8.1 Managing Users
There are actually three different User Accounts dialogs in Windows XP, each with a different design and "intended audience," so to speak. The problem is that each window has a few options not found in the other, so no single window can be used exclusively to handle all tasks.
- User Accounts
-
The primary user accounts interface, accessible by going to Control Panel
 User Accounts and shown in Figure 8-1, is the one that most users see. It's large, friendly, and unfortunately, somewhat cumbersome. But, given the "administrator" stigma behind user accounts, it's not surprising that Microsoft has gone to great lengths (some feel too far) to make this window less intimidating and easier to use than its counterparts in earlier versions of Windows.
User Accounts and shown in Figure 8-1, is the one that most users see. It's large, friendly, and unfortunately, somewhat cumbersome. But, given the "administrator" stigma behind user accounts, it's not surprising that Microsoft has gone to great lengths (some feel too far) to make this window less intimidating and easier to use than its counterparts in earlier versions of Windows. Figure 8-1. You can add, delete, or modify user accounts in the User Accounts dialog, but not much else.
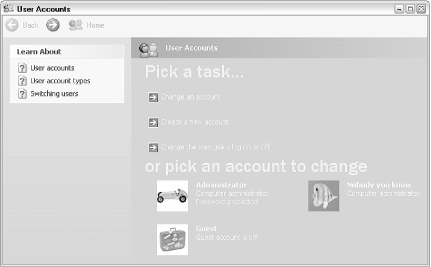
Adding, customizing, and removing user accounts is extremely easy, and for the most part, self-explanatory in this window, and that is admirable. But sometimes you'll need one of the alternate dialogs, listed below, to accomplish some of the more advanced tasks, such as managing groups and configuring Windows to log in a password-protected account automatically.
Avoiding .NET Passport Accounts
Littered throughout the operating system are various links and tie-ins to Microsoft's .NET online service. It seems as though no matter where you turn, there's another button that suggests that you need to sign up for a .NET "passport" in order to use the feature.
The point is to try to make .NET passports seem as ubiquitous as the My Documents folder, so that customers will feel more comfortable using the service. That way, Microsoft can try to push its MSN online service and much-hyped .NET technology onto other companies, so that soon, any Web site you visit and every program you start will require a .NET passport password.
Fortunately, we haven't reached that stage yet. In fact, the only component in Windows XP that absolutely requires a .NET passport is Windows Messenger. In all other cases, signing up for MSN or .NET is purely optional, despite what the instructions in the dialog may suggest.
Note that this window is the only place you can choose a user's picture, shown in both the login dialog and at the top of the new-style Start Menu (discussed in Chapter 2). The primary User Accounts dialog is also the only place you can choose between the Welcome Screen and the standard Login screen, as discussed in Section 8.1.3, later in this chapter.
- User Accounts 2
-
Some additional settings, discussed later in this chapter, can be changed only with the alternate User Accounts window, which, incidentally, is identical to the one found in Windows 2000. To open the old-style User Accounts dialog, select Run from the Start Menu, type control userpasswords2, and click OK. This dialog is shown in Figure 8-2.
Figure 8-2. The "other" User Accounts dialog can do many things otherwise impossible in the standard User Accounts window.
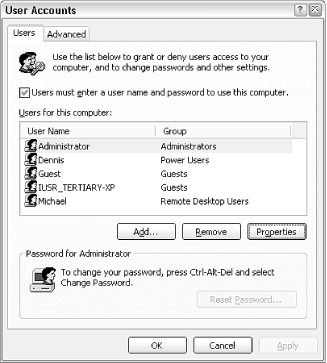
Like the primary User Accounts window, you can add new users, as well as rename or remove existing accounts. But here, you have more control over a user's permissions and restrictions. You can access accounts that would otherwise be hidden in the User Accounts window, such as the Administrator account (see Section 8.1.7, later in this chapter) and the IUSR account used by the IIS web server. See Section 8.1.3, also later in this chapter, for another use of this dialog.

Use the alternate User Accounts dialog and the Local Users and Groups window with caution, as both allow you to disable all accounts with administrator privileges. If this happens, the computer will be completely inaccessible by any administrator, and you'll probably have to reinstall just to log in.
- Local Users and Groups
-
The third way to manage user accounts in Windows is to use the Local Users and Groups policy editor (lusrmgr.msc), shown in Figure 8-3. The Local Users and Groups window (LUaG) is actually a Microsoft Management Console (mmc.exe) snap-in, like the Disk Management utility (see Chapter 5), and therefore can be accessed remotely if necessary. Figure 8-3 shows the LUaG dialog in all its glory.
Figure 8-3. The Local Users and Groups window gives you the most control over user accounts, but at the expense of a rather sparse and intimidating Registry Editor-like interface.
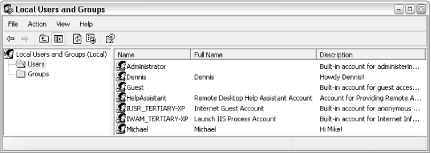
LUaG is where you'll want to do go to manage groups, set the automatic expiration of passwords, and change the location of a user's home directory. Just double-click any entry in the Users or Groups categories to change their properties. Or, right-click in an empty area of the right pane to add a new user or group.
Groups can be useful when you have a bunch of users. For example, say you wish to make a folder accessible to several users (as described later in this chapter); instead of having to specify each one individually, all you would need to do is specify the group. Note that once the group has been set up here, you can use the User Accounts 2 dialog (earlier) to assign new or existing members to that group.
What can be confusing is finding the right place to accomplish a specific task regarding user accounts. Table 8-1 shows a bunch of different tasks and where to go to accomplish them.
| Task | User Accounts | User Accounts 2 | Local Users and Groups |
|---|---|---|---|
| Add groups | | ||
| Add users | | | |
| Assign a user to a group | | | |
| Assign a user to multiple groups | | ||
| Change a user's description | | | |
| Change a user's home folder | | ||
| Change a user's password | | | |
| Change a user's picture | | ||
| Choose a logon script | | ||
| Disable a user or group account | | ||
| Manage network passwords | | | |
| Modify groups | | ||
| Prevent forgotten passwords | | ||
| Remove almost any user | | | |
| Remove any user | | | |
| Rename a user | | | |
| Require Ctrl-Alt-Del to log on | | ||
| Set password expiration | | ||
| Turn off login window | | ||
| Turn off welcome screen | | ||
| Use Fast User Switching | | ||
| View members of groups | |
For the most part, adding, removing, and modifying user accounts is a fairly self-explanatory process, so I won't go into every excruciating detail here. Here are some tips for working with user accounts:
-
Press Ctrl-Alt-Del and then click Change Password to change your own password. This is the only way to change the password of an account when you're not an administrator.
-
If you have a lot of users coming and going, use the Local Users and Groups window to have passwords automatically expire. This not only forces users to change their own passwords regularly, but automatically blocks users who haven't logged in a while.
Security Identifiers (SIDs)Every user on your machine has a unique Security Identifier (SID), which is used in conjunction with most of the features discussed in this chapter, such as permissions and encryption, as well as some of the solutions in other chapters in this book. For example, your personal settings in the Registry (Chapter 3) are stored in a branch that looks something like this: HKEY_USERS\S-1-5-21-1727987266-1036259444-725315541-500 The numeric portion is your SID, and is composed of the following elements: S-r-i-sa-xxxxxxxxxx-yyyyyyyyyy-zzzzzzzzz-uid where S stands for security identifier, r is the revision level and is always set to 1, i is the identifier authority, and sa-xxxxxxxxxx-yyyyyyyyyy-zzzzzzzzz, is the sub-authority. Finally, uid, is the user id. For example, the identifier authority (i) can tell you something about the type of user to which an SID corresponds:
Aside from some of the solutions that use SIDs, they can be an issue if you clone your machine, at which time you may have to change your SID. Microsoft's System Preparation Tool (SysPrep) can be used to do this. |
8.1.1 Understanding Permissions
Setting the permissions for a file or folder allows you to permit access to some users while restricting access to others.
Before you start messing with permissions, you'll need to turn off Simple File Sharing. Go to Control Panel ![]() Folder Options
Folder Options ![]() View tab, and turn off the Use simple file sharing option. Click OK when you're done.
View tab, and turn off the Use simple file sharing option. Click OK when you're done.
Note that permissions can only be used on files and folders stored on NTFS volumes (see the discussion of NTFS in Chapter 5).
8.1.1.1 Setting permissions for an object
By default, everyone on your computer has access to every file on your hard disk. In order to restrict access, you'll have to change the permissions for your folders, files, and drives that contain more sensitive data. It gets a little confusing when you realize that there are two different Permissions windows for any given object (file, folder, printer, etc.).
- Object permissions
-
Right-click any file, folder, drive, or printer, select Properties, and choose the Security tab to view or change the permissions for the selected object(s). These settings affect how the object is accessed by users on your machine.
- Share permissions
-
Right-click any file, folder, drive, or printer, select Properties, choose the Sharing tab, and click Permissions to view or change the share permissions for the selected object(s). These settings affect how the object is accessed by users on other machines on your network. Note that the Permissions button will only be available for objects currently shared on your network. See Section 8.2.3, later in this chapter, for more information on sharing resources.
|
Fortunately, all Permissions windows look and work the same; the only difference is their scope. Figure 8-4 shows a typical Permissions window.
Figure 8-4. The standard Permissions window allows you to permit or deny access to other users on your computer or in your workgroup.
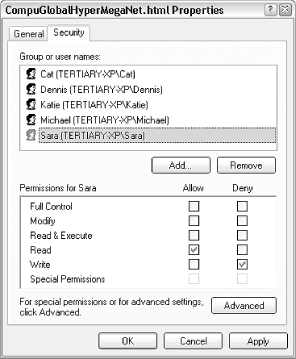
Typically, a single entry, "Everyone," will appear at the top of the list. In the example in Figure 8-4, only five single users are shown here. Any user not in the list will not be allowed to view or modify the object.
Select any user in the list, and then use the checkboxes in the list below to modify the permissions for that user. In this example, the user named Sara is allowed to read the selected file, but not allowed to write to it. Although this window only shows the permissions for one user or group at a time, you can click Advanced to see a better overview, as shown in Figure 8-5.
Figure 8-5. Open the Advanced Security Settings window to see all users and permissions for an object at once.
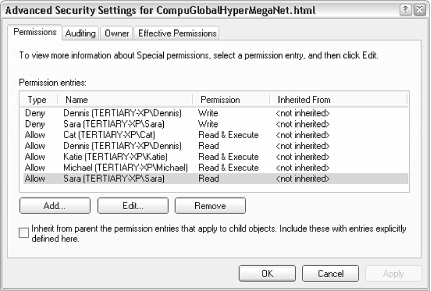
In some cases, when you attempt to remove or modify permissions in the standard Permissions window (Figure 8-4), Windows will complain about the fact that the object is inheriting permissions. The reason is the Inherit from parent option in the Advanced Security Settings dialog (Figure 8-5).
8.1.1.2 Inheritance and other advanced options
Inheritance can be confusing at first, but it does save time in the long run. Essentially, if you set the permissions of a folder, those permissions will propagate to all of the files and subfolders contained therein (although Windows will usually ask you whether or not you want this to happen). When the permissions for a "parent" folder propagate to a "child" folder or file, that child object is said to "inherit" the permissions of its parent folder. Furthermore, these permissions are locked, at least until you turn off the aforementioned Inherit from parent option.
The Auditing tab in the Advanced Security Settings window allows you to log access activity relating to the selected object. Before Auditing will work, you'll need to set up an Auditing policy by opening the Group Policy window (gpedit.msc). Then, navigate to Computer Configuration\Windows Settings\Security Settings\Local Policies\Audit Policy. Then, open the Event Viewer (eventvwr.msc) to view the corresponding logs. Note that settings in the Auditing tab obey inheritance like Permissions, discussed earlier.
The Owner tab is used to assume ownership of one or more objects. I use this option most when I have a dual-boot system (see Chapter 10), and I have to access files that were placed on the hard disk by the other operating system. In most cases, Windows won't let you access such files until you "take ownership" using the Owner tab of this window.
8.1.1.3 Adding new users to the Permissions window
Typically, a single entry, "Everyone," will appear at the top of the Group or user names list in the Permissions window. More than likely, though, you'll want to eliminate the "Everyone" entry and add only those users and groups to which you need to specifically grant access.
Start by deleting any unwanted users by selecting them and clicking Remove. Then, click Add to add new users and groups. The Select Users or Groups window appears, as shown in Figure 8-6.
Figure 8-6. New users and groups are added to a Permissions list with this rather confusing dialog.
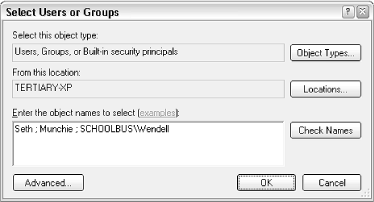
Most users visiting this dialog for the first time will expect a list of the users on their machine; unfortunately, such a list isn't here. Instead, you'll have to type the name(s) of the users and groups you wish to add in the Enter the object names to select field. If you enter more than one user, simply separate them with semicolons.
In the example in Figure 8-6, you'll notice that the third entry, SCHOOLBUS\Wendell, is unlike the others. While "Seth" and "Munchie" are users on the machine (or in the domain to which the machine belongs), the third entry shows how a user on a different machine is specified; in this case, the user "Wendell" on the computer SCHOOLBUS is to be added.
So, why aren't user and group names listed here? The reason is that this dialog has been designed to accommodate a single computer with two users, as well as a company-wide network with thousands of users, and everything in between. Naturally, you can always open the User Accounts window to look up the users on the local machine. Or, if you're part of a Windows domain, you can click Advanced to search for users on your network.
When you click OK, Windows will verify the user and group names you've entered, and if all is well, will add them to the Permissions window. You can also click Check Names here to verify your entries without closing the window.
When a new user has been added to the Permissions window (Figure 8-4), highlight the user or group name, and selectively click the checkmarks in the Allow or Deny columns. Note that Deny entries take precedence over Allow entries.
Depending on the type of object you've selected, you may see any number of different types of entries here, such as Full Control, Read, Write and Modify. After playing with the checkmarks, you'll notice that there is quite a bit of redundancy in this list; for example, Modify is an umbrella term that includes Read & Execute, Read, and Write.
For more control over permissions, click Advanced to show the Advanced Security Settings window (Figure 8-5), select the user, and click Edit. The Permission Entry window, shown in Figure 8-7, will allow you to fine-tune permissions and allow only those permissions that are absolutely necessary for the object.
Figure 8-7. The Permission Entry window lets you fine-tune permissions.
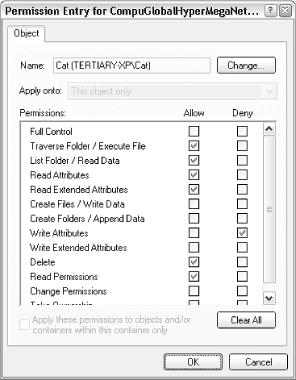
When you're done choosing permissions, click OK. If you're modifying the permissions for a folder, Windows may or may not prompt you to have your changes propagated to all subfolders and files.
8.1.1.4 Notes
-
In most cases, you'll want to set permissions to protect your files and folders from unauthorized access. But some permissions are necessary to get some programs to work.
For example, if you're writing a CGI or ASP program for the IIS web server (see Chapter 9), you'll need to set the permissions of your files to give the Internet Guest Account full access. The Internet Guest Account user account name is based on the machine name: for a system named SERVER, you'd enter SERVER\IUSR_SERVER into the Select Users or Groups dialog (Figure 8-6).
-
For better security, Windows XP Professional supports encryption, a feature used in conjunction with permissions. See Section 8.1.2, later in this chapter, for details.
-
Permissions protect files from other user accounts only. If you walk away from your computer while it's logged into your account, for example, someone else sitting down at your computer will have full access to all your files, regardless of permissions or even encryption.
8.1.2 Protecting Your Files with Encryption
Encryption effectively adds another layer of protection for your especially sensitive data, ensuring that a file can only be viewed by it's creator. If any other user even someone with administrator privileges attempts to view the file, they will see only gibberish.
When a file is marked for encryption, the encryption and decryption of the file are handled by Windows invisibly in the background when its creator writes and views the file, respectively. The problem is that Windows XP's on-the-fly encryption can be somewhat unpredictable, and security is one place where you don't want there to be any guesswork.
Note that encryption can only be used on NTFS volumes, as described in Section 8.1.2.1, which follows.
8.1.2.1 Encrypting files
Explorer has an option to visually differentiate encrypted files, which can be very handy, especially for those getting started with encryption. Start by going to Control Panel ![]() Folder Options
Folder Options ![]() View tab, and turn on the Show encrypted or compressed NTFS files in color option. Click OK when you're done.
View tab, and turn on the Show encrypted or compressed NTFS files in color option. Click OK when you're done.
Encrypted files appear in green, and compressed files appear in blue (except for icons on the Desktop). If you wish to change these colors, open TweakUI (see Appendix A), and select Colors in the Explorer category.
Here's how to encrypt a file:
-
Right-click one or more files in Explorer and select Properties.
-
Click Advanced in the General tab.
-
Turn on the Encrypt contents to secure data option, click OK, and click OK again.
After a file has been encrypted, you can continue to use it normally. You'll never have to manually decrypt an encrypted file in order to view it. But if you want other users on your machine (or network) to be able to view the file, you'll have to turn off encryption; just reverse the above procedure to do so.
See "Add Encrypt/Decript commands to context menus," later in this section, for a quicker way to encrypt and decript files.
8.1.2.2 Encrypting folders
You can also encrypt a folder and all of its contents using the same procedure for files shown earlier. Where it gets complicated, however, when you try to predict what happens to the folders contents, before and after you encrypt the folder. Here are some tips to help you understand the process:
-
If you encrypt a folder that contains files or other folders, Windows will ask you whether or not you want to those contents to be encrypted as well.
-
If a file contained in an encrypted folder is moved into an unencrypted folder, the file will become unencrypted. The exception is when you've specifically encrypted a single file; in this case, the file will remain encrypted, no matter where you put it.
-
If an unencrypted file is placed in an encrypted folder, the file will become encrypted. The catch is when one user has encrypted a folder and another user places a file in that folder; in this case, the file is encrypted for the creator of the file, which means that the owner of the folder, the one who originally implemented the encryption, will not be able to read it.
On the other hand, if the user places a file in a folder, and a different user comes along and encrypts the folder, only the user who implemented the encryption will be able to subsequently read the file, even though the file is technically owned by a different user.
8.1.2.3 Encryption tips
Here are some tips for working with encrypted files and folders:
-
Not even administrators can view files encrypted by other users. However, an administrator can change any user's password, and then subsequently log in to that user's account and view any files encrypted by that user.
The exception to this is what happens when the aforementioned user deletes his or her encryption keys. In this case, neither the user nor any administrator will be able to read the encrypted files until the key is reinstalled. See the discussion of the NTFS Encryption Utility, later, for more information.
-
Encrypting a file may not guarantee that it remains encrypted forever. For example, some applications, when editing and saving files, will delete the original file and then re-create it in the same place. If the application is unaware of the encryption, then it will be lost. The workaround is to encrypt the folder containing the file, rather than the file itself.
-
If you change the ownership of a file, as described in Section 8.1.1, earlier in this chapter, and the file is encrypted, the encryption will remain active for the original owner and creator of the file, even though that user no longer technically "owns" the file.
-
Since all users need to access files in certain folders, such as the \Windows and \Windows\System folders, Windows won't let you encrypt files and system folders or the root directories of any drives.
-
Encryption is a feature of the NTFS file system (discussed in Chapter 5) and is not available with any other file system. This means that if you copy an encrypted file onto, say, a floppy disk, CD, or other removable media, the file will become unencrypted, since none of these drives support NTFS.
-
Compression is another feature of the NTFS file system, which simply reduces the amount of space consumed by a file or folder. The rules apply to compression are the same as those that apply to encryption, earlier. Note that you cannot simultaneously use encryption and compression on any object; turn on one option in the Properties window, and the other will be turned off.
8.1.2.4 Add Encrypt/Decript commands to context menus
If you find yourself frequently encrypting and decrypting files, having to repeatedly open the Properties window can be a pain. Instead, use this next solution to add Encrypt and Decrypt commands to the context menus for every file and folder.
-
Open the Registry Editor (discussed in Chapter 3).
-
Expand the branches to: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced.
-
Create a new value by going to Edit
 New
New  DWORD Value, and type EncryptionContextMenu for the name of the new value.
DWORD Value, and type EncryptionContextMenu for the name of the new value. -
Double-click the new EncryptionContextMenuvalue, enter 1 for the Value data, and click OK.
-
Close the Registry Editor when you're done. The change will take effect immediately.
-
To use this new trick, right-click any unencrypted file in Explorer or on your Desktop, and select Encrypt. Or, right-click an already-encrypted file, and select Decrypt.
If at least one of the selected items is a folder, you'll have the option of encrypting only the folder or all the folders contained therein. If encrypting any individual files, you'll also be asked if you wish to encrypt only the file or the parent folder as well.
8.1.2.5 Using the NTFS Encryption Utility and working with keys
The NTFS Encryption Utility (cipher.exe) is the command-line equivalent of the Encrypt contents to secure data option discussed earlier, but it adds several powerful features not normally available through Explorer. Note that the NTFS Encryption Utility is included with Windows XP Professional only.
Open a Command Prompt window (cmd.exe) and type cipher without any arguments to display the encryption status for all the files in the current folder. (Use the cd command discussed in Appendix C to change to a different working folder.) Encrypted files will be marked with an E; all others will marked with a U.
To encrypt a file, type cipher /e filename, where filename is the name of the file or folder (include the full path if it's in a different folder). Likewise, type cipher /d filename to turn off encryption for the item. These functions are no different than using Explorer to control encryption, except that they have the advantage of being able to be executed from scripts (see Chapter 9) or batch files (see Appendix C). Type cipher /? for more options.
The real meat, however, is in cipher's ability to work with cryptographic keys.[1] Windows XP's encryption system employs symmetric key cryptography, which uses the same key to encrypt and decrypt data. Windows generates a unique key for each user, so that no user can decrypt another user's data.
[1] The classic example of cryptographic keys is how Julius Caesar encoded messages to his allies. Each letter in the message was shifted by three: A became D, B became E, C became F, and so on. Only someone who knew to shift the letters back by three could decode the messages. Cryptographic keys work the same way, except they're much more complicated.
So, what happens if your computer crashes, and you need to retrieve your encrypted data? As long as you've backed up your encryption key, it's not a problem. At the command prompt, type the following:
cipher /r:filename
where filename is the prefix of the output filename (without an extension). Cipher ask for a password, and then generate two separate files based on the specified filename. For example, if you type cipher /r:julius, you'll end up with two files:
- julius.pfx
-
This file contains the EFS (Encrypting File System) recovery agent key and certificate. Store this file in a safe place. If you ever need to retrieve the key, such as if your system crashes and you need access to encrypted data, just re-import the .pfx file by double-clicking it in Explorer.
- julius.cer
-
This file contains the EFS recovery agent certificate only (without the key). Double-click this file to open it in an official Certificate window, and optionally install it in another system. Open the Certificates window (certmgr.msc) to manage your installed certificates. Note that certificates are also used by Internet Explorer to communicate with secure web sites.
You can also generate a new key at any time by typing cipher /k (without any other options). Then, type cipher /u to update the encrypted files on your system with the new key.
8.1.2.6 Securing free space
Normally, when a file is deleted, only the file's entry in the file system table is deleted; the actual data contained in the file remains in the folder until it is overwritten with another file.
Cipher allows you to wipe a folder, which only means that it goes black and cleans out any recently deleted files, overwriting the left over data with random bits. This effectively makes it impossible to subsequently recover deleted data with an "undelete" utility. Think of the wipe feature as a virtual paper shredder.
To wipe a folder, type cipher /w:foldername, where foldername is the full path of the folder to wipe. Note that the /w option does not harm existing data, nor does it affect any files currently stored in the Recycle Bin. It also works on unencrypted folders and encrypted folders alike.
|
8.1.3 Use the Traditional Log On DialogInstead of the Welcome Screen
The new, friendly Welcome screen is the default interface used when logging onto Windows XP.
The traditional Log On dialog forces you to type both the user name and password of a user account to log in. Since a list of active users is not shown, it's more secure than the default Welcome screen. Here's how to switch:
-
Open the User Accounts window in Control Panel.
-
Click Change the way users log on or off.
-
Turn off the Use the Welcome screen option, and click Apply Options.
-
This change will take effect the next time you log off or restart your computer.
When you switch from the Welcome screen to the Log On screen, several other aspects of the Windows interface will be affected. Table 8-2 shows the differences between these two options of this deceptively-simple setting.
| Welcome screen | Log On screen | |
|---|---|---|
| Look and feel of Shut Down dialog | Large, friendly, colorful buttons for Stand By,[2] Turn Off, and Restart | A simple drop-down list, like the Shut Down dialog found in earlier versions of Windows. |
| Start Menu command to shut down | Turn Off Computer | Shut Down |
| Ctrl-Alt-Del | Opens Task Manager; security features shown in Shut Down menu (except for ChangePassword) | Opens the Windows Security dialog, from where you can log off, shut down, start Task Manager, change your password, or lock the computer. |
| Access to hidden user accounts | No access to hidden users | Log into any user account by typing user name |
[2] Hold the Shift key to display a Hibernate button instead of StandBy on the Welcome screen.
8.1.4 Customize the Welcome Screen
Although you can easily customize the look and feel of your own account, it's not so easy to customize the Welcome screen. The following solutions allow you change a few things about the Welcome screen. Note that these solutions have no affect on the Log On screen (discussed in the next section).
8.1.4.1 Choose new pictures for users
When a new account is created in Windows XP, it chooses a picture at random from a collection including a Monopoly race car, a soccer ball, a butterfly, and others. Here's how to change the picture for any account:
-
Open the User Accounts window in Control Panel, and then choose an account to modify in the list below.
-
Click Change my picture.
-
Choose a picture from the collection, or click Browse for more pictures to choose your own image. Windows supports .bmp, .jpg, .gif, and .png image files.
Note that the image you choose here will also be the one that appears at the top of the Start Menu (not applicable if you're using the Classic Start Menu).
-
Click Change picture when you're done. The new picture(s) will show up the next time you log off or restart Windows.
8.1.4.2 Create a new Welcome screen
Although changing the little picture for each user (as described earlier) is quite easy, it's an entirely different matter to customize the actual Welcome screen. The screen is embedded in one of Windows' .exe files, which means you'll need to extract the components of the screen to customize them.
-
Open Explorer, and navigate to your \Windows\System32 folder.
-
Place a copy of the file, logonui.exe somewhere convenient, such as on your Desktop or in your My Documents folder. Then, make another copy of the file, to be used as a backup in case something goes wrong.
-
Download and install the free Resource Hacker utility (available at http://www.annoyances.org/). Resource Hacker allows you to modify the bitmaps embedded in certain types of files, including .exe and .dll files, and is also used in a few solutions in Chapter 2.
-
Start Resource Hacker, and drag-drop the newly-created copy of logonui.exe onto the Resource Hacker window to open it (or use File
 Open).
Open). -
Expand the Bitmap branch to show the various images used on the Welcome page. For example, bitmap 100 is the blue gradient background, bitmap 125 is the horizontal line that appears above and below, and bitmaps 123 and 127 both contain the Windows logo.
Optional: you can export any of these bitmaps to .bmp files by selecting them in the tree, and then going to Action
 Save [Bitmap : ### : ###]. Do this if you wish to modify the existing images rather than (or in addition to) creating your own.
Save [Bitmap : ### : ###]. Do this if you wish to modify the existing images rather than (or in addition to) creating your own. -
Create new images or modify images you've extracted to your heart's content. Save your images as .bmp files.

Try to make your replacement images the same size (width X height) as the default images in this file. If you need to change the size of an image, you'll need a working knowledge of XML. See Step 10, later, for the additional modifications you'll need to make if your images have different sizes than the ones they're replacing.
-
When you're ready, go to Action
 Replace Bitmap. Highlight an entry in the Select bitmap to replace list, then click Open file with new bitmap, and then locate the .bmp file you've created or modified.
Replace Bitmap. Highlight an entry in the Select bitmap to replace list, then click Open file with new bitmap, and then locate the .bmp file you've created or modified. Repeat this for all the images you wish to replace.
-
Next, to customize any of the text shown in the Welcome screen, such as "To begin, click your user name," open the String Table branch, and choose one of the five categories shown. When you've found the text you want to change, just click in the right pane and start typing.

It's important that you keep the formatting of the text intact. For example, quotation marks, commas, and curly braces are used to separate and organize strings. Make sure you don't mess them up.
Here are some tips for modifying the text strings here:
-
To include a line break, type \n.
-
To include a double-quotation mark, type \" (necessary, since a quotation mark without the slash will be interpreted as the closing quotes that mark the end of the string).
-
To insert the username of the selected user, type %s.
-
Some of the strings have names of fonts; as you might expect, you can modify these to change the fonts used in the Welcome screen.
-
-
When you're done typing, click the Compile Script button.
-
The last component that can be modified is the actual layout of the Welcome page. This can be found in the UIFILE\1000 branch. The beginning of the text in this branch is blank, but if you scroll down (in the right-hand pane), you'll see the content. This, essentially, is an XML file, and unless you are familiar with XML (similar to HTML), you won't want to touch it.
However, you may need to modify one or more of the entries here if any of your new bitmaps have different dimensions than the ones they're replacing. Start by locating the <element . . . tag that corresponds to the image you wish to resize; for image 100, for example, it will be the one that has this attribute:
content=rcbmp(100,0,0,219rp,207rp,1,0)
Here, the first number is the image number, and the numbers ending in "rp" are the dimensions.
-
When you're done editing, go to File
 Save to save your changes.
Save to save your changes. 
If you are wise, you will take this opportunity to make sure you have a safe backup of the original logonui.exe before you replace it. That way, if the modified version is corrupted in any way, you'll be able to repair your system without having to reinstall.
-
The last step is to replace the in-use version of logonui.exe with the one you've just modified. You should be able to just drag the modified version right into your \Windows\System32 folder, replacing the one that's there.
If Windows complains that the file is in use and can't be replaced, you'll have to follow the steps outlined in Section 2.2.6.
-
The new logo should appear the next time you start Windows. If, for some reason, the Welcome screen is corrupted or won't load at all, the problem is most likely caused by a corrupt logonui.exe file. This can be repaired by using the instructions in the previous step to replace the modified version with the original version you backed up you did back it up, didn't you?
See Section 2.3.5 for a related solution.
8.1.4.3 Turn off the mail notification
By default, Windows will display the number of unread messages underneath each name on the Welcome screen, but only if you're using Outlook or Outlook Express to retrieve your email. To turn off this notification, follow this procedure:
-
Open the Registry Editor (discussed in Chapter 3).
-
Expand the branches to HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\UnreadMail.
-
Double-click the MessageExpiryDays value in this key.
If it's not there, go to Edit
 New
New  DWORD Value, and type MessageExpiryDays for the name of the new value.
DWORD Value, and type MessageExpiryDays for the name of the new value. -
Type 0 for its value data, click OK, and then close the Registry Editor when you're done. You'll have to log off and then log back on for the change to take effect.
Instead of disabling the feature, you can merely adjust how far back Windows will "look" for unread messages, if you like. For example, change the MessageExpiryDays value to 5 to ignore any unread messages more than five days old. The default is 3.
This feature has been known to stop working if two or more email accounts have been configured in Outlook for a single user account.
8.1.5 Customize the Log On Screen
Although you can easily customize the look and feel of your own account, it's not so easy to customize the Log On screen. The following solutions allow you to customize various aspects of this window and the desktop that appears in the background. Note that these solutions have no affect on the Welcome screen (discussed in the previous section).
8.1.5.1 Customize the appearance of the Log On dialog and the desktop background
Follow these steps to customize the colors used by the Log On dialog, as well as the colors and (optionally) the wallpaper of the desktop that appears behind it:
-
Open the Registry Editor (discussed in Chapter 3).
-
Expand the branches to HKEY_USERS\.DEFAULT\Control Panel\Colors.
-
Each of the values in this key represents the color of a different screen element. Each value has three numbers, the red, green, and blue values, respectfully, of the color of the corresponding object.
For example, double-click the Background value and type 255 0 128 (note the spaces between the numbers) to have a hot-pink background behind the Log On dialog.
To determine the RGB values for your favorite colors, open a Color dialog by going to Control Panel
 Display
Display  Appearance tab
Appearance tab Advanced
Advanced  Color 1
Color 1  Other.
Other. -
While you're here, you can also turn on the ClearType feature for the Log On screen. ClearType helps make text more readable on laptop and flat-panel displays. Double-click the FontSmoothingType value and change its value data to 2 to enable ClearType. A setting of one (1) will enable standard font smoothing, and a setting of zero (0) will turn it off entirely.
-
If you wish to use wallpaper on the Log On desktop instead of a solid color, expand the branches to HKEY_USERS\.DEFAULT\Control Panel\Desktop. Double-click the Wallpaper value, and type the full path and filename of a .bmp or .jpg file to use as the wallpaper. To tile the wallpaper, set the TileWallpaper value to 1, or to stretch the wallpaper, set the WallpaperStyle value to 2.
-
Close the Registry Editor when you're done. The change will take effect the next time you log off or restart Windows.
8.1.5.2 Hide the last-typed username
By default, the username of the previously-logged-in user is shown in the Log On screen. To disable this, follow these steps:
-
Open the Registry Editor (discussed in Chapter 3).
-
Expand the branches to HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon. (Note the Windows NT branch here, as opposed to the more-common Windows branch).
-
Create a new string value here by going to Edit
 New
New  String Value, and type DontDisplayLastUserName for the name of the new value.
String Value, and type DontDisplayLastUserName for the name of the new value. -
Double-click the new value, type 1 for its value data, and click OK.
Note that hiding the last-typed username will disable the automatic login, described in the next section.
8.1.5.3 Customize the log on message (Log On screen only)
The following solution allows you to place your own message above the User name and Password fields in the Log On dialog:
-
Open the Registry Editor (discussed in Chapter 3).
-
Expand the branches to HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon. (Note the Windows NT branch here, as opposed to the more-common Windows branch).
-
Create a new string value here by going to Edit
 New
New  String Value, and type LogonPrompt for the name of the new value.
String Value, and type LogonPrompt for the name of the new value. -
Double-click the new value, type the message you'd like to appear, and click OK.
8.1.6 Logging on Automatically
Depending on your settings, you may or may not see the Welcome screen or the Log On to Windows dialog when Windows first starts. For example, if your computer only has one user account (in addition to the Administrator account, discussed in previous solution), and you haven't specified a password for that account, Windows will log you in automatically.
But it's never a good idea to have any accounts on your system set up without passwords, not so much because someone could break into your computer while sitting at your desk, but because if you're connected to a network or the Internet, an account any account without a password is a big security hole. See Section 7.3.1 for more information.
The problem with setting up a password, however, is that Windows will then prompt you for the password every time you turn your computer, which can be a pain if you're the only person who uses the machine. Fortunately, there is a rather easy way to password-protect your computer and not be bothered with the Log On screen.
-
Open the alternate User Accounts window (described beginning of this chapter) by going to Start
 Run, typing control userpasswords2, and clicking OK.
Run, typing control userpasswords2, and clicking OK. -
Select the username from the list you'd like to be your primary login, and then turn off the Users must enter a username and password to use this computer option.
-
The Automatically Log On dialog will appear, prompting you to enter (and confirm) the password for the selected user.
-
Click OK when you're done. The change will take effect the next time you restart your computer.
Note that this solution will not disable your ability to log out and then log into another user account (see below). Furthermore, logging out and then logging back in will not disable the automatic login; the next time you restart Windows, you'll be logged in automatically to the user account you specified.
8.1.6.1 Prevent users from bypassing the automatic login
Automatic logins are also good for machines you wish to use in public environments (typically called "kiosks"), but you'll want to take steps to ensure that visitors can't log in as more privileged users. There are two ways for a user to skip the automatic login and log into another user account:
-
Hold the Shift key while Windows is logging in.
-
Once Windows has logged in, log out by selecting Log Off from the Start Menu or pressing Ctrl-Alt-Del and selecting Log Off.
This next solution eliminates both of these back doors:
-
Open the Registry Editor (discussed in Chapter 3).
-
Expand the branches to HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon. (Note the Windows NT branch here, as opposed to the more-common Windows branch).
-
Create a new string value here by going to Edit
 New
New  String Value, and name the new value IgnoreShiftOverride. Double-click the new value, type 1 for its value data, and click OK. (This disables the Shift key during the automatic login.)
String Value, and name the new value IgnoreShiftOverride. Double-click the new value, type 1 for its value data, and click OK. (This disables the Shift key during the automatic login.) -
Create a new DWORD value here by going to Edit
 New
New  DWORD Value, and name the new value ForceAutoLogon. Double-click the new value, type 1 for its value data, and click OK. (This automatically logs back in if the user tries to log out.)
DWORD Value, and name the new value ForceAutoLogon. Double-click the new value, type 1 for its value data, and click OK. (This automatically logs back in if the user tries to log out.) -
Close the Registry Editor when you're done. The change will take effect immediately.
To remove either or both of these restrictions, just delete the corresponding registry values.
8.1.6.2 Limit automatic logins
It's possible to limit the automatic login feature, so that the Log On dialog (or Welcome screen) reappears after a specified number of boots:
-
Open the Registry Editor (discussed in Chapter 3).
-
Expand the branches to HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon. (Note the Windows NT branch here, as opposed to the more-common Windows branch).
-
Create a new DWORD value here by going to Edit
 New
New  DWORD Value.
DWORD Value. -
Type AutoLogonCount for the name of the new value.
-
Double-click the new AutoLogonCount value, and type the number of system boots for which you'd like the automatic login to remain active.
Every successive time Windows starts, it will decrease this value by one. When the value is zero, the username and password entered at the beginning of this topic are forgotten, and the AutoLogonCount value is removed.
8.1.7 Logging in as the Administrator
When you first install Windows XP, setup walks you through the process of setting up two separate user accounts. First, you're asked to choose an Administrator password, which is used for an actual account called "Administrator." Setup then requires you to enter the name of at least one user that will be using the computer; that second username is what is used to subsequently log you into Windows XP.
Although the second user has administrator privileges, it's not the true Administrator account, which is occasionally required for advanced solutions. What makes things more difficult is that the Administrator account is hidden from the Welcome screen and the User Accounts window. If you wish to log into the Administrator account, either to complete some solution, or just to use it as your primary login, follow these instructions:
-
Get to the traditional Log On dialog, which requires you to type a username rather than simply clicking it. Not only is this window more secure than the Welcome screen, it's the only way to get to the Administrator account. There are two ways to open the Log On dialog:
-
If you're currently logged-in, select Log Off from the Start Menu. When the Welcome screen appears, press Ctrl-Alt-Del twice.
-
To make the traditional Log On dialog your default, see Section 8.1.4, earlier in this chapter.
-
-
When the old-style Log On to Windows dialog appears, type Administrator into the User name field, and your administrator password into the Password field.
-
If, after logging in as the Administrator, you wish to delete the secondary account created during setup, use the alternate User Accounts window by launching control userpasswords2, as described beginning of this chapter.
8.1.7.1 Notes
-
Despite the fact that the Administrator account is hidden by default, it's perfectly acceptable to use it as your primary login. You may wish to do this simply if you've gotten tired of seeing your name in huge, blazing letters in the Start Menu.
-
If you wish to use the Administrator account as your primary login, but don't wish to enter the password every time you turn on your computer, use the previous solution, "Logging on Automatically."
-
After you log into the Administrator account a few times, it will start showing up on the Welcome screen, at which point you can re-enable the Use the Welcome screen option if you so desire.
8.1.8 Hiding User Accounts
By default, several user accounts are hidden from the User Accounts window and the Welcome screen. Although you can access these accounts using the alternate User Accounts dialog as well as the Local Users and Groups window (both described at the beginning of this chapter), you can also simply unhide these accounts. Naturally, you can also hide additional accounts with this procedure.
-
Open the Registry Editor (discussed in Chapter 3).
-
Expand the branches to HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\SpecialAccounts\UserList. (Note the Windows NT branch here, as opposed to the more-common Windows branch).
-
In this key, there's a DWORD value named for each hidden user. To un-hide a user account, simply delete a corresponding value here.
-
To hide a user, start by creating a new DWORD value by going to Edit
 New
New  DWORD Value. Name the new value after the user you wish to hide.
DWORD Value. Name the new value after the user you wish to hide. -
Setting any of these values to zero (0) will hide the corresponding accounts from both the standard User Accounts window and the alternate User Accounts window, enabling access only through the Local Users and Groups window.
However, if a value is set to 65536 (hex 10000), it will only be hidden from the User Accounts window, allowing access through either the alternate User Accounts dialog or Local Users and Groups.
-
Close the Registry Editor when you're done. The change should take effect the next time any of the user account dialogs are opened.
8.1.9 Working with User Folders
Every user account on your system has its own profile (home) folder, stored, by default, in the \Documents and Settings folder. In this folder are such special user folders as Desktop, Send To, Start Menu, My Documents, and Application Data, among others. Files placed in the Desktop folder appear as icons on the user's desktop, shortcuts placed in the Start Menu folder appear as Start menu items, and so on. This arrangement lets each user have his or her own Desktop, Start Menu, etc.
There's also an All Users folder, used, for example, to store icons that appear on all users' Desktops. Likewise, the Default User folder is a template of sorts, containing files and settings copied for each newly-created user. All-in-all, the use of these folders is pretty self-explanatory.
The following are tips relating to user folders:
-
See Section 3.1.3 for more information on the NTUSER.DAT file found in each user folder.
-
To change the location of any user's home folder, start the Local Users and Groups window (lusrmgr.msc, described at the beginning of this chapter). Open the Users category, double-click a user, and choose the Profile tab.
-
To change the location of any system folder in a user's home folder, such as the My Documents folder or the Send To folder, you must be logged in as that user. Start TweakUI (see Appendix A), open the My Computer category branch, select Special Folders, and choose the folder to relocate from the Folder list. Note that this only changes the place that Windows looks for the associated files; you'll have to create the folder and place the appropriate files in it yourself.
For folders not listed in TweakUI, you'll need to edit the Registry. Most user folders are specified in these two Registry keys:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\ Explorer\Shell Folders HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\ Explorer\User Shell Folders
One of the exceptions is the Application Data folder, which is defined by the DefaultDir value in:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\ ProfileReconciliation\AppData.
You'll need to log out and then log back in for any these changes to take effect.
-
The Program Files and Common Files folders (shared by all users) are both defined in:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion
For Program Files, you'll need to change both the ProgramFilesDir and ProgramFilesPath values; for Common Files, just change the CommonFilesDir value.
When relocating system folders, keep in mind that there can be hundreds of references to them throughout the Registry, especially Program Files and Common Files. You'll probably need to use a program like Registry Search and Replace (available at http://www.annoyances.org ) to easily get them all.
-
To effectively remove a user's system folder, the best thing to do is simply to consolidate it with another system folder. After specifying the new location, as described earlier, just drag-drop the contents of one into the other, and then restart Windows.
The benefits of doing this are substantial. For example, Windows XP comes with the My Documents folder, which helps to enforce a valuable strategy for keeping track of personal documents by providing a single root for all documents, regardless of the application that created them (see Section 2.2.8 for details). The problem is that this design is seriously undermined by the existence of other system folders with similar uses, such as My Pictures, Favorites, Personal, Received Files, and My Files.[3] Consolidating all of these system folders so that they all point to the same place, such as c:\Documents or c:\Projects, causes several positive things to happen. Not only does it provide a common root for all personal documents, making your stuff much easier to find and keep track of, it also allows you to open any document quickly by using the Favorites menu in the Start Menu.
[3] My Files is the counterpart to My Documents, which is used by some older versions of WordPerfect and other non-Microsoft application suites. The Personal folder was used by Microsoft Office 95, but not so much in subsequent releases. Depending on which programs you've installed or have used in the past, these folders may or may not appear on your system.
EAN: 2147483647
Pages: 78