Threats and Countermeasures
The fact that an attacker can strike remotely makes a Web server an appealing target. Understanding threats to your Web server and being able to identify appropriate countermeasures permits you to anticipate many attacks and thwart the ever-growing numbers of attackers .
The main threats to a Web server are:
-
Profiling
-
Denial of service
-
Unauthorized access
-
Arbitrary code execution
-
Elevation of privileges
-
Viruses, worms, and Trojan horses
Figure 16.1 summarizes the more prevalent attacks and common vulnerabilities.
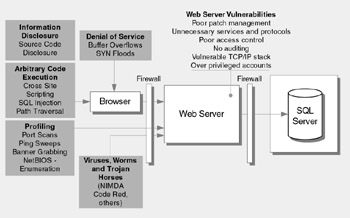
Figure 16.1: Prominent Web server threats and common vulnerabilities
Profiling
Profiling, or host enumeration, is an exploratory process used to gather information about your Web site. An attacker uses this information to attack known weak points.
Vulnerabilities
-
Common vulnerabilities that make your server susceptible to profiling include:
-
Unnecessary protocols
-
Open ports
-
Web servers providing configuration information in banners
Attacks
Common attacks used for profiling include:
-
Port scans
-
Ping sweeps
-
NetBIOS and server message block (SMB) enumeration
Countermeasures
Countermeasures include blocking all unnecessary ports, blocking Internet Control Message Protocol (ICMP) traffic, and disabling unnecessary protocols such as NetBIOS and SMB.
Denial of Service
Denial of service attacks occur when your server is overwhelmed by service requests. The threat is that your Web server will be too overwhelmed to respond to legitimate client requests .
Vulnerabilities
Vulnerabilities that increase the opportunities for denial of service include:
-
Weak TCP/IP stack configuration
-
Unpatched servers
Attacks
Common denial of service attacks include:
-
Network-level SYN floods
-
Buffer overflows
-
Flooding the Web server with requests from distributed locations
Countermeasures
Countermeasures include hardening the TCP/IP stack and consistently applying the latest software patches and updates to system software.
Unauthorized Access
Unauthorized access occurs when a user without correct permissions gains access to restricted information or performs a restricted operation.
Vulnerabilities
Common vulnerabilities that lead to unauthorized access include:
-
Weak IIS Web access controls including Web permissions
-
Weak NTFS permissions
Countermeasures
Countermeasures include using secure Web permissions, NTFS permissions, and .NET Framework access control mechanisms including URL authorization.
Arbitrary Code Execution
Code execution attacks occur when an attacker runs malicious code on your server either to compromise server resources or to mount additional attacks against downstream systems.
Vulnerabilities
Vulnerabilities that can lead to malicious code execution include:
-
Weak IIS configuration
-
Unpatched servers
Attacks
Common code execution attacks include:
-
Path traversal
-
Buffer overflow leading to code injection
Countermeasures
Countermeasures include configuring IIS to reject URLs with "../" to prevent path traversal, locking down system commands and utilities with restrictive access control lists (ACLs), and installing new patches and updates.
Elevation of Privileges
Elevation of privilege attacks occur when an attacker runs code by using a privileged process account.
Vulnerabilities
Common vulnerabilities that make your Web server susceptible to elevation of privilege attacks include:
-
Over-privileged process accounts
-
Over-privileged service accounts
Countermeasures
Countermeasures include running processes using least privileged accounts and using least privileged service and user accounts.
Viruses, Worms, and Trojan Horses
Malicious code comes in several varieties, including:
-
Viruses . Programs that are designed to perform malicious acts and cause disruption to an operating system or applications.
-
Worms . Programs that are self-replicating and self- sustaining .
-
Trojan horses . Programs that appear to be useful but that actually do damage.
In many cases, malicious code is unnoticed until it consumes system resources and slows down or halts the execution of other programs. For example, the Code Red worm was one of the most notorious to afflict IIS, and it relied upon a buffer overflow vulnerability in an ISAPI filter.
Vulnerabilities
Common vulnerabilities that make you susceptible to viruses, worms, and Trojan horses include:
-
Unpatched servers
-
Running unnecessary services
-
Unnecessary ISAPI filters and extensions
Countermeasures
Countermeasures include the prompt application of the latest software patches, disabling unused functionality such as unused ISAPI filters and extensions, and running processes with least privileged accounts to reduce the scope of damage in the event of a compromise.
EAN: 2147483647
Pages: 613
- Tips for Standard GUI Practices and Forms Development
- Intersession and Interdatabase Communication from Forms
- Preventing Validation of WHEN-VALIDATE-ITEM for Control Items During Query Time
- Techniques for Querying and Updating New Data Sources in Forms Based on Objects
- A New Look at Relations Using REFS
- Chapter III Two Models of Online Patronage: Why Do Consumers Shop on the Internet?
- Chapter IV How Consumers Think About Interactive Aspects of Web Advertising
- Chapter V Consumer Complaint Behavior in the Online Environment
- Chapter VI Web Site Quality and Usability in E-Commerce
- Chapter X Converting Browsers to Buyers: Key Considerations in Designing Business-to-Consumer Web Sites