.NET Framework Security Namespaces
To program .NET Framework security, you use the types in the .NET Framework security namespaces. This section introduces these namespaces and the types that you are likely to use when you develop secure Web applications. For a full list of types, see the .NET Framework documentation. The security namespaces are listed below and are shown in Figure 6.3.
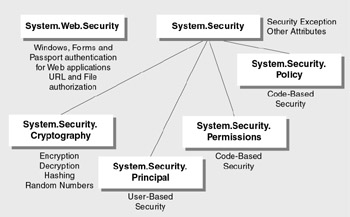
Figure 6.3: .NET Framework security namespaces
-
System.Security
-
System.Web.Security
-
System.Security.Cryptography
-
System.Security.Principal
-
System.Security.Policy
-
System.Security.Permissions
System.Security
This namespace contains the CodeAccessPermission base class from which all other code access permission types derive. You are unlikely to use the base class directly. You are more likely to use specific permission types that represent the rights of code to access specific resource types or perform other privileged operations. For example, FileIOPermission represents the rights to perform file I/O, EventLogPermission represents the rights for code to access the event log, and so on. For a full list of code access permission types, see Table 6.2 later in this chapter.
The System.Security namespace also contains classes that encapsulate permission sets. These include the PermissionSet and NamedPermissionSet classes. The types you are most likely to use when building secure Web applications are:
-
SecurityException . The exception type used to represent security errors.
-
AllowPartiallyTrustedCallersAttribute . An assembly-level attribute used with strong named assemblies that must support partial trust callers . Without this attribute, a strong named assembly can only be called by full trust callers ( callers with unrestricted permissions.)
-
SupressUnmanagedSecurityAttribute . Used to optimize performance and eliminate the demand for the unmanaged code permission issued by the Platform Invocation Services (P/Invoke) and Component Object Model (COM) interoperability layers . This attribute must be used with caution because it exposes a potential security risk. If an attacker gains control of unmanaged code, he is no longer restricted by code access security. For more information about using this attribute safely, see "Unmanaged Code" in Chapter 8, "Code Access Security in Practice."
System.Web.Security
This namespace contains the classes used to manage Web application authentication and authorization. This includes Windows , Forms, and Passport authentication and URL and File authorization, which are controlled by the UrlAuthorizationModule and FileAuthorizationModule classes, respectively. The types you are most likely to use when you build secure Web applications are:
-
FormsAuthentication . Provides static methods to help with Forms authentication and authentication ticket manipulation.
-
FormsIdentity . Used to encapsulate the user identity that is authenticated by Forms authentication.
-
PassportIdentity . Used to encapsulate the user identity that is authenticated by Passport authentication.
System.Security.Cryptography
This namespace contains types that are used to perform encryption and decryption, hashing, and random number generation. This is a large namespace that contains many types. Many encryption algorithms are implemented in managed code, while others are exposed by types in this namespace that wrap the underlying cryptographic functionality provided by the Microsoft Win32 -based CryptoAPI.
System.Security.Principal
This namespace contains types that are used to support role-based security. They are used to restrict which users can access classes and class members . The namespace includes the IPrincipal and IIdentity interfaces. The types you are most likely to use when building secure Web applications are:
-
GenericPrincipal and GenericIdentity . Allow you to define your own roles and user identities. These are typically used with custom authentication mechanisms.
-
WindowsPrincipal and WindowsIdentity . Represents a user who is authenticated with Windows authentication together with the user's associated Windows group (role) list.
System.Security.Policy
This namespace contains types that are used to implement the code access security policy system. It includes types to represent code groups, membership conditions, policy levels, and evidence.
System.Security.Permissions
This namespace contains the majority of permission types that are used to encapsulate the rights of code to access resources and perform privileged operations. The following table shows the permission types that are defined in this namespace (in alphabetical order).
| Permission | Description |
|---|---|
| DirectoryServicesPermission | Required to access Active Directory. |
| DNSPermission | Required to access domain name system (DNS) servers on the network. |
| EndpointPermission | Defines an endpoint that is authorized by a SocketPermission object. |
| EnvironmentPermission | Controls read and write access to individual environment variables. It can also be used to restrict all access to environment variables . |
| EventLogPermission | Required to access the event log. |
| FileDialogPermission | Allows read-only access to files only if the file name is specified by the interactive user through a system-provided file dialog box. It is normally used when FileIOPermission is not granted. |
| FileIOPermission | Controls read, write, and append access to files and directory trees. It can also be used to restrict all access to the file system. |
| IsolatedStorageFilePermission | Controls the usage of an application's private virtual file system (provided by isolated storage). Isolated storage creates a unique and private storage area for the sole use by an application or component. |
| IsolatedStoragePermission | Required to access isolated storage. |
| MessageQueuePermission | Required to access Microsoft Message Queuing message queues. |
| OdbcPermission | Required to use the ADO.NET ODBC data provider. (Full trust is also required.) |
| OleDbPermission | Required to use the ADO.NET OLE DB data provider. (Full trust is also required.) |
| OraclePermission | Required to use the ADO.NET Oracle data provider. (Full trust is also required.) |
| PerformanceCounterPermission | Required to access system performance counters. |
| PrincipalPermission | Used to restrict access to classes and methods based on the identity and role membership of the user. |
| PrintingPermission | Required to access printers. |
| ReflectionPermission | Controls access to metadata. Code with the appropriate ReflectionPermission can obtain information about the public, protected, and private members of a type. |
| RegistryPermission | Controls read, write, and create access to registry keys (including subkeys). It can also be used to restrict all access to the registry. |
| SecurityPermission | This is a meta-permission that controls the use of the security infrastructure itself. |
| ServiceControllerPermission | Can be used to restrict access to the Windows Service Control Manager and the ability to start, stop, and pause services. |
| SocketPermission | Can be used to restrict the ability to make or accept a connection on a transport address. |
| SqlClientPermission | Can be used to restrict access to SQL Server data sources. |
| UIPermission | Can be used to restrict access to the clipboard and to restrict the use of windows to "safe" windows in an attempt to avoid attacks that mimic system dialog boxes that prompt for sensitive information such as passwords. |
| WebPermission | Can be used to control access to HTTP Internet resources. |
The SecurityPermission class warrants special attention because it represents the rights of code to perform privileged operations, including asserting code access permissions, calling unmanaged code, using reflection, and controlling policy and evidence, among others. The precise right determined by the SecurityPermission class is determined by its Flags property, which must be set to one of the enumerated values defined by the SecurityPermissionFlags enumerated type (for example, SecurityPermissionFlags.UnmanagedCode ).
EAN: 2147483647
Pages: 613