Firewall Considerations
Your security infrastructure can include internal firewalls on either side of the application server. This section discusses the ports that you open on these firewalls to support the functionality of your application.
Enterprise Services
If you use middle- tier Enterprise Services, configure an internal firewall that separates the Web server and application server to allow DCOM and RPC traffic. Additionally, if you use Enterprise Services, your applications often use distributed transactions and the services of the Distributed Transaction Coordinator (DTC). In this event, open DTC ports on any firewall that separates the application server from remote resource managers, such as the database server. Figure 17.3 shows a typical Enterprise Services port configuration.
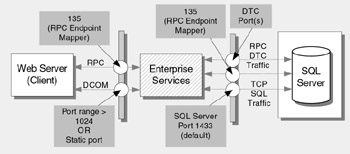
Figure 17.3: Typical Enterprise Services firewall port configuration
| Note | Figure 17.3 does not show the additional ports that are required for authentication mechanisms between a client and an Enterprise Services application and possibly between the Enterprise Services application and the database server. Commonly, for networks that do not use Active Directory, TCP port 139 is required for Windows authentication. For more information on port requirements, see the TechNet articles "TCP and UDP Port Assignments," at http://www.microsoft.com/technet/prodtechnol/ windows2000serv/reskit/tcpip/part4/tcpappc.asp , and "Security Considerations for Administrative Authority," at http://www.microsoft.com/technet/security/bestprac/bpent/sec2/seconaa.asp . |
By default, DCOM uses RPC dynamic port allocation, which randomly selects port numbers above 1024. In addition, port 135 is used by the RPC endpoint mapping service.
Restrict the ports required to support DCOM on the internal firewall in two ways:
-
Define port ranges .
This allows you to control the ports dynamically allocated by RPC. For more information about dynamic port restrictions, see Microsoft Knowledge Base article 300083, "How To: Restrict TCP/IP Ports on Windows 2000 and Windows XP."
-
Use static endpoint mapping .
Microsoft Windows 2000 SP3 (or QFE 18.1 and later) or Windows Server 2003 allows you to configure Enterprise Services applications to use a static endpoint. Static endpoint mapping means that you only need to open two ports in the firewall: port 135 for RPC and a nominated port for your Enterprise Services application.
For more information about static endpoint mapping, see Microsoft Knowledge Base article 312960, "Cannot Set Fixed Endpoint for a COM+ Application."
Web Services
If you cannot open ports on the internal firewall, then you can introduce a Web-services fa §ade layer in front of the serviced components on the application server. This means that you only need to open port 80 for HTTP traffic ( specifically , SOAP messages) to flow in both directions.
This approach does not allow you to flow transaction context from client to server, although in many cases where your deployment architecture includes a middle-tier application server, it is appropriate to initiate transactions in the remote serviced component on the application server.
For information about physical deployment requirements for service agents and service interfaces, such as the Web-services fa §ade layer, see "Physical Deployment and Operational Requirements" in the Reference section of MSDN article, "Application Architecture for .NET: Designing Applications and Services," at http://msdn.microsoft.com/library/default.asp?url=/library/en-us/dnbda/html/distapp.asp .
DTC Requirements
If your application uses COM+ distributed transactions and these are used across remote servers separated by an internal firewall, then the firewall must open the necessary ports to support DTC traffic. The DTC uses RPC dynamic port allocation. In addition to port 135 for RPC, DTC communication requires at least one additional port.
If your deployment architecture includes a remote application tier, transactions are normally initiated there within the Enterprise Services application and are propagated to the database server. In the absence of an application server, the Enterprise Services application on the Web server initiates the transaction and propagates it to the SQL Server resource manager.
For information about configuring firewalls to support DTC traffic, see:
-
"DTC Security Considerations" in the COM+ platform SDK at http://msdn.microsoft.com/library/default.asp?url=/library/en-us/cossdk/htm/pgdtc_admin_9dkj.asp
-
Microsoft Knowledge Base article 250367, " INFO : Configuring Microsoft Distributed Transaction Coordinator (DTC) to Work Through a Firewall."
-
Microsoft Knowledge Base article 306843, "How To: Troubleshoot MS DTC Firewall Issues."
.NET Remoting
If you use the HTTP channel and host your remote components in ASP.NET, only open port 80 on the internal firewall to allow HTTP traffic. If your application also uses SSL, open port 443.
If you use the TCP channel and host in a Windows service, open the specific TCP port or ports that your Remoting application has been configured to use. The application might need an additional port to support callbacks.
Figure 17.4 shows a typical .NET Remoting firewall port configuration. Note that the port numbers shown for the TCP channel scenario (5555 and 5557) are illustrations. The actual port numbers are specified in web.config configuration files on the client and server machines. For more information, see Chapter 13, "Building Secure Remoted Components."
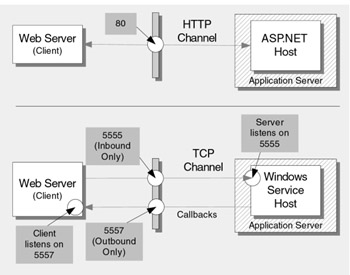
Figure 17.4: Typical Remoting firewall port configuration for HTTP and TCP channel scenarios
Web Services
Web services communicate using SOAP over HTTP; therefore, only open port 80 on the internal firewall.
SQL Server
If a firewall separates the application server from the database server, then connecting to SQL Server through a firewall requires that you configure the client using the SQL Server Client Network Utility and configure the database server using the Server Network Utility. By default, SQL Server listens on TCP port 1433, although this can be changed. The chosen port must be open at the firewall.
Depending on the chosen SQL Server authentication mode and use of distributed transactions by your application, you might also need to open several additional ports at the firewall:
-
If your application uses Windows authentication to connect to SQL Server, open the necessary ports that support the Kerberos protocol or NTLM authentication.
-
If your application uses distributed transactions, for example automated COM+ transactions, configure your firewall to allow DTC traffic to flow between separate DTC instances, and between the DTC and resource managers, such as SQL Server.
For more information on SQL Server port requirements, see Chapter 18, "Securing Your Database Server."
EAN: 2147483647
Pages: 613