Routing Between VLANs
The main reason for the creation of a VLAN is to keep traffic within local workgroups. We have already mentioned in this book that you can not communicate between VLANs without a router (layer 3 device), so understanding the configuration of VLANs and understanding routing need to go hand in hand in order to understand the full process of inter-VLAN communications.
Route processors provide the communication that hosts need between VLANs. However, if you are using local VLANs (see Chapter 3, “VLANs, Trunks, and VTP” for a thorough explanation), a good rule of thumb is to design your networks so at least 80 percent of the users’ traffic does not cross over into another VLAN. Therefore, you should design the network so that the users have access to local servers and other needed resources to prevent excessive packets from crossing the route processor.
It is worth repeating that many network card vendors nowadays make NICs that can understand ISL and 802.1Q encapsulated packets. When attempting to keep a large percentage of traffic from straying from the local VLAN, these cards can be very useful. Fitting a server with an ISL or 802.1Q-aware NIC means that the server can be a member of multiple VLANs and connect to a switch via a trunk link.
Example scenarios include installing one of these NICs in an e-mail server or a database server. Anything that a large number of people, across several VLANs, need to access is a candidate for this type of connection. It often makes more fiscal sense to upgrade a server NIC than to upgrade an entire router.
Cisco recommends that VLANs should be configured one for one with IP subnet designs. This means that you need to create a subnet design for your network taking into account the needs of the various VLANs. If you are using VLSM, this is pretty straightforward, but if for some reason you are constrained to a single subnet mask, you may need to select the mask first and then design your VLANs around the subnet design. For example, if you have engineering, marketing, sales, and support departments, you will typically—not always, but typically—create a subnet for each department, making sure you have room for growth. You would then create a VLAN for each department. In Chapter 3, we discussed the differences between local and end-to-end VLANs. Regardless of the type of VLAN you configure, each of these types would be associated with a subnet.
The route processor managing the inter-VLAN routing would have multiple interfaces (real or virtual) and each would have an IP address in the subnet associated with the interface VLAN. Each device within a VLAN would have a default gateway of the IP address of the inter-VLAN device connected to its VLAN. The inter-VLAN device would then route any packets with a destination not on the local network.
Before configuring routing between your VLANs, you need to understand the type of data sharing that is needed. By understanding the user and business needs, you can design the network with load balancing and/or redundant links if needed.
When configuring routing, you can choose from three options:
-
Multiple links
-
A single trunk link
-
An internal or external route processor
Tip VLSM (Variable Length Subnet Masking) is a technique designed to create flexible subnets and get the most from your available IP address space. It is covered in detail in the CCNP: Building Scalable Cisco Internetworks Study Guide, by Carl Timm and Wade Edwards (Sybex, 2003).
Multiple Links
You can configure your VLANs to inter-communicate by connecting a separate router interface into separate switch ports that are configured for each VLAN. Each workstation in the VLAN would have its default gateway configured for the physical router interface’s own VLAN/subnet. Figure 6.1 shows how this might look in an internetwork.
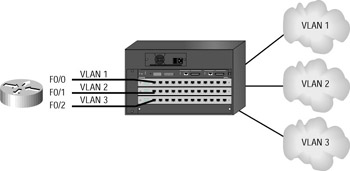
Figure 6.1: Routers with multiple links
This is a perfectly workable solution for small networks, but it does not scale well when you have more than a few VLANs. It depends on the type of router you have. For every VLAN, you need to have a router interface (typically FastEthernet or Gigabit Ethernet), so a larger, more expensive router can have more interfaces without being saturated—but sooner rather than later, you will run out of physical interfaces.
The more VLANs you have, the more router interfaces you have to purchase with the router. Also, you should have a fast router such as a high-end (at least a 4700 or 7200 series) router that can route quickly so the router does not become a bottleneck. Cost then becomes the issue with multiple links, and the possible requirement for multiple or redundant route-processors doubles the cost.
Using multiple links is not a desirable thing to do in most cases, but there are times when it might be the only solution. The alternate solutions—using a trunk, for example—require Fast Ethernet at the least. Trunks do not run over 10Mbits/second Ethernet. So if you have some routers with only slower Ethernet interfaces, such as the 2500 series, then you would be able to effect inter-VLAN routing with one of those—albeit quite slowly.
A Single Trunk Link
Another possible solution to routing between VLANs is creating a trunk link on a switch and then using a frame-tagging protocol such as ISL or 802.1Q (which are used to identify VLAN/ frame relationships as they traverse FastEthernet and Gigabit Ethernet links) on the router. Cisco calls this solution “router on a stick.”
Figure 6.2 shows how the internetwork might look with a single trunk link for all VLANs.
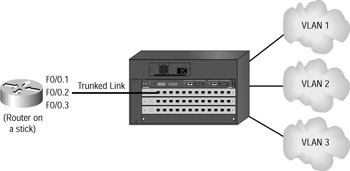
Figure 6.2: Single trunk link for all VLANs
This solution uses only one router interface on the router, but it also puts all the traffic on one interface. You really have to have a fast router to do this. Also, to even perform this function, you need, at minimum, a FastEthernet interface on a 2600 series router. ISL does not work on 10BaseT interfaces, nor would you want to run this on 10BaseT because it is processor- and bandwidth-intensive.
An Internal Route Processor
An internal route processor is a router on a card that fits inside the switch. This enables a switch to route packets without having the packets leave the box that the switch resides in. You need to add an internal route processor to a layer 2 device—for example, a 4000 Catalyst switch—to be able to provide forwarding of layer 3 packets without an external router.
Adding an internal route processor makes a layer 2 switch into a multi-layer switch and can integrate layer 2 and layer 3 (and possibly layer 4) functionality in a single box. The 4000 series uses a Layer 3 Switching Module (L3SM), and the 6000 series uses the Multi-layer Switch Module (MSM) and the Multi-layer Switch Feature card (MSFC) to perform this function. The MSM and MSFC (and older RSMs and RSFCs) are configured in exactly the same way on older switches.
The 4000 series router module (WS-X4232-L3) consists of a 4GB routing switch fabric with 4GB interfaces. Two of these gigabit connections appear on the front panel, making externally accessible gigabit router ports, while the two remaining ports are connected internally to the switch backplane. (There are also 32 10/100M ports, which are standard layer 2 ports and not linked into the routing fabric.)
Most of the time, ports 3 and 4 are configured as part of the same channel and subinterfaces are added as needed using either ISL or 802.1q encapsulation. The configuration of gigabit ports 3 and 4 on the router module must be consistent with the configuration of port slot/1 and slot/2 on the switch.
| Tip | The traffic flow between the module and the switch can be seen using the global commands show interface port-channel or show interface gigabit. |
The L3SM is plugged directly into the switch, and runs the Cisco IOS in order to perform inter-VLAN communication. The 4000 series switch sees the RSM as a single trunked port with a single MAC address. In other words, it appears as a router on a stick to the switch.
Internal Routing on an IOS-Based Switch
More recently, an entirely new method for inter-VLAN switching has emerged. The migration of Cisco switches over to IOS has meant that a new generation of switches is equipped with native routing capabilities. Not only are these faster than those switches with additional daughter boards or routing cards, but they support a variety of enhanced features that we will examine later in the book, such as QoS (quality of service) and layer 3 switching.
EAN: 2147483647
Pages: 174