Certification Objective 15.04-Security Enhanced Linux
Security Enhanced Linux (SELinux) provides one more layer of security. Developed by the US National Security Agency, SELinux makes it more difficult for crackers to use or access any file or service if they break in. SELinux assigns different contexts to each file, known as subjects, objects, and actions.
To see the context of a particular file, run the ls -Z command. As an example, review what this command does in Figure 15-3, as it displays security contexts in my /root directory.
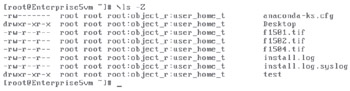
Figure 15-3: ls -Z output
For this purpose, we'll examine basic configuration tools for SELinux, including the SELinux Management Tool and the Setroubleshoot Browser.
Most SELinux settings are boolean-in other words, they're activated and deactivated by setting them to 1 or 0. Naturally, the booleans are stored in the /selinux/booleans directory. One simple example is user_ping, which is normally set to 1, which allows users to run the ping command. For a fuller description, see the NSA Guide to Security Policy Configuration using SELinux at www.nsa.gov/selinux/papers/policy/node1.html.
| On the Job | If you just want to experiment with SELinux, configure it in Permissive mode. It'll log any violations without stopping anything. It's easy to set up with the Security Level Configuration tool, or you can set SELINUX=permissive in /etc/sysconfig/selinux. |
SELinux Status
There are three possible statuses for SELinux: enforcing, permissive, and disabled. enforcing and disabled are self-explanatory. permissive means that any SELinux rules that are violated are logged; however, permissive SELinux doesn't stop anything.
If SELinux is active, it protects systems in two ways: in targeted or in strict mode. The default is targeted, and that is what I recommend that you use; it allows you to customize what it protects, and how.
As you'll see shortly, SELinux is easy to configure with the GUI SELinux Management Tool. However, the basics can be easily configured in the /etc/ sysconfig/selinux configuration file. There are three directives in this file, as described in Table 15-3.
| Directive | Description |
|---|---|
| SELINUX | Basic SELinux status; may be set to enforcing, permissive, or disabled. |
| SELINUXTYPE | Specifies the level of protection; set to targeted by default, where protection is limited to daemons. The alternative is strict, which is associated with full SELinux protection. |
| SETLOCALDEFS | Supports the configuration of local SELinux policies. Set to 0 (disabled) by default. |
If you want to change the basic status of SELinux, change the SELINUX directive. The next time you reboot, the changes are applied to your system.
If you have to configure SELinux during your exam, it's no longer possible to do so during the installation process (except to specify enforcing, permissive, or disabled). If you have to configure SELinux and have to reboot, the process of applying SELinux policies can take several minutes. You won't be able to log in or do anything else during your exam. So plan ahead!
Configuring Manually
SELinux is still relatively new. If you don't understand it well, it may be more efficient to use the SELinux Management Tool to configure SELinux settings. And it's much improved from the GUI SELinux functionality that was part of the Security Level Configuration tool. You can even set SELinux contexts for individual directories from the new tool.
However, as this tool is new, many will believe it's unproven, perhaps until RHEL 6 is released. In Chapter 9, I described how you can set SELinux contexts manually for Apache virtual hosts.
To this end, there are some essential SELinux commands. If you've enabled SELinux, the ls -Z command displays the current contexts, as described earlier in Figure 15-3. To see the current status of SELinux, run the getenforce command; it returns one of three self-explanatory options: enforcing, permissive, or disabled.
You can change the current SELinux status with the setenforce command; the options are straightforward:
# setenforce enforcing # setenforce permissive
This changes the /selinux/enforce boolean. Naturally, you can also change the boolean directly with a command such as:
# cat "1" > /selinux/enforce
If you want to change the settings of a file or directory, you can use the chcon command. For example, if you wanted to configure a non-standard directory for an FTP server, you'll want to make sure the context matches the default FTP directory. As you can see from the following command:
# ls -Z /var/ftp/ drwxr-xr-x root root system_u:object_r:public_content_t pub
The contexts are the system user (system_u) and system objects (object_r), for type sharing with others (public_content_t). If you create another directory for FTP service, you'll need to assign the same security contexts to that directory. For example, if you create an /ftp directory as the root user and run the ls -Z / command, you'll see the contexts associated with the /ftp directory as shown:
drwxr-xr-x root root user_u:object_r:root_t ftp
To change the context, use the chcon command. If there are subdirectories, you'll want to make sure changes are made recursively with the -R switch. In this case, to change the user and type contexts to match /var/ftp, run the following command:
# chcon -R -u user_u -t public_content_t /ftp
If you want to support uploads to your FTP server, you'll have to assign a different type context, specifically public_content_rw_t. That corresponds to the following command:
# chcon -R -u user_u -t public_content_rw_t /ftp
Default contexts are configured in /etc/selinux/targeted/contexts/files/file_contexts. If you make a mistake and want to restore the original SELinux settings for a file, the restorecon command restores those settings based on the file_contexts configuration file. However, the defaults in a directory are not necessarily the same as the contexts you created. For example, the following command leads to a different set of contexts for the /ftp directory:
# restorecon -F /ftp # ls -Z / drwxr-xr-x root root system_u:object_r:default_t ftp
Configuring with the SELinux Management Tool
This section assumes you've enabled SELinux in enforcing or permissive mode, using one of the methods described earlier. The easiest way to change SELinux settings is with the SELinux Management Tool, which you can start with the system-config-selinux command. If you haven't enabled it, you won't even be able to start the tool as shown in Figure 15-4, at least until bug 232544 is addressed. Enable SELinux, at least in permissive mode, and reboot, before continuing with this chapter. If you have to use SELinux during the RHCE exam, you'll probably have to configure SELinux in enforcing mode.
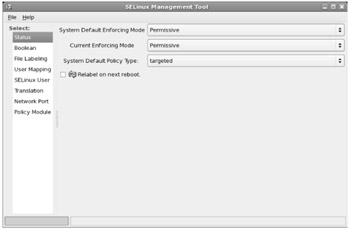
Figure 15-4: SELinux Management Tool
The SELinux Management Tool is much more capable than the previous utility that was part of the Security Level Configuration tool. As you can see, there are options for Default and Current enforcing modes, which you can set to Enabled, Permissive, or Disabled. As of this writing, this tool supports only a targeted system default policy type. Generally, you don't need to activate the Relabel On Next Reboot option unless you've changed the default policy type.
There are a number of categories shown in the left pane of the SELinux Management Tool window which are described in the following sections. Most of the focus here will be in the Boolean category, where most of SELinux policies are customized.
SELinux Boolean Settings
As you can see, SELinux policy can be modified in a number of different categories, some related to administrative functions, others to specific services. Some of these options are shown in Figure 15-5. Any changes you make are reflected in boolean variables in the /selinux/booleans directory. You may not see these variables in /selinux/booleans until you make those changes.
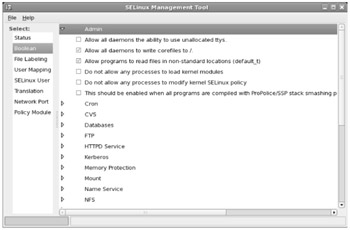
Figure 15-5: SELinux Boolean options
As the Security Level Configuration tool is updated regularly, the detailed information in this section of the book may not be completely up to date. You may even see more categories and options than what I describe in this section, depending on the services and packages you have installed.
I do not cover every option. Don't get lost in these options, even though Red Hat has just added SELinux as a requirement for the RHCE and RHCT exams.
Admin
Under the Admin category, you can allow systems to use unallocated terminals (ttys), allow writing to the top-level root (/) directory, read files from non-standard locations, prevent any process from loading kernel modules, prevent any modifications to SELinux policy, and enable support for the ProPolice SSP stack smashing protector.
Cron
In this section, you can enable extra rules to support the fcron command scheduler as well as disable SELinux protection for the cron daemon.
CVS
If you use the CVS revision control system, you may want to allow it to read shadow passwords.
Databases
If you install the MySQL or PostgreSQL database systems, you can disable SELinux protection for such.
FTP
There are six configuration options in this section. By default, RHEL 5's SELinux configuration allows FTP services to run as individual services, separate from the xinetd super server described in Chapter 13. One supports the running of vsftpd as a regular service, not connected to inetd, or the Red Hat version of the service, xinetd. Others allow uploads to directories configured with the public_content_rw_t directive discussed earlier. You can also support the use of CIFS and NFS for file transfer, allow reads and writes to user home directories, or even disable SELinux protection for FTP services.
HTTPD Service
There are a number of SELinux directives available to help secure the Apache Web server, as summarized in the following bullet points. Most are straightforward and self-explanatory. In a few cases, I've added additional explanation in parentheses.
-
Allow Apache to use mod_auth_pam (Pluggable Authentication Modules)
-
Allow HTTPD cgi support (for CGI scripts)
-
Allow httpd daemon to write files in directories labeled public_content_rw_t (similar to FTP)
-
Allow HTTPD scripts and modules to connect to the network
-
Allow HTTPD scripts and modules to network connect to databases
-
Allow HTTPD scripts to write files in directories labeled public_content_rw_t (similar to FTP)
-
Allow HTTPD to read home directories
-
Allow HTTPD to run as an FTP server
-
Allow HTTPD to run SSI executables in the same domain as system CGI scripts
-
Allow HTTPD to support built-in scripting
-
Disable SELinux protection for httpd daemon
-
Disable SELinux protection for httpd suexec (executable files run by the HTTPD service)
-
Unify HTTPD handling of all content files
-
Unify HTTPD to communicate with the terminal; needed for handling certificates
Kerberos
There are three options in this section. One allows other daemons to use Kerberos files (enabled by default). The other two options disable protection for the Kerberos administrative daemon (kadmind) and the Kerberos key control daemon (krb5kdc).
Memory Protection
The memory protection options are not related to any services or systems cited in the current version of the Red Hat Exam Prep guide.
Mount
The settings in this category relate to the automount service; you can configure it to allow the automounter to mount any directory or file, as well as disable SELinux protection for this service.
Name Service
The Name Service daemon (named) is the RHEL DNS service. If you maintain a zone, you'll probably want to allow the named daemon to overwrite master zone files. You can also disable SELinux protection for named as well as the name services cache daemon (ncsd).
NFS
Before using NFS with SELinux, you'll want to enable at least the reading of NFS file systems. If you're sharing with NFS, you'll also want to enable read/ write/create on an NFS file system. If you configure home directories on a server and share them with NFS, you'll also want to support NFS home directories. There's also support for the General Security Services daemon, gssd.
NIS
If you want to run NIS on a SELinux system, you'll want to allow daemons to run with NIS. You can disable SELinux protection for the NIS password and NIS transfer daemons. If all else fails, you can disable SELinux protection for the associated daemon, ypbind.
Other
These miscellaneous options can allow full file access via FTP and unlabeled packets. They can also disable SELinux protection for PC Card readers and specialized time zone data.
Polyinstatiation
Polyinstatiation is a mouthful; it means different users may see different things when looking at the same directory, such as /tmp. You can enable this support in the SELinux tool.
pppd
The pppd daemon governs communication primarily over telephone modems. You can allow pppd to insert modules in the kernel, which supports communication, or disable SELinux protection for this daemon.
Printing
This section allows you to disable SELinux protection for the different CUPS-related daemons, including the CUPS back-end server, the cupsd daemon, the cupsd-lpd service, and the HP imaging (hplip) daemon. You can even enable the use of LPD instead of CUPS.
rsync
The rsync section allows you to configure writes to directories where the public_content_rw_t type context is assigned, as described earlier in the chapter. You can also disable SELinux protection for this daemon.
Samba
There are several ways you can modify SELinux protections for Samba. The options are straightforward:
-
Allow Samba to share nfs directories.
-
Allow Samba to share users' home directories.
-
Allow Samba to write files in directories labeled public_content_rw_t.
-
Allow users to log in with CIFS home directories.
-
Disable SELinux protection for nmbd daemon (the NetBIOS daemon).
-
Disable SELinux protection for smbd daemon (the Samba daemon).
-
Disable SELinux protection for winbind daemon (the WINS server daemon).
SASL Authentication Server
The simple authentication and security layer (SASL) server is another authentication method; with the Security Level Configuration tool, you can allow it access to your /etc/shadow authentication database, and disable SELinux protection for the related daemon.
| On the Job | As of this writing, there are categories for the "sasl authentication server" and "sasl authentications server." This is a mistake related to bug 231868 documented at https://bugzilla.redhat.com. |
SELinux Service Protection
The SELinux Service Protection category allows you to disable SELinux protection for a wide variety of daemons, from amanda to zebra. These services are not already configured in other categories.
Spam Protection
The Spam Protection category works with the SpamAssassin service. Access to home directories is required for regular users. Of course, you can also disable SELinux protection for this service.
SQUID
If you want to set up the Squid Web Proxy cache, discussed in Chapter 9, you'll want to allow it to access the network. And you can disable SELinux protection for this service.
Universal SSL Tunnel
If you configure a secure tunnel for network communication, you can configure additional protection with SELinux. You can use this tool to allow stunnel to run as a stand-alone service and disable SELinux protection.
Zebra
You can use this tool to let the Zebra routing service write to routing tables.
File Labeling
You can change the default labels associated with files, some of which are described earlier in this chapter (and in other chapters discussing SELinux contexts). Some of the options are shown in Figure 15-6.
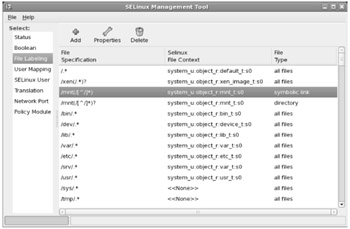
Figure 15-6: SELinux Management File Labeling
User Mapping
The User Mapping section allows you to go beyond the defaults for regular and administrative users.
SELinux User
The SELinux User section allows you to specify default roles for standard users, such as regular users (user_u), system users (system_u), and the administrative root user.
Translation
The Translation section allows you to customize sensitivity levels.
Network Port
The Network Port section associates standard ports to services.
Policy Module
The Policy Module section specifies the SELinux policy version number applied to each module.
The Setroubleshoot Browser
If you have problems with SELinux, it may not be obvious. For example, if you have a problem with Samba, you may not even see an error message; if you do, it may not be clear whether you've forgotten to add the right password to the Samba authentication database or if SELinux is blocking access. You could analyze the log files, but that can be difficult for those newer to SELinux.
Red Hat has added the Setroubleshoot Browser shown in Figure 15-7. It provides tips and advice on any problems that you may encounter, in a language more Linux administrators can understand, often including commands that you can run and that will address the subject problem.
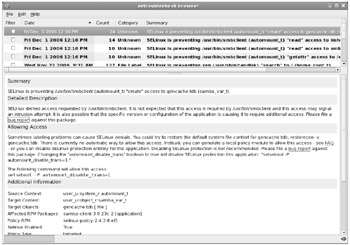
Figure 15-7: SELinux Setroubleshoot Browser
To start the Setroubleshoot Browser from the GNOME desktop, click System | Administration | SELinux Troubleshooter; or run sealert -b from a GUI-based command line. There are other options associated with sealert, which you can review by running the sealert -h command.
EAN: 2147483647
Pages: 227