology
When most people think of hacking, they think of the dedicated human attack manually attacking a computer system. And while this still happens, it is important to realize that it constitutes a small minority of the malicious hacking activity in the world. But small doesn't mean not dangerous.
The dedicated hacker can take its time with the targeted network or computer. Hackers can change their techniques and payloads based upon newly learned information. Here are the traditional steps that a human attacker uses to exploit a system:
-
Scans for active IP addresses on intended victim host or network.
-
Fingerprints host operating systems.
-
Scans for and documents active listening TCP and UDP ports.
-
Enumerates each found TCP and UDP to determine what service is running.
-
Uses one of the eight methods listed in the previous section to compromise the victim host or network.
-
Hacker elevates their privileges to root, Administrator, or System, if they are not already in as such.
-
After successful exploitation, hacker copies additional hacking tools and hides their presence.
-
Hacker modifies victim system in a way to ensure they will be able to get back in.
-
Hacker steals information and/or sets up remote control mechanism.
-
Hacker pillages and plunders compromised system to find out more information on other hosts and networks (if desired).
-
Hacker then compromises additional hosts or networks (if desired).
For example, hacker scans an IP address range registered to an intended victim, and finds one or more active IP addresses. The hacker runs Nmap (http://www.insecure.org/nmap/index.html) or Xprobe2 (http://www.sys-security.com/index.php?page=xprobe) tools to identify the underlying victim host OS.
Nmap is used to map and identify the services running on listening TCP and UDP ports. Nmap finds TCP port 80 open, and running IIS 5. The attacker then uses one of eight previously mentioned exploitation techniques. For this example, let's assume they used an unpatched buffer overflow. The overflow gives the attacker local System access.
The hacker uses the local System access to copy up their hacking tools as a single, password-protected Zip file. The files are hidden in the \Windows \Font folder. A backdoor is installed. It is renamed Svchost.exe and uses stealth technology to hide.
The attacker uses its new system access to dump local service account passwords. One of the service accounts belongs to a popular backup tape vendor. The service is used to allow remote backups of workstations to the tape backup server. It is infrequently used, but installed on all computers in the Active Directory forest. The service runs in an Administrative context. The attacker uses the newly found service credentials to log on to a forest root domain controller that also functions as the PDC emulator (i.e., holds the master password table).
The hacker uses the admin-level credentials to dump all the password hashes of the Active Directory database. They then use John the Ripper to crack all the passwords. Dozens of new passwords are found. The attacker plants remote access Trojans all throughout the network, downloads confidential files, deletes mission critical files, and captures the personal logon banking credentials of several employees who used their work computers to check their online bank balances. The hacker also has several personal and corporate credit card numbers.
The hacker then uses the newly gained knowledge to break into other trusted partner networks. New customer accounts are stolen, business-to-business networks are exploited. Within a few days, the hacker has everything it needs. It erases any logs recording its activity and even password encrypts the tape backups using passwords not known by the company's IT staff. Then the hacker deletes all malware and all traces of its maliciousness. By the time the company even knows there is a problem, the hacker is gone.
This scenario, and ones similar to it, are played out hundreds to thousands of times each day. In truth, the dedicated hacker is difficult to defend against. A defender must be perfect; a dedicated attacker just needs to be patient. For example, a dedicated attacker can learn all the software that is running on a particular system, even what defense tools are used. Over the course of a year, the victim's network will need patching several times to prevent exploitation. When a new patch comes out, it can often take several days to two weeks before the patch is tested and deployed. During all that time, the attacker can be exploiting vulnerability. Even as dangerous as a dedicated attacker is, even more common is automated malware.
Automated Malware
Automated malware includes malicious mobile code of any kind, including: viruses, worms, Trojans, bots, spyware, and adware. There are many other types, and hybrids, but these are the main types.
Computer Virus
A computer virus is any program that modifies other legitimate host files or code in order to spread itself. Usually it modifies a file, adding itself to the host file in such a way that when the host file is run, the virus is also run. Viruses often go memory-resident and can infect any executable (or data type in the case of viruses, like macro and script viruses).
Computer viruses were very popular for nearly two decades, but became less successful when Microsoft introduced the Windows File Protection (WFP) in Windows ME and Windows 2000. With WFP, when any changes are made to protected executables, Windows replaces the modified copies immediately with a known good copy. This effectively prevented computer viruses, which must infect other host files to survive and spread, from being able to infect Windows system executables. While viruses could infect non-Microsoft files with system impunity, it made the job of spreading harder to do without being foiled and detected. Eventually, malicious coders decided to focus on malware types that did not need to modify other host files (or boot sectors) to survive.
Computer Worm
Computer worms are self-contained, self-replicating malicious programs. They do not directly modify other host programs or other legitimate coding to spread. Instead, they contain their own replication code and use the legitimate features (for example, e-mail, file shares) to spread.
Currently, computer worms are the most popular type of malware. Computer worms containing remote buffer overflows are responsible for the majority of the most popular attacks in the 21st century so far, as demonstrated by the Slammer SQL server and MS-Blaster worms. Slammer has the title of the fastest spreading worm so far: 90 percent of the possible hosts on the Internet were infected in 10 minutes (http://www.caida.org/publications/papers/2003/sapphire), but no security experts expect that record to go unchallenged in the future.
Trojan Horse Program
Trojan programs pretend to be one type of legitimate program, but instead contain malicious coding. The program the user is executing can be purely Trojan code (called a direct action trojan), or contain both a legitimate and illegitimate program. The user executes the Trojan file expecting to see another sort of program, utility, game, or multimedia content. The expected content is run along with the Trojan code. The user does not expect that a malicious program has been loaded, and will even kindly send it onto other friends and co-workers.
The key defining points of a Trojan are that it pretends to be another type of program, and that it has no self-replicating mechanism. It relies upon end users sending the program to each other to spread. Viruses, worms, bots, and other types of malware often masquerade as legitimate programs, meaning they have Trojan-like features as well. We call these sorts of programs, with multiple classifications, hybrid malware. For instance, an e-mail attachment arrives claiming to be a file the user was waiting for. The user installs it (i.e., it's a Trojan at this point). The Trojan installs a worm to spread via e-mail, and drops a computer virus just to add to the fun.
Bot
Bot is short for robot code, and used to be known as remote access Trojans (RATs) or zombies. Essentially a bot is a Trojan program that is able to take full control of a computer system. The initial compromise is done using a virus, worm, or Trojan. After the initial exploitation, it often contacts another compromised computer that is temporarily acting as a mothership web server. It is able locate the mothership server through a predefined DNS name that is temporarily hosted on a dynamic DNS server. Then the bot downloads either new instructions or a new program, and the process repeats multiple times (see Figure 2-6). At some point, the updating is considered completed, and the bot awaits instructions from its originating hacker. It may be instructed to act as spyware or adware, steal identity information, or be used in a massive distributed DoS (DDoS) attack.
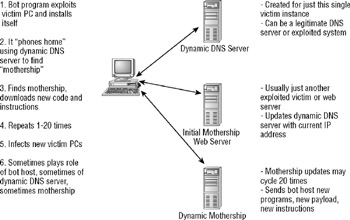
Figure 2-6: Bot phoning home
Bots are a large majority of the malware in use today. Their multiple download/updating scheme makes them very hard to track forensically. Many auto-delete themselves after successfully carrying off their missions.
Most bot hackers control tens of thousands of compromised computers in massive bot nets. Bot nets with over a hundred thousand, and even 1.5 million infected hosts are not rare. The hackers use the bot nets themselves in criminal enterprises or rent them out to other criminals. They literally advertise their available and offer 2-for-1 and first hour free sales.
Bots can be detected and removed just like any other malware threat, but their massive sizes often make them easier to detect and remove by the carrier network hosts and ISPs. There are even commercial solutions available to detect and remove bot networks, including products from http://www.simplicita.com.
Spyware
Spyware monitors and records a user's computer activity. It comes in two forms. One form targets the authorized monitoring market, such as parents monitoring children's Internet activities, employers monitoring employees, and spurned spouses monitoring adulterous loved ones (the last category is often not legal). This class of software often installs itself directly on the host computer it is monitoring, and then records every logged in user's keystrokes, e-mails, and chats. The most popular software vendor in this category is Spectorsoft (http://www.spectorsoft.com).
The more worrisome spyware category is one where the spyware is installed without any user's approval by an unknown, unauthorized third party. Spyware is often used by criminals to record users' identity information, passwords, credit card information, and banking information. The vast majority of malware programs are used for criminal intent. See http://www.symantec.com/enterprise/threatreport/index.jsp for more detail.
Adware
Compared to the other forms of malware, adware almost seems harmless. Adware installs itself through the normal mechanisms (virus, worm, Trojan, and so on) and then records the Internet sites and content a user visits, or goes even further to redirect (without authorization) the user to other Internet locations. Adware normally modifies Internet Explorer, but can also maliciously manipulate DNS client services.
Adware makes its money by getting people to visit sponsored Web sites and advertisers. The adware hacker usually make up to ten cents per every sponsored visit. By installing the adware on multiple computers (much like a bot net), the adware hacker makes money. In most cases, the infected user isn't maliciously harmed, other than being re-directed away from other legitimate sites they may want to visit and being redirected to sites they would not ordinarily visit.
And it's not just that adware vendors are criminals hiding in the dark reaches of the Internet. Many adware programs are unknowingly sponsored by the world's biggest Web sites (for example, Google, Nike, Yahoo, and so on) and adware venders are multi-million dollar companies getting millions of dollars of venture capital money. The adware vendor maintains just enough plausible deniability that it takes the legal authorities years to catch them. The legitimate companies that use the adware services don't realize they are dealing with adware vendors. They think they are dealing with a legitimate advertising firm (and many are).
There are many other types of malware, such as rootkits, which hide from forensic investigators, but most malware can be classified as one of the types just mentioned. It is also important to note that dedicated hackers often use automated malware to find their next victims. They let the automated program do the grunt work of the initial exploitation, which then contacts the hacker, who continues a more intelligent attack.
EAN: N/A
Pages: 163