Analysis, Debugging, and Reverse-Engineering Tools
No hacker or virus writer can resist the temptation of investigating ideas and algorithms implemented in the bodies of viruses added to his personal collection. Most frequently, they exchange viruses privately. Collections that can be found on the Internet are of little or no interest to experienced hackers. This is because such collections, as a rule, are formed on the basis of open sources. Nevertheless, for beginners such collections are a true Klondike.
If there is no source code available (crippled disassembled listings must not be considered as afflatus or relied upon), then it is necessary to grind binary code manually. At this point, there is one of the main pitfalls waiting for the hacker. The best disassembler available at all times ” IDA Pro ” is not suited for working with ELF files because it refuses to load files with corrupted section header, and most viruses never correct it after infection.
| Note | In newer versions of IDA Pro, this bug has been fixed. |
I didn't discover any worthy disassembler that would correctly process the ELF format. Therefore, the hacker will have to either spend time and effort writing such a disassembler or, lacking better ideas, use hex editors, such as HIEW, to study the auxiliary structure of the file manually.
The situation with debuggers is even worse . Under UNIX, there is only one more or less worthy application-level debugger ” the GNU Debugger (GDB). This debugger is the foundation for most other ones. Even the simplest antide-bugging techniques, which can be found in hacker's manuals from when MS-DOS prevailed, either blind GDB or allow the code being debugged to break loose from its control. Just imagine what would happen if the code being studied under the debugger was a destructive virus! Therefore, it is intolerable to debug shellcode on a working computer. The best practice in this case is to use some emulator for this purpose.
Emulators equipped with a built-in debugger are the best choice in this case. For the code being investigated with the debugger, it will be especially difficult, if even possible, to bypass such a debugger. In an ideal case, this will be practically impossible . A good example is the Bochs emulator. Bochs is a high-quality PC emulator with an integrated debugger, one extremely well suited for experiment with viruses directly on a working PC without risking information destruction. Bochs is freeware distributed with the source code. It can be downloaded from http://bochs. sourceforge .net and contains such a debugger (Fig. 1.6). By the way, it is not necessary to install UNIX to study ELF viruses. An emulator is enough to achieve this goal (Fig. 1.7).
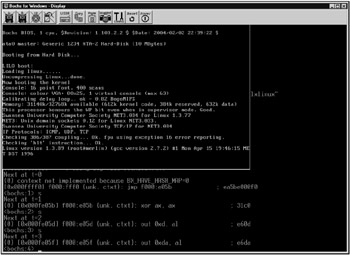
Figure 1.6: Debugging a virus using the integrated debugger of the Bochs emulator started under Windows 2000
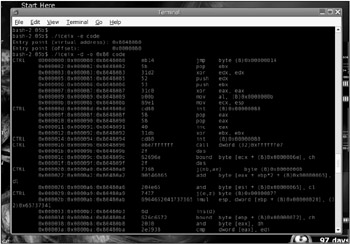
Figure 1.7: Investigating the behavior of UNIX viruses using the Iceix disassembler
EAN: 2147483647
Pages: 164