Chapter 17. System Management Tools
| < Day Day Up > |
16.4. The Mac OS X FirewallMac OS X uses FreeBSD's ipfw2 (IP firewall, version 2) facility to control how incoming and outgoing packets are routed through the system. You use the ipfw utility to define a set of rules that controls this. The default rules allow all traffic from any location to come into your computer, using the following ipfw rule (65535 is the priority level of the rule, the lowest priority possible): 65535 allow ip from any to any To define this rule yourself, you'd issue the following command: # ipfw add 65535 allow ip from any to any Mac OS X uses ipfw and several other tools to share your Internet connection and to protect your Macintosh from malicious hackers. 16.4.1. Internet SharingWhen you turn on Internet Sharing (System Preferences 16.4.1.1. ifconfigIf you're sharing the connection over a port, such as the Ethernet port (en0 on many systems), it probably has a self-assigned IP address. Internet Sharing sets this to the first host on whatever subnet it is using (the default is 192.168.2.1): # ifconfig en0 192.168.2.1 16.4.1.2. ipfw/natdMac OS X adds a firewall rule with a high priority (00010), which diverts any traffic coming into port 8668 on en1 (the AirPort adapter on many systems): # ipfw add 00010 divert 8668 ip from any to any via en1 It also sets the net.inet.ip.forwarding sysctl to 1, which enables IP forwarding. The Network Address Translation Daemon (natd) listens on this port. InternetSharing starts it with this command, where IP_ADDRESS is the IP address you want to share and INTERFACE is the network interface (both the IP address and interface here correspond to "Share your connection from" in the Internet Sharing preference pane). INTERFACE2 should be the interface you're sharing the connection to: # /usr/sbin/natd -alias_address IP_ADDRESS -interface INTERFACE \ -use_sockets -same_ports -unregistered_only -dynamic -clamp_mss \ -enable_natportmap -natportmap_interface INTERFACE2 So, if your AirPort adapter (en1) was assigned the IP address 192.168.254.150, and you shared that connection to another computer plugged into your Ethernet port (en0), natd would be invoked like so: # /usr/sbin/natd -alias_address 192.168.254.150 -interface en1 \ -use_sockets -same_ports -unregistered_only -dynamic -clamp_mss \ -enable_natportmap -natportmap_interface en0 16.4.1.3. bootpdThis is a combined BOOTP and DHCP server. You can find the DHCP configuration in Directory Services, under /config/dhcp/subnets. Here is a dump of the settings, which are created when the firewall is started, and deleted when it is stopped: $ nidump -r /config/dhcp / { "name" = ( "dhcp" ); "bootp_enabled" = ( "" ); "dhcp_enabled" = ( "en0" ); "reply_threshold_seconds" = ( "4" ); "detect_other_dhcp_server" = ( "1" ); CHILDREN = ( { "name" = ( "subnets" ); CHILDREN = ( { "name" = ( "192.168.2" ); "net_address" = ( "192.168.2.0" ); "net_mask" = ( "255.255.255.0" ); "dhcp_router" = ( "192.168.2.1" ); "lease_max" = ( "3600" ); "client_types" = ( "dhcp" ); "dhcp_domain_name_server" = ( "192.168.2.1" ); "net_range" = ( "192.168.2.2", "192.168.2.254" ); "_creator" = ( "com.apple.nat" ); } ) } ) } To allocate addresses in a different subnet, you'd need to change each occurrence of 192.168.2 to a private subnet that conforms to the rules in RFC 1918 (ftp://ftp.rfc-editor.org/in-notes/rfc1918.txt) and load those into Directory Services. Then you'd need to start bootpd with this command: # /usr/libexec/bootpd -P 16.4.1.4. namedThis is the BIND (Berkeley Internet Name Domain) , which provides DNS services to client machines. When you start Internet Sharing, it creates a configuration file for named in /etc/com.apple.named.conf.proxy and runs named with that as its configuration file. Here is a trimmed-down version (comments and white space removed) of that file: controls { }; options { directory "/var/named"; listen-on { 192.168.2.1; }; forward first; forwarders { 192.168.254.1; }; }; zone "." IN { type hint; file "named.ca"; }; zone "localhost" IN { type master; file "localhost.zone"; allow-update { none; }; }; zone "0.0.127.in-addr.arpa" IN { type master; file "named.local"; allow-update { none; }; }; acl can_query {any;}; You'd need to create this file and run named against it if you wanted to start it by hand. Be sure to change any occurrences of 192.168.2 to the appropriate subnet if you changed the DHCP settings. The forwarders setting should be set to the name of your Mac's DNS server. Internet Sharing launches named as: # /usr/sbin/named -c /tmp/com.apple.named.conf.proxy -f For more information, see the respective manpages for these commands, as well as the Advanced Networking section of the FreeBSD Handbook (http://www.freebsd.org/doc/en_US.ISO8859-1/books/handbook/). 16.4.2. The Mac OS X FirewallWhen you enable the firewall (System Preferences 02000 allow ip from any to any via lo* 02010 deny ip from 127.0.0.0/8 to any in 02020 deny ip from any to 127.0.0.0/8 in 02030 deny ip from 224.0.0.0/3 to any in 02040 deny tcp from any to 224.0.0.0/3 in 02050 allow tcp from any to any out 02060 allow tcp from any to any established 65535 allow ip from any to any In addition, the firewall sets up rules for any services you have enabled in the Sharing tab, such as this one, which allows SSH connections by explicitly permitting traffic on port 22: 02070 allow tcp from any to any dst-port 22 in Tiger introduces some advanced capabilities (press Advanced in the Firewall preference pane to set these, as shown in Figure 16-5). Figure 16-5. Configuring advanced firewall options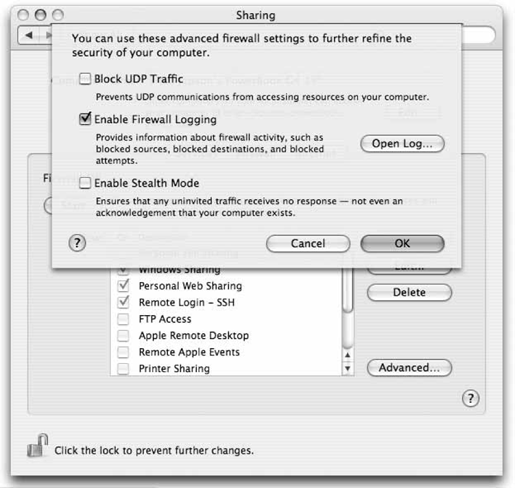 16.4.2.1. Enable Firewall LoggingIf you've enabled this in the advanced settings, this rule will also be in effect, which logs anything that's not permitted: 12190 deny log tcp from any to any The Mac OS X firewall is configured such that only the protocols you specify are allowed through. So, if something is not checked, it won't be permitted through. Here's what you'd see in the firewall log (/var/log/ipfw.log) if you tried to FTP from 192.168.254.150 to a machine (192.168.254.154) whose firewall didn't permit it: Apr 3 15:30:49 brian-jepsons-powerbook-g4-15 ipfw: 12190 Deny TCP 192.168.254.201:32769 192.168.254.150:21 in via en1 16.4.2.2. Block UDP TrafficThis option puts a number of rules into effect, which blocks UDP (User Datagram Protocol) traffic on all but a few essential ports (noted in the # comments): 20310 allow udp from any to any dst-port 53 in # DNS 20320 allow udp from any to any dst-port 68 in # bootpc 20321 allow udp from any 67 to me in # bootps 20322 allow udp from any 5353 to me in # Bonjour 20340 allow udp from any to any dst-port 137 in # Samba 20350 allow udp from any to any dst-port 427 in # SLP 20360 allow udp from any to any dst-port 631 in # CUPS 20370 allow udp from any to any dst-port 5353 in # Bonjour 22000 allow udp from any to any dst-port 123 in # network time 30510 allow udp from me to any out keep-state 30520 allow udp from any to any in frag 35000 deny log udp from any to any in 16.4.2.3. Enable Stealth ModeThis option renders your server somewhat invisible by setting the following sysctls to 1: net.inet.tcp.blackhole net.inet.udp.blackhole net.inet.tcp.log_in_vain net.inet.udp.log_in_vain This sets both the blackhole (don't reply at all to connections; act as if there's not even a server there) and log_in_vain (log all those rejections in /var/log/ipfw.log) options for UDP and TCP traffic. It also sets the following firewall rule to deny ICMP echo requests: 20000 deny icmp from any to me in icmptypes 8 16.4.3. Add Your Own RulesYou can add your own packet filter rules by clicking the New button on the Firewall tab. You can also add your own firewall rules using the ipfw utility, but the Firewall tab remains disabled until you reboot or clear the rules with sudo ipfw flush. For example, you could add a custom firewall rule such as this one, which permits Telnet from only one host (192.168.254.150): # ipfw add 02075 allow tcp from 192.168.254.150 to any dst-port 23 in However, if you navigated to the Firewall preferences pane, you'd get the message shown in Figure 16-6. (You'll also get this message if you're running an application that uses ipfw to its own twisted ends, such as Virtual PC.) You can get things back to normal by deleting the rule: # ipfw delete 02075 Figure 16-6. You won't be able to make changes until you put things back the way you found them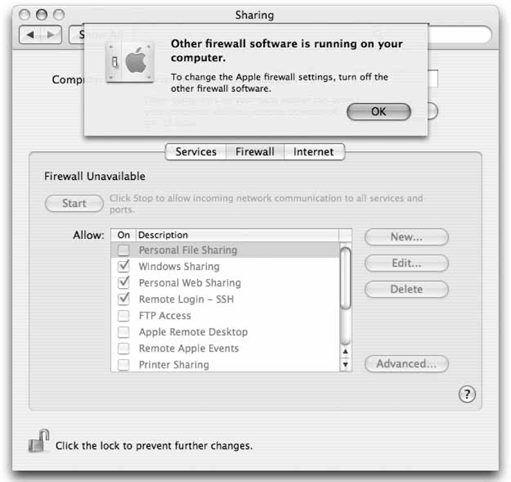 You may need to quit and restart the System Preferences application before it notices that you've reset the firewall to the default rules. For more information, see the ipfw manpage. |
| < Day Day Up > |
EAN: 2147483647
Pages: 176
 Sharing
Sharing