Threats and Countermeasures
An attacker can target and compromise a database server in a number of ways by exploiting a variety of configuration and application level vulnerabilities.
The main threats to a database server are:
-
SQL injection
-
Network eavesdropping
-
Unauthorized server access
-
Password cracking
Figure 18.1 shows the major threats and vulnerabilities that can result in a compromised database server and the potential destruction or theft of sensitive data.
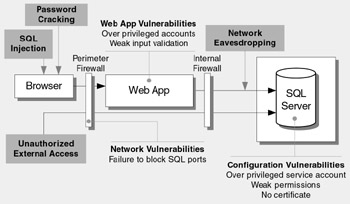
Figure 18.1: Top database server threats and vulnerabilities
The next sections describe each of these threats and vulnerabilities.
SQL Injection
With a SQL injection attack, the attacker exploits vulnerabilities in your application's input validation and data access code to run arbitrary commands in the database using the security context of the Web application.
Vulnerabilities
Vulnerabilities exploited by SQL injection include:
-
Poor input validation in your Web applications
-
Unsafe, dynamically constructed SQL commands
-
Over-privileged application logins to the database
-
Weak permissions that fail to restrict the application's login to the database
Countermeasures
To counter SQL injection attacks:
-
Your application should constrain and sanitize input data before using it in SQL queries.
-
Use type safe SQL parameters for data access. These can be used with stored procedures or dynamically constructed SQL command strings. Using SQL parameters ensures that input data is subject to type and length checks and also that injected code is treated as literal data, not as executable statements in the database.
-
Use a SQL Server login that has restricted permissions in the database. Ideally, you should grant execute permissions only to selected stored procedures in the database and provide no direct table access.
For more information about application-level countermeasures to SQL injection attacks, see Chapter 14, "Building Secure Data Access."
Network Eavesdropping
The deployment architecture of most applications includes a physical separation of the data access code from the database server. As a result, sensitive data, such as application-specific data or database login credentials, must be protected from network eavesdroppers.
Vulnerabilities
Vulnerabilities that increase the likelihood of network eavesdropping include:
-
Insecure communication channels
-
Passing credentials in clear text to the database; for example:
-
Using SQL authentication instead of Windows authentication
-
Using SQL authentication without a server certificate
-
Countermeasures
To counter network eavesdropping:
-
Use Windows authentication to connect to the database server to avoid sending credentials over the network.
-
Install a server certificate on the database server. This results in the automatic encryption of SQL credentials over the network.
-
Use an SSL connection between the Web server and database server to protect sensitive application data. This requires a database server certificate.
-
Use an IPSec encrypted channel between Web and database server.
Unauthorized Server Access
Direct access to your database server should be restricted to specific client computers to prevent unauthorized server access.
Vulnerabilities
Vulnerabilities that make your database server susceptible to unauthorized server access include:
-
Failure to block the SQL Server port at the perimeter firewall
-
Lack of IPSec or TCP/IP filtering policies
Attacks
Direct connection attacks exist for both authenticated users and those without a user name and password; for example:
-
Tools such as Query Analyzer (Isqlw.exe) or the command line equivalent (Osql.exe) are used to establish a direct connection to SQL Server and issue commands.
-
Server information, such as software version, is revealed to an attacker who sends carefully constructed packets to listening ports.
Countermeasures
To counter these attacks:
-
Make sure that SQL Server ports are not visible from outside of the perimeter network.
-
Within the perimeter, restrict direct access by unauthorized hosts , for example, by using IPSec or TCP/IP filters.
Password Cracking
A common first line of attack is to try to crack the passwords of well known account names , such as sa (the SQL Server administrator account).
Vulnerabilities
Common vulnerabilities that lead to password cracking are:
-
Weak or blank passwords
-
Passwords that contain everyday words
Attacks
Common password cracking attacks include:
-
Dictionary attacks
-
Manual password guessing
Countermeasures
To counter these attacks:
-
Create passwords for SQL Server login accounts that meet complexity requirements.
-
Avoid passwords that contain common words found in the dictionary.
Note If you use Windows authentication, password complexity can be enforced by Windows security policy.
EAN: 2147483647
Pages: 613