Chapter 3: Hacking Using GPRS Uncovered
The season of hunting for hackers is at its height. Hackers are wanted by the police and intelligence services of practically all countries . If some individual releases warez, disassembles programs, cracks protection mechanisms, writes viruses, or attacks networks, then it is possible that this person will land first in court and then in jail. To remain free, hackers try to protect themselves . Among hackers, attacks that use General Packet Radio Services (GPRS) have become popular. For this purpose, they need a phone supporting GPRS protocol, soldering iron, disassembler and, finally, intellect.
Why Using Anonymous Is Not Safe
Any criminal investigation begins with traditional questions: Who might benefit from the results of this crime, and who might commit it? Many hackers are caught because they like to leave text strings (so called graffiti ) specifying their nick, native city, or other revealing information. This considerably narrows the range of suspects . Intelligence services only need to check the computing community. Real hackers are few in number, and practically everyone knows them. This is the inevitable payment for fame and publicity.
Only those hackers survive in this cruel world who, to be on safe side, isolate themselves from the outer world, reduce social contacts to the minimum, and hide in a lonely den and enjoy hacking. The main source of information that can disclose an attacker is the IP address. From the standpoint of networking protocols, this is simply a 32-bit number in the packet header, which is easy to forge or corrupt. However, no practical advantages will be achieved by doing so. A packet with an incorrect IP address will be discarded at the first router encountered . Even if such packet is not discarded, the sender won't receive any reply and, consequently, won't be able to establish a transmission control protocol (TCP) connection.
The simplest way of ensuring anonymity is using a proxy server located in a Third World country. Such servers are numerous ; however, not all of them are anonymous. There are lots of services that check the proxies you are currently using. In my opinion, the best one is http://www.showmyip.com (Fig. 3.1). A brief list of proxy-checking services is provided here:
-
http://www.showmyip.com . As was already mentioned, this is the best service for checking anonymous proxies. It provides as much information as is possible to collect and automatically refers to the map, provided that the geographic region was detected .
-
http://www.leader.ru/secure/who.html . This is a powerful service for testing proxies. It determines the IP address, domain name , browser type, operating system version, preferred mail server, etc. It has no promo or advertisements and minimum graphics.
-
http://checkip.dyndns.org . This service displays only the IP address of the remote host. It doesn't display advertisements and graphics.
-
http://www.ipcheck.de . This service reports the IP address, domain name, and browser type. There are lots of graphics here.
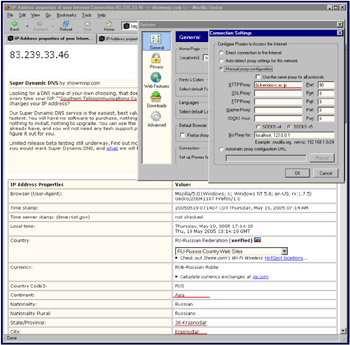
Figure 3.1: The http://www.showmyip.com proxy-checking service displays as much information as is possible to collect
As a rule, even if the chosen proxy successfully hides the hacker's IP, and tries to conceal the continent , the proxy checker detects the city of residence, name of the user 's ISP, and even the time zone. By the way, time zones are determined using Java scripts, and the proxy has no relation to it. Therefore, the first thing that a clever hacker will do is changing the server and disabling the scripts. However, even if the proxy appears quite trustworthy, it might stealthily collect the traffic and provide that information at the request of the intelligence services. According to rumors, the fastest anonymous proxies belong to intelligence services. However, even this is not the essence of problem. Everyone can install a legal proxy that would be guaranteed not to collect any information about the users and share this with the others. This is typical for educational institutions, universities, and noncommercial organizations that do not pay for their traffic. However, there is no guarantee that information about incoming and outgoing connections is not collected by the ISP or communications carrier. As practice has shown, most ISPs collect such information and store the logs for several days or even weeks.
If the hacker is going to deface someone's home page, then it might be enough to have a good proxy server to achieve this goal. A good example of such a proxy is http://www.triumphpc.com/proxy-server ” an excellent anonymous proxy server that automatically disables scripts and blocks cookies. Unfortunately, this is not a fully featured HTTP proxy but an online service. Therefore, secure shell (SSH) won't operate using it. Nevertheless, it is still suitable for a hacker's goals. The main concern of the hacker is ensuring that no personal information is left on the attacked host. As a rule, intelligence services will not investigate proxy logs because doing so is such a trifling affair. In more serious cases, however, using a proxy is not enough; therefore, hackers try to find other ways of achieving their goals.
One possible approach is building a chain of anonymous proxies. This can be done using special programs, such as Secret Surfer (Fig. 3.2).
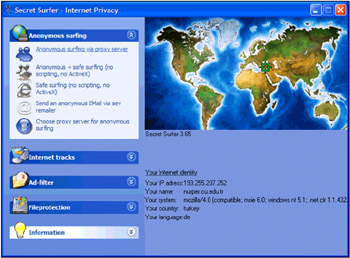
Figure 3.2: The Secret Surfer program automatically builds a chain of anonymous proxies
The more servers included in the chain, the safer the hacker's positions . However, the risk of being caught remains high. Who can guarantee that the first server in the chain doesn't belong to the FBI?
EAN: 2147483647
Pages: 164
- Command Reference
- Carrier Supporting Carriers Overview
- L2TPv3 Overview
- Implementing Layer 3 VPNs over L2TPv3 Tunnels
- Case Study 2: Implementing Multi-VRF CE, VRF Selection Using Source IP Address, VRF Selection Using Policy-Based Routing, NAT and HSRP Support in MPLS VPN, and Multicast VPN Support over Multi-VRF CE