Certification Objective 7.03: The Very Secure FTP Service
|
| < Day Day Up > |
|
FTP, the File Transfer Protocol, is one of the original network applications developed with the TCP/IP protocol suite. It follows the standard model for network services, as FTP requires a client and a server. The FTP client is installed by default on most operating systems, including Red Hat Enterprise Linux. If you've installed the FTP Server package group, you've installed the default Red Hat FTP Server, the very secure FTP (vsFTP) daemon. But before we begin, let's look at FTP clients.
| On The Job | Red Hat no longer includes alternate FTP servers such as WU-FTP. When you install vsFTP on your computer, you're installing the same FTP server used on ftp.redhat.com. |
FTP Client (lftp)
The original FTP client software was a basic command line, text-oriented client application that offered a simple but efficient interface. Most Web browsers offer a graphical interface and can also be used as an FTP client.
Any FTP client allows you to view the directory tree and files. Using ftp as a client is easy. You could use the ftp command to connect to a server such as ftp.redhat.com with the following command:
# ftp ftp.redhat.com
The FTP client listed in the Red Hat Exam Prep guide is lftp. You can use it to connect to the FTP server of your choice. It automatically attempts an anonymous login. It also supports command completion, which can especially help you access files and directories with longer names.
Figure 7-7 illustrates a typical lftp session to ftp.redhat.com. As you can see, lftp uses a number of typical bash commands. The command completion feature lists available subdirectories. I've navigated to the directory with RHEL 3 Source RPMs.
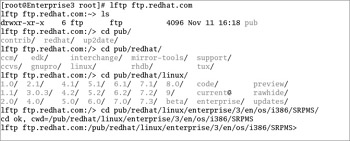
Figure 7-7: A typical lftp session
Another advantage of lftp is that it can handle all of the basic upload and download commands of a regular FTP client. Some of these commands are described in Table 7-1.
| Command | Description |
|---|---|
| cd | Changes the current working directory at the remote host |
| ls | Lists files at the remote host |
| get | Retrieves one file from the remote host |
| mget | Retrieves many files from the remote host with wildcards or full filenames |
| put | Uploads one file from your computer to the remote host |
| mput | Uploads a group of files to the remote host |
| pwd | Lists the current working directory on the remote host |
| quit | Ends the FTP session |
| !ls | Lists files on your host computer in the current directory |
| lcd | Changes the local host directory for upload/download |
| !pwd | Lists the current working directory on local host computer |
Almost all commands in FTP mode are run at the remote host, similar to a Telnet session. You can also run commands locally from the FTP prompt. When you start the command with an exclamation point (!), you can run regular shell commands.
This is only a subset of the commands available through lftp. Typing the help command will give you a full list of the available commands. The command help cmd yields a brief description of the command itself.
One graphical FTP client for Linux is GNOME FTP (GFTP). GNOME FTP provides an easy-to-use GUI interface to FTP. It also offers these features:
-
Restartable transfers
-
Multiple independent transfers
-
Download file queuing
-
Transferring whole directory trees (recursive transfers)
-
Drag-and-drop transfer activation
-
Session names and settings
And with GFTP you don't even need to know a single FTP command. If you have installed the gftp RPM, you can start the GFTP client from a GUI command line with the gftp command. Alternatively, you can start it from the Red Hat GNOME or KDE desktop with the Main Menu | Internet | More Internet Applications | gFTP command.
Installing the Very Secure FTP Server
The only FTP server included with RHEL 3 is vsFTP. In fact, it's the only RPM that's part of the FTP Server package group. If it isn't already installed, you probably won't have to bother with the GUI package management utility. This package has few dependencies, and should be installed automatically when you install RHEL 3. Assuming you've connected to the NFS installation share described in Chapter 2, you'd run the following command:
# rpm -Uvh /mnt/inst/RedHat/RPMS/vsftpd-1.2.0-4.i386.rpm
In the following sections, I'll show you how to start the vsFTP service the next time you reboot your computer, how it's already configured by default, and how to secure it by user. If you want to limit access to vsFTP by computer or network, you'll have to use the tcp_wrappers system, with its hosts.allow and hosts.deny files in the /etc directory, as described in Chapter 10.
Starting on Reboot
Once vsFTP is installed, you'll want to make sure it starts the next time you boot Linux. If it doesn't start when the person who grades your Red Hat exam reboots your computer, you may not get credit for your work configuring an FTP server.
The most straightforward way to make sure the FTP server starts the next time you boot Linux is with the chkconfig command. You'll need to set it to start in at least runlevels 3 and 5, with a command such as:
# chkconfig --level 35 vsftpd on
To see if the chkconfig command worked, use the --list switch:
# chkconfig --list vsftpd
If you want to start the vsFTP server, just start the service script with the following command:
# service vsftpd start
Basic FTP Server Configuration
As you've seen in Chapter 2, the vsFTP server is very easy to configure. Once you've started the daemon and modified any current firewalls, it's ready for use. By default, remote users can log in anonymously or with a username on the local computer. The sequence is straightforward. Assume you have a vsFTP server on a computer named Enterprise3. To connect anonymously using the lftp client, you'd run the following command:
# lftp Enterprise3
This opens a connection in the /var/ftp directory. It looks like a top-level root directory to the lftp client. Alternatively, if you wanted to connect to the account of user michael, you'd add just a little more:
# lftp -u michael Enterprise3
This opens a connection to the /home/michael directory. Unfortunately, the default is dangerous, as users who log in with a real username can navigate to the top-level root directory.
vsFTP Server Security
So now you know that vsFTP can be dangerous. But you can help secure your system by configuring vsFTP to disable logins from regular users. Naturally, you can configure vsFTP through the vsftpd.conf configuration file, in the /etc/vsftpd directory.
The commands in this file are straightforward. I urge you to read the file for yourself; the comments make many of the commands self-explanatory. Let's examine just a few of these commands in Table 7-2. I've focused on those commands that you might change to enhance the security of your system. The commands in the default vsftpd.conf file are just a small fraction of the commands that you can use. You can review the RHEL 3 Reference Guide available online at www.redhat.com/docs/manuals/enterprise for detailed information.
| Command | Description |
|---|---|
| anonymous_enable=YES | If you don't want anonymous access, you'll have to set this to NO. |
| local_enable=YES | If you don't want regular users to log in, comment this out by adding a pound (#) character. |
| write_enable=YES | If you don't want remote users writing to your directories, comment out this command. |
| #chroot_list_enable=YES | If you set chroot_local_user=YES (see discussion that follows), you can configure users who are allowed to roam through your directories by activating this command. |
| pam_service_name=vsftpd | Configures Pluggable Authentication Module (PAM) security. For more information, see Chapter 10. |
| userlist_enable=YES | Don't change this! This keeps users such as root from logging into your system. |
| tcp_wrappers=yes | Supports the use of security commands in /etc/hosts.allow and /etc/hosts.deny. See Chapter 10. |
By default, vsFTP is configured to disable logins from sensitive users such as root, bin, and mail. The userlist_enable=YES command points to a list of disabled users in /etc/vsftpd.user_list. As vsFTP also uses Pluggable Authentication Modules (PAM) for security, it also disables the users in /etc/vsftpd.ftpusers. The list of users in the default versions of this file are identical.
If you want regular users to log into your FTP server, you should add the chroot_local_user=YES command. This helps secure your system by keeping regular users from navigating to your top-level root directory (/).
A couple of useful features for users help welcome them to your server. The following command provides a message for users who are logging into your system:
ftpd_banner=Welcome to blah FTP service
This next message looks for a .message file in each directory and sends it to the client:
dirmessage_enable=YES
Unfortunately, these messages don't work for users who log into your system using a client such as lftp.
Access by root and many service users are disabled by default. If you try to log in as root using lftp, it will look like you're connected. But when you try to do something as root, you'll see messages delaying your commands 'before reconnect.'
Exercise 7-5: Configuring a Basic FTP Server
In this exercise, you'll install and activate a basic vsFTP server on your RHEL 3 computer. While you should ideally also have a second computer, it isn't absolutely necessary here.
-
Check your system to see if the vsFTP server is installed. The easiest way is with the following command:
# rpm -q vsftpd
-
If it isn't already installed, use the techniques discussed in earlier chapters to install the vsFTP RPM package on your computer.
-
Activate the vsFTP server with the service vsftpd start command.
-
Make sure this server is automatically activated the next time you boot Linux with the following command:
# chkconfig --level 35 vsftpd on
-
Log into the vsFTP server as a regular user. You should preferably log in from a remote computer.
-
Once you're logged in, run the cd .. command twice (remember the space between the command and the two dots). Explore the local directory. You should see a danger here, as this is the root directory for the FTP server computer.
-
Close the FTP client session.
-
If you're concerned about the security issues, deactivate the vsFTP server. The best way to secure FTP is to uninstall the vsFTP server. However, if you need a vsFTP server, work with the lab at the end of the chapter.
|
| < Day Day Up > |
|
EAN: N/A
Pages: 194
- The Effects of an Enterprise Resource Planning System (ERP) Implementation on Job Characteristics – A Study using the Hackman and Oldham Job Characteristics Model
- Distributed Data Warehouse for Geo-spatial Services
- Data Mining for Business Process Reengineering
- Intrinsic and Contextual Data Quality: The Effect of Media and Personal Involvement
- Development of Interactive Web Sites to Enhance Police/Community Relations