FIREWALL
FIREWALL? WHERE'S THE FIRE?The Annoyance:I have antivirus software running on every computer on my network, so why do I need a firewall? Buying and installing all this stuff is annoying. The Fix:Antivirus software and firewalls are two different animals, and they protect you from two different types of attacks. Antivirus software locates and eliminates viruses, which are destructive programs sneaked on to your computer (usually through your email). A firewall protects you from attacks by ne'er-do-wells who are trying to enter your computer while you're on the Internet. Because evildoers use both methods of attack, you need both forms of protection. WINDOWS XP FIREWALL HALTS NETWORK TRAFFICThe Annoyance:I added a Windows XP computer to our network. The Help files tell me how important it is to have a firewall on the computer, and they explain how to enable the built-in firewall. However, friends tell me that if I use the built-in firewall, none of the other computers on the network will be able to access the Windows XP computer. Why would an important tool such as a firewall not work on a network? The Fix:Your friends are right. The firewall built into Windows XP stops network communications (unless you're running Windows XP Service Pack 2). Isn't that an interesting way to design an operating system feature? Maybe Microsoft doesn't know about the explosive growth of small networks.
If the firewall has been automatically enabled (which occurs frequently when you use the Internet Connection Wizard in Windows XP), you should disable it. Open the Properties dialog box for the Local Area Connection, click the Advanced tab, and make sure the box in the Internet Connection Firewall area is unchecked (see Figure 7-1). Then install a software firewall or a firewall-enabled router (if you're using a router to share your Internet connection). Figure 7-1. Disable the Windows XP Internet Connection Firewall if you're running a network.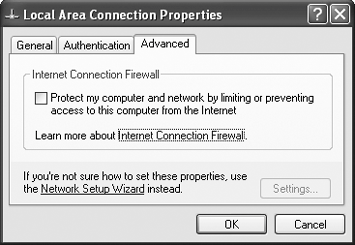 WINDOWS XP SERVICE PACK 2 OFFERS IMPROVED FIREWALLThe Annoyance:Our Windows XP computer is running Service Pack 2, and the advertising blurbs say the new firewall lets you have a network. I enabled the firewall, but other computers still can't access the XP machine. What happened? The Fix:With SP2, Microsoft added setup options to the built-in firewall. To let network computers access this computer, use the following steps:
Figure 7-2. Enable network communications by making an exception to the firewall's data blocking. It's beyond the scope of this book to discuss all the security settings available in Windows XP Service Pack 2, including the firewall. However, you should investigate some of the other firewall settings that allow you to use the Remote Assistance and Remote Desktop features. The Help files for SP2 provide instructions and explanations. You'll also need to configure the firewall if you want to play Internet games or take part in online conferences. SHARED TELEPHONE MODEMS NEED FIREWALLSThe Annoyance:Our network uses Internet Connection Sharing to share a telephone modem. Do I have to have a firewall on every computer on the network? The Fix:Nope, you only need to protect the computer that has the modem (the host computer). The host is a gateway, and a firewall on the gateway guards the computers on the network side of the gateway like Cerberus guards the entrance into the underworld.
WINDOWS XP FIREWALL FOR BROADBAND-BASED ICSThe Annoyance:We have a cable modem, but we didn't buy a router. Instead, we attached the cable modem to a Windows XP computer and set it up as an ICS host. Can I use the built-in Windows XP firewall to protect the entire network? The Fix:Yes, but make sure you enable it on the right network adapter. To share a cable modem (or a DSL modem) without a router, the host computer has two network adapters: one connects to the hub where the other computers meet and the other connects to the modem. Enable the built-in firewall on the adapter connected to the modem. SAFEGUARDING OLDER COMPUTERSThe Annoyance:The four computers on our network share a router without a firewall. Two of the computers, however, run Windows XP SP2 and use the built-in firewall. The other two computers run Windows 2000 Professional and 98SE. Do they have a version of the built-in firewall? The Fix:No, you'll have to install a software firewall on the computers running Windows 2000 Professional and 98SE. I use ZoneLabs' ZoneAlarm, and for most home networks the freebie version of ZoneAlarm does the job. Another well-known software firewall is Internet Security Systems' Black Ice. Symantec and McAfee, best known for their antivirus software, also offer good firewall programs.
ROUTERS CAN PROTECT YOUR NETWORKThe Annoyance:We use a router with a built-in firewall for shared Internet access. Do I still have to install firewall software on all the computers on the network? The Fix:No, the router blocks malicious intruders at the gateway, which protects all the computers on the network. Warning: Most hardware-based firewalls block only incoming traffic. This approach doesn't provide bidirectional security (see "Software Firewalls Go Both Ways"). STATEFUL INSPECTION CAN TELL WHO'S LYINGThe Annoyance:We're considering adding a router with a firewall to our network. Some of the routers say they use "stateful inspection." Is this an important feature worth paying for? The Fix:Stateful inspection is a firewall technique that makes sure the data coming through the firewall is truthfully describing itself. Different types of data use different virtual ports on a computer, and a firewall lets data come through some ports and closes other ports. For example, a stateful inspection firewall will make sure that the data that uses the HTTP port (the protocol of Internet web pages) is really HTTP, and not some dangerous programming code. Because Internet hackers don't announce their data packets with a reference that says "there's dangerous stuff in this data packet even though it says it's HTTP," stateful inspection is important. (If you're curious about the technical stuff, see the sidebar "Ports and Data.")
SOFTWARE FIREWALLS GO BOTH WAYSThe Annoyance:Some people tell me that a software firewall is preferable to the Windows XP firewall or a firewall on a router. Isn't blocking data from the Internet the same thing no matter which type of firewall you use? I mean, either the data is allowed through or it isn't; who cares what type of firewall does the blocking? The Fix:Your logic is impeccable. If you want to block unwanted data trying to get to your computer from the Internet, a firewall is a firewall is a firewall. But hold on a minute. You talked about blocking data trying to get into your computer. What about data trying to get out? Can you think of times that you don't want to send data to another computer on the Internet? No? Well, suppose you pick up a virus that gathers your files and sends them to some hacker's computer? Suppose you download a really nifty software program or game and you don't know that it's programmed to send sensitive and private information to some punk who will use it to steal your identity, or use your cookies to gain access to a web site that has your credit card numbers. Most hardware firewalls worry only about incoming data streams; they don't give a hoot about stuff moving from your computer to the Internet. Software firewalls ask your permission before letting any software send data from your computer to the Internet. Tip: You can configure some hardware firewalls to protect you from unwanted outward-bound data transmissions. However, you usually have to know a lot of technical gunk to get the configuration right. Play it safe and go with a software firewall. STOP FIREWALL POP-UP NOTIFICATIONSThe Annoyance:The software firewall I installed on all the computers on our network drives everyone crazy. A pop-up appears every few minutes to announce that the firewall has blocked access to the computer from the Internet. I would rather risk an intruder than have to click OK to clear the pop-up window every couple of minutes. The Fix:Don't worry; you can stop the pop-ups. But aren't you amazed at how often somebody tries to access your computer? The thought that some or most of those attempts are attacks is scary. All software firewalls offer an option to suppress the pop-up notifications about incoming data streams, and you usually have the option to save the information to a log file. Check the Help files to learn the exact steps. DON'T BLOCK OUTGOING FIREWALL POP-UP NOTIFICATIONSThe Annoyance:Every so often, my firewall software opens a pop-up message to ask me whether some program can send information to the Internet. It's always OK because the program needs to get to the Internet (for instance, it's the Microsoft Help Files program). Is there a way to turn off the notifications? The Fix:Your firewall asks for permission when it doesn't know how you feel about a specific program. By default, most software firewalls assume you want to let your browser access the Internet, so they configure themselves to permit the browser to send data without asking your permission. Any other program that isn't on the list requires your permission. When you give permission for a program to access the Internet, always select the option to give the program permanent permission. Then you'll never be asked again. You can also preconfigure your firewall with the names of programs (in addition to your browser) that should automatically be allowed to send data from your computer. Check the Help files to learn how to add programs to the list of preapproved data senders. APPROVED OUTGOING PROGRAMS ASK FOR PERMISSION AGAINThe Annoyance:My antivirus and accounting software both check the vendors' web sites periodically for updates. I configured the firewall to let these programs access the Internet, and selected the option to make it a permanent permission. Today, the firewall asked me if the accounting software could access the Internet. Doesn't the firewall have the same definition of "permanent" that I do? The Fix:The program changed and your firewall is asking permission again to make sure it's OK to let the changed program send data from your computer to the Internet. In fact, you can probably find a note on the pop up that says the program has changed since the last time you gave it permission to send data to the Internet. Programs change when you download upgrades to the software, and for both antivirus and accounting software programs, this is a frequent event. The firewall's approach is a good protection scheme because it prevents the possibility that some virus or other maleficent program is using the name of an existing software program to accomplish some horrific deed. If you didn't recently upgrade the software, don't give permission. CHECK THE PROGRAM BEFORE YOU GIVE PERMISSIONThe Annoyance:Sometimes my firewall pop up tells me that some program is trying to exchange data with another computernot with the Internet. In fact, sometimes the pop up warns me that the program is asking for server rights. This sounds very scary. The Fix:Some programs, mostly utilities built into Windows, are designed to implement network tasks. For example, you might see a pop-up reference to Generic Host Process for Win32 (which lets computers on the network access each other) or to the Spooler Service (which lets you send data to a remote printer). Most of the program names contain a reference to Microsoft or Windows, but do some homework (search the Internet or search Microsoft's web sites) before you give permission. WHICH COMPUTERS SHOULD HAVE A SOFTWARE FIREWALL?The Annoyance:We've decided on a software firewall for our network. Do I have to install a copy on every computer on the network? The Fix:Maybe yes, maybe no. If your computers directly access the Internet through a router (without a built-in firewall), each computer needs a copy of the firewall. If you're using ICS, only the computer that hosts the Internet connection needs a firewall. TEST THE FIREWALLThe Annoyance:How can you tell whether the firewall works properly? The Fix:Test it. Several web sites exist for testing firewall effectiveness. One of the best is from Gibson Research Corporation (www.grc.com/). To test your firewall, click the Shields Up! link on the home page, and then scroll down the page and click the Shields Up! link. Click the Proceed button to begin the test. Select the tests you want to run (File Sharing and Common Ports are the most important). GRC attempts all sorts of tricks to break into your computer and then posts its results. You can see the results of my File Sharing test in Figure 7-3, and the results of my Common Ports test in Figure 7-4. If you don't see similar results when you test your computer, you need to reconfigure your firewall. Figure 7-3. My firewall is taking care of file security. Figure 7-4. Secured ports keep intruders out of my computer. |
EAN: 2147483647
Pages: 90