Penetrating the Firewall
Only the best-quality firewalls support the assembly of fragmented TCP packets. All other firewalls analyze only the first fragment and let the other fragments pass without obstacles. By sending a strongly-fragmented TCP packet, in which the TCP header is spread over several IP packets (Fig. 23.6), the hacker can hide the acknowledgment number from the firewall. Consequently, the firewall won't be able to determine whether the TCP packet belongs to the TCP session that corresponds to it (the packet might or might not belong to a legal connection established by one of the corporate users). If the Discard fragmented packets option is not set on the firewall, then the success of the hacker attack by fragmented traffic is practically guaranteed . Blocking fragmented packets creates lots of problems and obstacles for the normal operation of the network. In theory, it is possible to block only packets with fragmented TCP header; however, not every firewall supports such a flexible configuration policy. Attacks of this type, also known as tiny-fragment attacks , are powerful and represent the favorite technique of intruders.
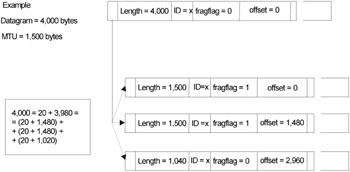
Figure 23.6: Fragmentation of TCP packets as method of bypassing firewalls
Attacks that use source routing are considerably less important; nevertheless, they will also be covered in detail. IP allows a hacker to include information about routing in the packet. When the IP packet is sent to the target computer, the routing information forged by the hacker most often is ignored and the path , along which the packet travels to the destination, is determined exclusively by intermediate routers. However, the reply packets are returned along the route specified in the IP header, which creates favorable conditions for replacing it with a fictitious one. A simplified variant of the attack is limited only to the replacement of the sender IP address. In this case, the attacker sends a packet on behalf of one of the internal hosts . Expertly configured routers, as well as most UNIX clones , block the packets containing source routing information. Packets with fictitious IP addresses are a more serious problem; however, high-quality firewalls allow you to block these.
Routing tables can be dynamically changed by sending an ICMP Redirect message, thus allowing (at least, in theory) the hacker's traffic to be directed along the route bypassing the firewall (see also the section on ARP spoofing in Chapter 27 ). However, such hopelessly unprotected systems are never encountered nowadays.
Here are some facts about firewalls:
-
Firewalls are vulnerable to a large number of various DoS attacks, such as Echo flood or SYN flood, that they are principally unable to withstand.
-
Firewalls combine the functions of routers, proxy servers, and intrusion detection systems.
-
Firewalls do not ensure full protection against attack. Figuratively, they only surround the perimeter of the internal network with an analogue of a brick wall, which intruders "climb over" if desired.
-
In most cases, the firewall can be bypassed using ICMP tunnels by wrapping the data being transmitted in an ICMP header.
-
Firewall can be attacked from the outside and from the inside of the protected corporate network.
-
Different firewalls react differently to nonstandard TCP packets, thus disclosing their presence.
-
Firewalls that open port 53 (the DNS service) not only at the destination but also at the source (Check Point Firewall, for example) allow hackers to scan the entire internal network.
-
In general, the vulnerability of software proxies is not too significant. As a rule, they are attacked using buffer overflow errors.
-
Some firewalls are vulnerable to unauthorized file viewing using port 8010 and requests such as http://www.hostcom::8010/c:/ or http://www.host.com::8010// .
-
The DCOM service relies on a range of opened ports, which considerably reduces the security level of the system, neutralizing firewalls.
EAN: 2147483647
Pages: 164