Identify Threats
You need to know your threats before you can successfully apply security measures. Threats can be external, such as from an attacker on the Internet, or internal ” for example, from a disgruntled employee or administrator. This guide helps you to identify threats in two ways:
-
It lists the top threats that affect Web applications at the network, host, and application layers .
-
It presents a threat modeling process to help you identify which threats are relevant to your application.
An outline of the threat modeling process covered in the guide is shown in Figure 4.
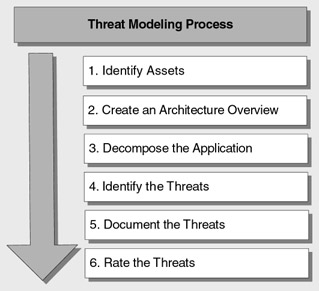
Figure 4: The Threat Modeling Process
The steps shown in Figure 4 are described below:
-
Identify assets .
Identify the assets of value that your systems must protect.
-
Create an architecture overview .
Use simple diagrams and tables to document the architecture of your application, including subsystems, trust boundaries, and data flow.
-
Decompose the application .
Decompose the architecture of your application, including the underlying network and host infrastructure design, to create a security profile for the application. The aim of the security profile is to uncover vulnerabilities in the design, implementation, or deployment configuration of your application.
-
Identify the threats .
Keeping an attacker's goals in mind, and with knowledge of your application's architecture and potential vulnerabilities, you identify the threats that could impact the application.
-
Document the threats .
Document each threat using a common threat template that defines a core set of attributes that you should capture for each threat.
-
Rate the threats .
Rate the threats to prioritize and address the most significant threats first. These threats are the ones that present the biggest risk. The rating process weighs the probability of the threat against the damage that could result should an attack occur. It might turn out that certain threats do not warrant any action when you compare the risk posed by the threat with the resulting mitigation costs.
EAN: 2147483647
Pages: 613