Restricting Web Server Communication
The following example shows you how to use IPSec to limit communication with a Web server to port 80 (for HTTP traffic) and port 443 (for HTTPS traffic that uses SSL.) This is a common requirement for Internet- facing Web servers.
| Note | After applying the steps below, communication will be limited to port 80 and 443. In a real world environment, you will require additional communication such as that required for remote administration, database access and authentication. A complete IPSec policy, in a production environment, will include all authorized communication. |
Task Create filter actions
-
Start the Local Security Policy Microsoft Management Console (MMC) snap-in.
-
Right-click IPSec Security Policies on Local Machine , and then click Manage IP filter lists and filter actions .
-
Click the Manage Filter Actions tab.
-
Click Add to create a new filter action, and then click Next to move past the introductory Wizard dialog box.
-
Type MyPermit as the name for the new filter action. This filter action is used to permit traffic.
-
Click Next .
-
Select Permit , click Next , and then click Finish .
-
Create a second filter action called "MyBlock" by repeating steps 4 to 8. This time, select Block when you are prompted by the Filter Action dialog box.
-
Click Close to close the Manage IP filter lists and filter actions dialog box.
Task Create IP filters and filter lists
-
Right-click IPSec Security Policies on Local Machine , and then click Manage IP filter lists and filter actions .
-
Click Add to add a new IP filter list., and then type MatchAllTraffic for the filter list name.
-
Click Add to create a new filter and proceed through the IP Filter Wizard dialogs boxes by selecting the default options.
This creates a filter that matches all traffic.
-
Click Close to close the IP Filter List dialog box.
-
Click Add to create a new IP filter list, and then type MatchHTTPAndHTTPS for the filter list name.
-
Click Add , and then click Next to move past the introductory Wizard dialog box.
-
Select Any IP Address from the Source address drop-down list, and then click Next .
-
Select My IP Address from the Destination address drop-down list, and then click Next .
-
Select TCP from the Select a protocol type drop-down list, and then click Next .
-
Select To this port and then specify port 80 .
-
Click Next and then Finish .
-
Click Add , and then repeat steps 9 to 14 to create another filter that allows traffic through port 443.
Use the following values to create a filter that allows TCP over port 443:
-
Source Address: Any IP address
-
Destination Address: My IP Address
-
Protocol: TCP
-
From Port: Any
-
To Port: 443
-
After finishing these steps, your IP Filter List should look like the one that Figure 5 shows.
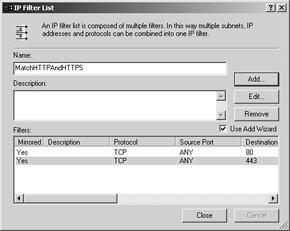
Figure 5: IP Filter List dialog box
After creating the filter actions and filter lists, you need to create a policy and two rules to associate the filters with the filter actions.
Task Create and apply IPSec policy
-
In the main window of the Local Security Policy snap-in, right-click IPSec Security policies on Local Machine , and then click Create IPSecurity Policy .
-
Click Next to move past the initial Wizard dialog box.
-
Type MyPolicy for the IPSec policy name and IPSec policy for a Web server that accepts traffic to TCP/80 and TCP/443 from anyone for the description, and then click Next .
-
Clear the Activate the default response rule check box, click Next , and then click Finish .
The MyPolicy Properties dialog box is displayed so that you can edit the policy properties.
-
Click Add to start the Security Rule Wizard, and then click Next to move past the introductory dialog box.
-
Select This rule does not specify a tunnel , and then click Next .
-
Select All network connections , and then click Next .
-
Select Windows 2000 default (Kerberos V5 protocol) , and then click Next .
-
Select the MatchHTTPAndHTTPS filter list, and then click Next .
-
Select the MyPermit filter action, click Next , and then click Finish .
-
Create a second rule by repeating steps 5 to 10. Instead of selecting MatchHTTPAndHTTPS and MyPermit , select MatchAllTraffic and MyBlock .
After creating the second rule, the MyPolicy Properties dialog box should look like the one in Figure 6.
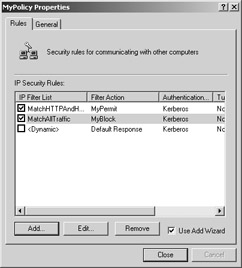
Figure 6: MyPolicy Properties dialog box
Your IPSec policy is now ready to use. To activate the policy, right-click MyPolicy and then click Assign .
Summary of What You Just Did
In the previous three procedures, you performed these actions:
-
You started by creating two filter actions: one to allow traffic and one to block traffic.
-
Next, you created two IP filter lists. The one called MatchAllTraffic matches on all traffic, regardless of port. The one called MatchHTTPAndHTTPS contains two filters that match TCP traffic from any source address to TCP ports 80 and 443.
-
Then you created an IPSec policy by creating a rule that associated the MyBlock filter action with the MatchAllTraffic filter list and the MyPermit filter action with the MatchHTTPAndHTTPS filter list. The result of this is that the Web server only allows TCP traffic destined for port 80 or 443. All other traffic is rejected.
EAN: 2147483647
Pages: 613