Chapter 13: Playing Hide-and-Seek Under Linux
Overview
In this chapter, you'll learn how to hide your files, processes, and network connections under Linux-like operating systems with kernels version 2.4 to 2.6. This chapter is not a manual on configuring Adore; these are plentiful on the Internet. Rather, this is a tutorial for creating custom rootkits that are cooler and more reliable than Adore and Knark taken together.
Penetrating the target machine is only a part of the attacker's goal. After that, attackers must hide their files, processes, and network connections; otherwise , system administrators will remove them. For this purpose, there are lots of root-kits ” Adore (Fig. 13.1), Knark, and other similar tools ” widely available on the Internet (note, however, that not each of them is usable). Furthermore, however intricate the widely used rootkit might be, there are specialized tools developed for neutralizing it.
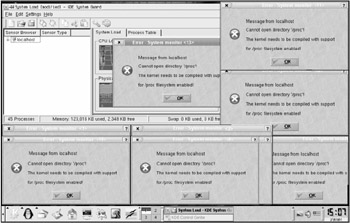
Figure 13.1: Consequences of starting Adore 0.42 under Knoppix 3.7 LiveCD
True hackers differ from their imitators in that they develop all required tools on their own, or at least adapt existing tools for specific purposes. This chapter describes how to do this.
EAN: 2147483647
Pages: 164