Introduction
Passwords are more or less universally hated. Today, they are generally considered the weakest possible authentication tokenpossibly with the exception of a personal identification number (PIN), which is really just a very weak password. Most information security professionals claim that the best thing we could do about passwords is to stop using them altogether in favor of a stronger form of authentication tokens.
We disagree with this assessment slightly. Yes, it is correct that the vast majority of passwords used by users today are very weak. As discussed later, we were able to crack 83 percent of all passwords on a large corporate domain. On a very large Web service with 30 million passwords, the average randomness (entropy) in each was only 18.25 bits. 18.25 bits of entropy means that a perfect password crackerwhich does not exist today, by the waywould only have to test 156,000 passwords to crack one. We usually use 3,000,000 tries per second as a heuristic for password cracking speed, so clearly those passwords are bad.
However, and this is the reason we disagree with the assessment that passwords are bad, the problem with passwords is not inherent in passwords. The problems stem from two things: (1) Human beings are bad at inventing and remembering good passwords, and (2) the password storage implementations in many products today allow attackers to exploit the fact that people pick poor passwords. If we, as human beings, could remember extremely long totally random passwords, such as t4D …~ ]mUz_2 ²P $O FuY & pound ;8 + [ »&j60P G #f&6XU~]u5x k#4 ‰\^ »N 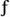 X ²7rf A/. T2< ¼ « &%}IifAV seQ\C SfRx> /qP{] ‰:\=L( 58)L7mMgljMt_$ and the implementations were as strong as the password, there would be nothing wrong with passwords. However, because these two problems are there, it is correct that the security of most (all?) systems would increase if we could replace passwords with other tokens. Ideally, we would use the following preference order for authentication tokens:
X ²7rf A/. T2< ¼ « &%}IifAV seQ\C SfRx> /qP{] ‰:\=L( 58)L7mMgljMt_$ and the implementations were as strong as the password, there would be nothing wrong with passwords. However, because these two problems are there, it is correct that the security of most (all?) systems would increase if we could replace passwords with other tokens. Ideally, we would use the following preference order for authentication tokens:
-
Smart cards with a properly implemented protocol that prevents replay attacks
-
One-time passwords, such as SecureID
-
Unique passwords for each system and user account
-
Passwords, as currently implemented
What About Biometrics?The astute reader will have noticed the absence of biometric authentication systems in our list. It is missing for a reason, which we explore later in this chapter. |
Unfortunately, it is impossible today to completely stop using passwords. Even if you implement a smart card logon system, a user must still have a password stored. (The user may not know what it is, but in some cases, an attacker may extract it and use it.) In certain cases, smart cards, one-time passwords, and other token-based authentication systems cannot be used at all. For instance, only password-based authentication is supported for service accounts. Therefore, we spend a significant part of this chapter on passwords and how to improve the security of a system using them.
EAN: 2147483647
Pages: 219