Basic User and Group Management
Basic User and Group Management
Everyone on a Linux system needs a user account. Every account has rights and privileges that vary depending on the command and the directory. Linux user accounts are organized into groups. While default users are the only member of their default groups, you can organize users into new groups, and you can configure rights and privileges that vary differently by group.
In Red Hat Linux, user accounts are organized in /etc/passwd . Their passwords are made more secure in /etc/shadow . For Red Hat Linux groups, the analogous files are /etc/group and /etc/gshadow .
When creating a new account, the default parameters are configured in /etc/login.defs; configuration files are normally copied to the new user s home directory from the /etc/skel directory.
| Note | Regular users will want their own accounts, and generally , you want to minimize risks by keeping them away from root user privileges. However, if you re the administrator for your Linux computer, you may want to sign in as the root user, for the reasons discussed in Chapter 06 . |
/etc/passwd
Linux users can be classified into three groups: administrative, service, and regular users. Every user has rights and privileges. Regular and administrative users have usernames, passwords, and home directories. All users are configured through a line in the /etc/passwd file, as shown in Figure 9.1.
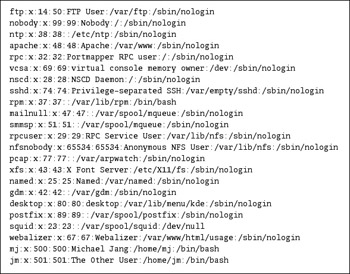
Figure 9.1: /etc/passwd
The last two lines in this figure contain entries for regular users. As you can see, usernames are associated with services such as ftp , apache , and squid . Each entry includes seven columns delineated by colons (:). Table 9.1 describes each of these columns .
/etc/shadow
Red Hat Linux includes the /etc/shadow file for additional password security. By default, this file is readable only to the root user. If you use standard commands to create new users, basic information is also added to this file, based on the defaults in /etc/login.defs (which we discuss later in this chapter). Take a look at /etc/shadow in Figure 9.2.
| Column | Function | Comment |
|---|---|---|
| 1 | Username | Login name . |
| 2 | Password | If this field contains an x , the encrypted password is stored in /etc/shadow . |
| 3 | User ID | Red Hat User IDs start at 500. |
| 4 | Group ID | Red Hat Group IDs normally match User IDs. |
| 5 | Extra information | Commonly used for a user s real name. |
| 6 | Home directory | Normally /home/ username . |
| 7 | Default shell | The shell a user sees after logging in. |
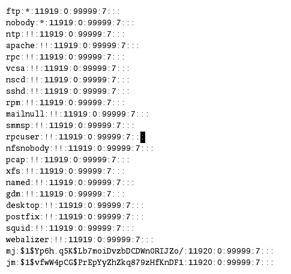
Figure 9.2: /etc/shadow
As you can see, the last two lines contain entries for the same regular and service users that were shown in /etc/passwd . In this case, each user entry includes eight columns delineated by colons (:). Table 9.2 describes each of these columns.
| Column | Function | Comment |
|---|---|---|
| 1 | Username | Login name. |
| 2 | Password | Encrypted password. |
| 3 | Number of days | Last time the password was changed, in days, after January 1, 1970. |
| 4 | Minimum password life | You can t change a password for at least this amount of time, in days. |
| 5 | Maximum password life | You have to change a password after this period of time, in days. |
| 6 | Warning period | You get a warning this many days before your password expires . |
| 7 | Disable account | If you don t use your account this many days after your password expires, you can t log in. |
| 8 | Account expiration | If you don t use your account by this date, you won t be able to log in. May be in YYYY-MM-DD format, or in the number of days after January 1, 1970. |
/etc/group
The Red Hat Linux group configuration file is simpler than those for users; they include only four columns. In Figure 9.3, you can see the same two regular usernames in /etc/group that you saw in /etc/passwd and /etc/shadow . In /etc/group , they are group names . You may note that the group

Figure 9.3: /etc/group
ID for groups mj and jm matches the user IDs for the users with the same names in the previous two configuration files.
Note the final entry, the Sharing group. As you can see, users mj and jm are members of that group. Table 9.3 describes the columns in /etc/group .
| Column | Function | Comment |
|---|---|---|
| 1 | Group name | By default, Red Hat users are members of groups with the same name. |
| 2 | Password | If you see an x in this column, see /etc/gshadow for the actual encrypted password. |
| 3 | Group ID | By default, Red Hat users have the same ID as their groups. |
| 4 | Members | Includes the usernames of others that are members of the same group. |
/etc/gshadow
The Red Hat Linux /etc/gshadow configuration file for groups is analogous to the /etc/shadow file for users. It specifies an encrypted password for applicable groups, as well as administrators with privileges for a specific group. A sample /etc/gshadow file is shown in Figure 9.4.

Figure 9.4: /etc/gshadow
Note the differences from /etc/group with respect to the Sharing group. Table 9.4 describes the columns in /etc/shadow .
| Column | Function | Comment |
|---|---|---|
| 1 | Group name | You can create additional groups. |
| 2 | Password | The encrypted group password, added with the gpasswd command. |
| 3 | Group administrator | The user allowed to manage users in that group. |
| 4 | Group members | Includes the usernames that are members of the same group. |
/etc/skel
Users have a default set of configuration files and directories. You examined some of these files as they related to the bash shell in Chapter 08 . The default list of these files is located in the /etc/skel directory, which you can easily inspect with the ls -la /etc/skel command, as shown in Figure 9.5. The list changes depending on what you have installed.
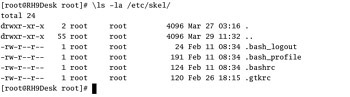
Figure 9.5: Default home files in /etc/skel
| Tip | If you have a list of standard files, such as corporate policies for new users, you may want to copy them to /etc/skel . All new users will get a copy of these files in their home directories. |
/etc/login.defs
When you create a new user, the basic parameters come from the /etc/login.defs configuration file. The version included with Red Hat Linux includes settings for e-mail directories, password aging, user ID and group ID numbers , and creating a home directory. The default variables in this file are almost self-explanatory:
MAIL_DIR /var/spool/mail # Default mail directory PASS_MAX_DAYS 99999 # Password max life PASS_MIN_DAYS 0 # Password min life PASS_MIN_LEN 5 # Min password length PASS_WARN_AGE 7 # Warning before expiration UID_MIN 500 # Lowest User ID number UID_MAX 60000 # Highest User ID number GID_MIN 500 # Lowest Group ID number GID_MAX 60000 # Highest Group ID number CREATE_HOME yes
Needless to say, these settings can be further refined through other configuration files. For example, you can manage the allowed lifetime settings for passwords by editing /etc/shadow . You can review a copy of this file in Figure 9.6.
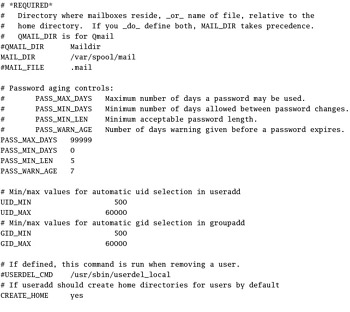
Figure 9.6: /etc/login.defs
EAN: 2147483647
Pages: 220