The Basics of Searching
While LDAP allows us to do many things, searching is really the primary activity of LDAP programming. As such, it makes sense that we spend two whole chapters talking about it. Before we can execute a search, we need to answer some important questions.
- Where should the search start?
- How deep in the directory tree should the search go?
- Which objects should be found?
- What attribute data from each object found should be returned?
- How many objects should be found?
- How will security affect my search?
If we take each of these questions in turn, we can start to formulate a simple plan for how to design and perform a search in the most efficient manner. If all of this is starting to look too complicated, don't worry, it will become second nature as your experience using SDS grows.
Deciding Where to Search
Our search starts at the location in the directory defined by the SearchRoot property. SearchRoot contains a DirectoryEntry that represents both the binding context that will be used for connecting to the directory as well as the starting location for the search.
For example, let's say we want to do a search starting at the normal Users container of our Active Directory domain, and the distinguished name (DN) of the domain naming context is as follows:
DC=domain,DC=com
We would first create a DirectoryEntry object pointing to the Users container and pass that to the SearchRoot of the DirectorySearcher, as Listing 4.1 demonstrates.
Listing 4.1. Initializing the SearchRoot of the DirectorySearcher
DirectoryEntry users = new DirectoryEntry( "LDAP://CN=Users,DC=domain,DC=com", null, null, AuthenticationTypes.Secure ); DirectorySearcher ds1 = new DirectorySearcher(users); //this is equivalent DirectorySearcher ds2 = new DirectorySearcher(); ds2.SearchRoot = users; |
The DirectorySearcher will search in some part of the directory tree, starting at the CN=Users container.
Note: Use the Default SearchRoot with Caution
The default value for SearchRoot is null. This has several implications of which we should be aware. First, the LDAP provider will be assumed. Next, the RootDSE of the current domain will be contacted and the default naming context will be queried to determine the starting search location (which means we are searching the entire domain). Finally, the security credentials of the current thread will be used to determine our permissions. Needless to say, these are a lot of assumptions to make, and the result might not be exactly what we wanted. For the sake of clarity, we recommend specifying a SearchRoot using either this property or one of the DirectorySearcher constructors. This makes it much easier to decipher our intent.
How Security Affects Searching
The binding context of the DirectoryEntry object set as our SearchRoot determines the security context for all of the related searching operations. This means that whatever credentials our SearchRoot uses will determine what our DirectorySearcher can and cannot return. Since not all accounts in the directory may have rights to see every object and attribute value, choosing different DirectoryEntry credentials for our SearchRoot may result in completely different search results.
This really comes into play when using nonprivileged accounts and searching for attributes that only more privileged accounts can normally view. In these scenarios, it will appear as though the attribute does not exist on the object. In some cases, we may not have permission to see the whole object or even list the contents of a specific container.
It is important to note that no error will occur when searching for an attribute or location for which the user does not have the proper read privileges. Instead, the returned result set will simply be empty of the prohibited objects or attributes and no indication will be given as to the reason.
One thing a developer can do to troubleshoot these types of issues is to use one of the many freely available LDAP browsers (see Appendix B for our LDAP tools list). By binding as a standard user in such a tool and browsing to an object, we will immediately see what is and is not available in our targeted context.
Controlling Depth of Search with SearchScope
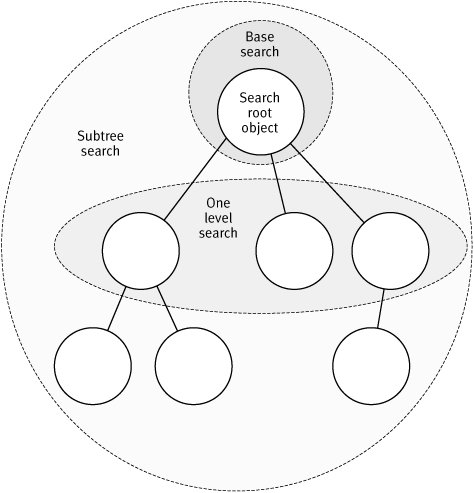
The SearchScope property controls the depth of our search below the SearchRoot object in the directory hierarchy. SearchScope uses an enumeration (also called SearchScope) to define the three possible depths: Subtree, OneLevel, and Base. The default value is SearchScope.Subtree.
Subtree
The Subtree option is typically the one that most developers will use, as it will search the current SearchRoot and all children below it, including any child containers. This is the largest of the scope settings and we typically use it when we do not know where objects are located, or when we want to search for similar objects across disparate containers.
OneLevel
The OneLevel option searches all immediate children of the current SearchRoot, excluding the SearchRoot itself. Unlike the Subtree scope, descendants below the immediate children will not be included. This option is best used when we know which container holds our target objects and we want to tighten our scope.
Base
A Base-scoped search looks within the SearchRoot object itself. This scope is generally used for retrieving constructed attributes of a particular object from the directory. The search does not select any objects below the SearchRoot in the directory hierarchy. As such, we typically set the Filter property to (objectClass=*), which will match any object, as all objects by definition must have an objectClass.
We rarely use this option in SDS to retrieve constructed attributes, because the DirectoryEntry object mirrors this functionality with the RefreshCache method. Given that we need to create the DirectoryEntry anyway to populate the SearchRoot property, using RefreshCache often requires less code and is cleaner (see Chapter 6).
The question becomes, when should we use this scope? It turns out that one of our advanced searches, called an attribute scope query (see Chapter 5), requires this option. We might also use this scope to take advantage of the different data marshaling behaviors of DirectorySearcher compared to DirectoryEntry (see Chapter 6).
Figure 4.1 illustrates the three scope options. In the diagram, we see a root object with three immediate children. Two of the child objects have children as well.
Figure 4.1. Search Scope Options Illustrated
Part I: Fundamentals
Introduction to LDAP and Active Directory
- Introduction to LDAP and Active Directory
- A Brief History of Directory Services
- Definition of LDAP
- Definition of Active Directory
- Definition of ADAM
- LDAP Basics
- Summary
Introduction to .NET Directory Services Programming
- Introduction to .NET Directory Services Programming
- .NET Directory Services Programming Landscape
- Native Directory Services Programming Landscape
- System.DirectoryServices Overview
- System.DirectoryServices.ActiveDirectory Overview
- System.DirectoryServices.Protocols Overview
- Selecting the Right Technology
- Summary
Binding and CRUD Operations with DirectoryEntry
- Binding and CRUD Operations with DirectoryEntry
- Property and Method Overview
- Binding to the Directory
- Directory CRUD Operations
- Summary
Searching with the DirectorySearcher
- Searching with the DirectorySearcher
- LDAP Searching Overview
- DirectorySearcher Overview
- The Basics of Searching
- Building LDAP Filters
- Controlling the Content of Search Results
- Executing the Query and Enumerating Results
- Returning Many Results with Paged Searches
- Sorting Search Results
- Summary
Advanced LDAP Searches
- Advanced LDAP Searches
- Administrative Limits Governing Active Directory and ADAM
- Understanding Searching Timeouts
- Optimizing Search Performance
- Searching the Global Catalog
- Chasing Referrals
- Virtual List View Searches
- Searching for Deleted Objects
- Directory Synchronization Queries
- Using Attribute Scope Query
- Extended DN Queries
- Reading Security Descriptors with Security Masks
- Asynchronous Searches
- Summary
Reading and Writing LDAP Attributes
- Reading and Writing LDAP Attributes
- Basics of Reading Attribute Values
- Collection Class Usage
- Understanding the ADSI Property Cache
- LDAP Data Types in .NET
- ADSI Schema Mapping Mechanism
- .NET Attribute Value Conversion
- Standard Data Types
- Binary Data Conversion
- COM Interop Data Types
- Syntactic versus Semantic Conversion
- Dealing with Attributes with Many Values
- Basics of Writing Attribute Values
- Writing COM Interop Types
- Summary
Active Directory and ADAM Schema
- Active Directory and ADAM Schema
- Schema Extension Best Practices
- Choosing an Object Class
- Choosing Attribute Syntaxes
- Modeling One-to-Many and Many-to-Many Relationships
- Search Flags and Indexing
- Techniques for Extending the Schema
- Discovering Schema Information at Runtime
- Summary
Security in Directory Services Programming
- Security in Directory Services Programming
- Binding and Delegation
- Directory Object Permissions in Active Directory and ADAM
- Code Access Security
- Summary
Introduction to the ActiveDirectory Namespace
- Introduction to the ActiveDirectory Namespace
- Working with the DirectoryContext Class
- Locating Domain Controllers
- Understanding the Active Directory RPC APIs
- Useful Shortcuts for Developers
- Summary
Part II: Practical Applications
User Management
- User Management
- Finding Users
- Creating Users
- Managing User Account Features
- Managing Passwords for Active Directory Users
- Managing Passwords for ADAM Users
- Determining User Group Membership in Active Directory and ADAM
- Summary
Group Management
- Group Management
- Creating Groups in Active Directory and ADAM
- Manipulating Group Membership
- Expanding Group Membership
- Primary Group Membership
- Foreign Security Principals
- Summary
Authentication
- Authentication
- Authentication Using SDS
- Authentication Using SDS.P
- Authentication Using SSPI
- Discovering the Cause of Authentication Failures
- Summary
Part III: Appendixes
Appendix A. Three Approaches to COM Interop with ADSI
- Appendix A. Three Approaches to COM Interop with ADSI
- The Standard Method
- The Reflection Method
- Handcrafted COM Interop Declarations
- Summary
Appendix B. LDAP Tools for Programmers
- Appendix B. LDAP Tools for Programmers
- LDP
- ADSI Edit
- Active Directory Users and Computers
- LDIFDE
- ADFind/ADMod
- BeaverTail LDAP Browser
- Softerra LDAP Browser
- Summary
Appendix C. Troubleshooting and Help
- Appendix C. Troubleshooting and Help
- Error 0x8007203A: "The server is not operational."
- Error 0x8007052E: "Login Failure: unknown user name or bad password."
- Error 0x80072020: "An operations error occurred."
- Error 0x80072030: "There is no such object on the server."
- Error 0x8007202F: A constraint violation occurred.
- Error 0x80072035: The server is unwilling to process the request.
- Error 0x80070005: General access denied error.
- InvalidOperationException from DirectorySearcher
- Summary
Index
EAN: 2147483647
Pages: 165
