Understanding Protocol Stacks
Now you can see that computers on a network need different elements to communicate. They need domain names , numeric addresses, and hardware addresses. They also need connection managers and application protocols such as those related to mail, web pages, file servers, and more. These elements can be classified through a protocol stack.
A protocol stack is essentially a division of labor. Some protocols are associated with applications such as mail or DNS. Others cite domain names, IP addresses, and hardware addresses. Some can encrypt your data, manage the 1s and 0s of binary code, or govern a remote login session.
There are two major ways to divide this labor. One is known as the OSI model of networking. This section examines the basics of OSI, as well as a couple of the other major protocol stacks, NetBEUI and IPX/SPX. The other major model of networking is based on TCP/IP, and we discuss it later in this chapter.
| Tip | The arguments between supporters of the OSI and TCP/IP models of networking can be as vigorous as the arguments between the supporters of Linux and Microsoft Windows. While purists may object to the use of OSI to describe TCP/IP protocols, it is a useful learning exercise. |
OSI Levels
The OSI model of networking consists of seven levels. Before your computer sends a message over a network, your message is translated through these levels into the 1s and 0s that are actually sent over a network. The programs associated with each level perform different functions such as encryption, error checking, and routing.
The following is a brief description of each of these levels, from top to bottom, as shown in Figure 20.1. Pay attention to the numbers associated with each level.
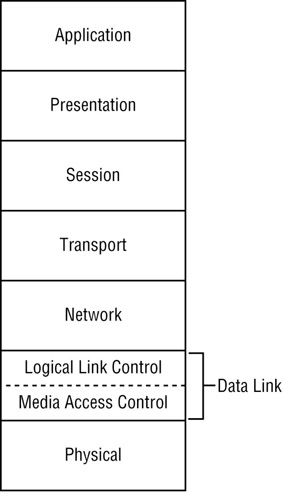
Figure 20.1: The OSI model
Application Application-level (7) protocols start the translation process from the programs that you use. For example, HTTP is an Application-level protocol that translates data from web browsers such as Mozilla. Gateways are computers that can translate applications between networks.
Presentation Presentation-level (6) protocols translate numbers and letters into lower-level computer code. One example is ASCII, which represents the numbers and characters on an English-language keyboard. Encryption protocols such as the Secure Sockets Layer (SSL) are also part of the Presentation level.
Session Session-level (5) protocols manage the time you spend on a network. These protocols determine which computer is sending and receiving messages at any particular time. For example, Session-level software in your network card determines whether data moves one direction at a time (half-duplex) or both directions simultaneously ( full-duplex ).
Transport Transport-level (4) protocols can resend your message until it gets a return receipt (a.k.a., an acknowledgment), or it can just send a message and make a best effort to get it to the destination computer. The two major TCP/IP Transport-level protocols are TCP and UDP. Transport protocols also begin breaking down messages into packets. TCP adds a request for acknowledgment to the start of the packet; UDP does not.
| |
Unless your message is very small, computer networks don t send complete messages all at once. Starting at the Transport level, networks break messages down into packets. As you go further down OSI hierarchy, the packets may be further divided into smaller packets or even cells . Some protocols may send each packet or cell through a different route on the Internet; address information is included with each packet to make sure that your message gets reassembled at the right computer, in order.
For example, Ethernet packets, which are created at the Data-Link level, can contain up to 1518 bytes. This includes 1500 bytes of data and 18 bytes of address information (and more), to ensure that the packet gets to the right computer on a network.
The details of network design are rich and complex. Perhaps the standard reference for network design is Computer Networks , by Andrew Tanenbaum, Prentice Hall, 2002.
| |
Network Network-level (3) protocols actually move the data from computer to computer, and from network to network. IP is the quintessential Network-level protocol. Your messages need IP addresses to move between networks. Routers can manage traffic between networks at this level.
Data-Link Data-Link-level (2) protocols are primarily used to make sure that your information gets to the destination computer correctly. This is often split into two sublevels: Logical Link Control (LLC) and Media Access Control (MAC). LLC protocols ensure that your messages reach the destination computer in order, without errors. This is also known as frame synchronization and error checking. MAC protocols help computers communicate with each other. That is why the hardware address of a network card is also known as a MAC address. Switches or bridges can manage traffic within a network at this level.
Physical Physical-level (1) protocols translate data into the 1s and 0s of computer communication. They also govern the physical world of networking, such as the cables and connectors.
| Note | When you re shopping for network hardware, keep in mind that sales engineers often refer to components by a certain level. For example, standard switches work at level 2 and basic routers work at level 3. However, the boundaries are not rigid. For example, some switches include routing or transport functionality and are then advertised as level 3 or level 4 switches. |
NetBEUI
NetBEUI is the NetBIOS Extended User Interface. This is the set of protocols developed by Microsoft and IBM for networks. It is based on NetBIOS, the Network Basic Input Output System. NetBIOS includes a series of commands that allows a computer to send and receive data, as well as information on shared directories on other computers on that network.
The main drawback of NetBEUI and NetBIOS is that it is not routable. In other words, you can t connect a NetBEUI network to another network such as the Internet. A NetBEUI network is limited to 255 computers.
However, Microsoft has adapted NetBIOS commands to routable network protocol stacks such as TCP/IP and IPX/SPX. If you re an administrator of a network that includes Microsoft computers, you should know a few basic NetBIOS commands, such as net view and net use .
When you use Samba, you re taking advantage of the format associated with NetBIOS commands known as the Server Message Block (SMB). In Chapter 29 , you ll learn about the commands that you can use on a Linux system. Since Samba is essentially the Linux/Unix implementation of NetBIOS, you should not be surprised to find Samba commands that correspond directly to NetBIOS commands such as net view and net use .
IPX/SPX
Like TCP/IP, IPX/SPX is actually a suite of protocols for network communication. It was developed by Novell, in support of its NetWare program, which is actually a network operating system.
Many older networks still use NetWare. However, NetWare also supports TCP/IP, so you probably do not need to adapt to IPX/SPX even if you re connecting to a NetWare-based network.
IPX/SPX is routable. In earlier versions of Microsoft Windows, IPX/SPX was the only choice available if you wanted to configure computers on multiple networks.
If you need to connect to an IPX/SPX network, you ll want the mars-nwe-* , ipxutils-* and ncpfs-* RPM packages. The first package allows your Linux computer to act as a file and print server on a NetWare network. The second package includes support for IPX/SPX. The final package includes the commands you need to act as a client on a NetWare network.
| Note | There are several other major protocol suites, including IBM s System Network Architecture (SNA), the Xerox Network System (XNS), and the Digital Equipment Corporation network (DECnet). DEC is now part of Hewlett-Packard. |
EAN: 2147483647
Pages: 220