The WorldWide WarDrive Is Born
|
| < Day Day Up > |
|
Since The Watcher and I had decided to WarDrive Baltimore together, I thought it would be fun to see if anyone else might be interested in driving with us. There were several people on the NetStumbler Forums that were interested in coming along. Renderman decided to try to do a drive of Red Deer, Canada on the same day. He and I discussed the idea of a “World Stumbling Day” in which people all over the world would WarDrive their areas on the same day.
WorldWide WarDrive 1
I posted this “World Stumbling Day” idea in the DefCon Forums to see if there might be any interest from the members; there was. By this time, there were several people that wanted to WarDrive their area. We chose August 31, 2002 for our WarDrive date. I didn’t care for the term World Stumbling Day and decided that WorldWide WarDrive had a better sound. I posted information about the WorldWide WarDrive on my Web site, Security Tribe (www.securitytribe.com). We needed some way to let people know what areas were involved, and how many people were planning to participate. I put up a guestbook-type message board for people to use for signing up and coordinating. Throughout the next week, I received several e-mails from people that were interested but didn’t want to post their e-mail addresses or locations on a public message board. I decided to move all of the coordination to the WarDriving mailing list (http://mailsrv.dis.org/_mailman/listinfo/wardriving) where people could make arrangements in a more private forum.
Organization
At this point, I knew that I needed to put some sort of page up with general information about the event. Word had started to circulate and a general buzz was growing about the event, particularly in the computer underground. I posted a page that had each of the areas that were being coordinated and the coordinator’s contact information. There were only about six or seven coordinators on this page when it was first posted. That number grew to ten by the day of the event.
I had done absolutely no promotion for the first WorldWide WarDrive other than a general announcement on the WarDriving mailing list and the existing posts on the NetStumbler and DefCon Forums. The idea was spreading by word of mouth through the underground. One thing people should understand about the WorldWide WarDrive is that I intentionally leave organization of the individual areas up to the local organizers. I don’t have a “press kit” or anything with a prefabricated press release for people to use. For the first WorldWide WarDrive, I only offered up basic guidance on local organization. That was primarily based around making sure that people didn’t attach to any networks that were discovered. I also let each local organizer know that he was responsible for getting a merged data set to me. Organizers were asked to send me either a merged NetStumbler .ns1 file or a wi-scan dump with extensions. I would then collate the data and manually generate the statistical analysis.
The organizers from Canada, Renderman and JJKaczor, thought it would be a good idea to send a press release out to the Canadian press. This was an idea that I completely disagreed with. I am not a person that enjoys doing interviews or any kind of self-promotion. This is not from some sense of modesty. There are three primary reasons for my standoffishness with the press.
-
I don’t like taking credit for other people’s accomplishments. The WorldWide WarDrive is collaboration. I can’t do it by myself. A lot of people work very hard to ensure that the event goes off without a hitch (or at least as few hitches as possible). The press tends to like using words such as “founder” and “organizer.” This gives me a lot more credit than I deserve.
-
The press has a tendency to point out primarily the negative aspects of any so-called “underground” event.
-
I have become gun-shy when it comes to the press after watching the way they have twisted quotes from me and other collaborators in past interviews regarding DefCon.
I pointed these issues out to Renderman and JJKaczor and strongly cautioned them against issuing a general press release. They felt that it was important to send something out though, and did. This was a decision they would later come to regret as you will see in the Lessons Learned section.
The Canadian press release did have an impact on the participation in the WorldWide WarDrive. After a few Canadian papers and news Web sites picked the story up, there was even more notice taken of the event in the United States. American papers and Web sites were quoting and mirroring the Canadian stories and interest in the event picked up dramatically. One of the most important things that came from the Canadian press release was that the Chicago, Illinois group Deadtech (www.deadtech.net) became aware of the event and volunteered to organize Chicago. These guys really knew how to organize. Unlike other organizers in other cities (including me), these guys didn’t just choose a meeting place and time. Deadtech put together a complete class on how to WarDrive, encouraged people who didn’t understand WarDriving to come and learn what it was all about and even tag along with more experienced people. They also planned a big post-WarDrive party for everyone to get together afterwards. They have done this for every WorldWide WarDrive and that probably explains why they have consistently had one of the best turnouts.
As August 31st approached, I was paying attention to the weather forecasts and noticed that thunderstorms were expected in Baltimore. Driving in the rain is not fun; let alone WarDriving in the rain. I contacted a few of the people that were planning to attend and asked them what they thought about postponing our drive until the following Saturday. The general consensus was that no one wanted to drive in the rain, so the announcement was made that the Baltimore drive would be one week after most of the other areas. Although at the time this was a decision based solely on the weather, it turned out to be a major decision in how the WorldWide WarDrive would be organized from that point forward. Since we were now extending the WorldWide WarDrive over an entire week, people started e-mailing me to ask if they could submit data for each day as opposed to only on the 31st. I decided that the WorldWide WarDrive would be the entire week. Each subsequent WorldWide WarDrive has been a week-long event.
On the evening of the 31st, the organizers began e-mailing me their results. I continued to receive results from them for the next few days. On September 4th, 2002, the WorldWide WarDrive would change forever. I was in Washington, D.C. doing some work when my cell phone rang. I was in a meeting so I turned it off. About an hour later, I left the meeting and turned the phone back on to find that I had missed fourteen calls, most of them from Russ. I called him back before I checked my voicemail to try to find out what the emergency was. He told me that the Security Tribe Web server was being hit with a Distributed Denial-of-Service (DDoS) attack. I told him to log in and shut the Web server down and that I would check on it when I got home. As it turned out, it wasn’t a DDoS per se. It was what I have come to call an “Industry-Induced Denial-of-Service Attack.”
Unbeknownst to me, Slashdot had run a story about the WorldWide WarDrive (http://slashdot.org/articles/02/09/04/1238219.shtml). Because Security Tribe is a medium-traffic Web site even during the busiest times, I had set the concurrent connections threshold to 100. Slashdot has a very large readership, and many of its patrons clicked the link that was provided to the Security Tribe Web site. This caused the server to be overloaded. Later that evening, I tried turning the Web server back on, but the connections immediately hit 100. Again, because Security Tribe is a hobby server, I didn’t have the type of service plan that would allow many more connections than that and I didn’t feel comfortable increasing the threshold. I ended up leaving the server offline for about a day and a half, long enough for the story to be replaced on the Slashdot front page.
For the most part, the Slashdotting was a frustration, but not a major issue. My mail server still worked and I could access the box remotely. It did generate a lot of awareness for the event though, and I began to receive e-mails from WarDrivers asking if they could submit their data from that week even if they hadn’t participated in an organized area drive. I decided that any data that was collected during the week of the WorldWide WarDrive could be submitted even if an organized drive wasn’t attended. This is a policy that has been maintained throughout the history of the WorldWide WarDrive.
Lessons Learned
The first WorldWide WarDrive was an eyeopener in many ways. I had no idea that the event would generate the amount of interest from the WarDriving community and the press that it did. I quickly realized that if I wanted to do future WorldWide WarDrives, it would need its own identity. Most of the reaction from the WarDriving community was positive and people seemed to be interested in doing it again. I purchased the domain www.worldwidewardrive.org so that I could move information about the WorldWide WarDrive off of Security Tribe, which was not a wireless security site but rather a general security site and repository for whitepapers I had written, as well as presentations I had given in the past.
Many of the drives were organized simply by taking a city map and cutting it into sections; giving each driver a piece of the map. This is a completely ineffective way to plan a WarDrive. Many drivers that participated found themselves in areas that were unsavory to say the least. Low income, urban areas were dangerous to drive in. Also, when people are struggling to pay for their food, it is highly unlikely that they are spending money to deploy wireless networks. I knew that before we did this again, steps had to be taken to maximize the effectiveness of the drives.
What completely surprised me was the reaction from the Information Security community. The SANS Institute, in their weekly News Bites, negatively portrayed the event. Their September 9, 2002 edition carried the following story "Wardriving Reveals Lack of LAN Security.”
“A week-long worldwide wardrive revealed that many wireless LANs (local area networks) don’t employ even basic security. A New Jersey–based company is selling complete wardriving kits. A consultant for the company observed that wardriving is legal and has legitimate uses. [Editor’s Note (Murray): it is legal to look in your neighbor’s open window but nice people do not do it. There is no more corrupting idea than the current one that that which is legal is, ipso facto, ethical.]”
www.computerworld.com/mobiletopics/
mobile/story/0,10801,74103,00.html
www.computerworld.com/mobiletopics/
mobile/story/0,10801,74102,00.html
Another surprise was the reaction of the Canadian Security Intelligence Service (CSIS). After hearing of the WorldWide WarDrive from the press release issued by Renderman and JJKaczor, the CSIS opened an investigation into the two of them and the WorldWide WarDrive. Their investigation discovered no malicious intent or actions and was quickly closed. The lesson was learned that if a press release is going to be issued, statements such as participants will be “converging on” an area should be avoided.
This brings me to the main lesson learned from the first WorldWide WarDrive. If you are going to engineer an event such as this that has the potential to be controversial, it is important to state the goals up-front. I had not done this with the first WorldWide WarDrive. It was put together relatively quickly, and spawned from a small group of friends getting together to drive one city. I didn’t realize that it would be perceived in a negative way by anyone. This was addressed with the second WorldWide WarDrive.
Stumbler Code of Ethics
Even though the FAQ addressed most of the things I wanted people to know about the WWWD, I thought it was important to create a general set of guidelines to address the ethical behavior that should be adhered to by WarDrivers. These guidelines apply not only during the WorldWide WarDrive but anytime they go out WarDriving. I asked Renderman if he would be willing to assemble this for inclusion on the WorldWide WarDrive page. He agreed and the Stumbler Code of Ethics was born.
These are by no means rules that must be followed, but they are a collection of suggestions for safe, ethical, and legal stumbling. I encourage you to follow them.
-
Obey traffic laws. It’s your community, too. Traffic laws are there for everyone’s safety—besides, doing doughnuts at 3 a.m. are rewarded with unwanted attention from the authorities.
-
Obey private property and no-trespassing signs. Don’t trespass in order to scan an area—that’s what the directional antenna is for. You wouldn’t want people trespassing on your property, would you?
-
Don’t connect. The vast majority of APs out there were not intended by their owners to be accessed by you, even if they configured it so you could access it if you wanted to. There is much legal question as to the trouble you can get into for accessing a network through a misconfigured AP. Also, it’s a matter of respect—you wouldn’t want people rooting through your computers just because you happened to make a mistake, so don’t do it to them.
-
Don’t use your data for personal gain. Share the data with like-minded people, show it to people who can change things for the better, but don’t try and make any money or status off your data. It’s just wrong to expect these people to reward you for pointing out their own stupidity.
-
Don’t warchalk other people’s networks. Only chalk your own if you want to indicate your willingness to share access. If you chalk some stranger’s network, it dilutes the use of the symbols to indicate free access. If you’re a business and you have both a public AP and a non-public one, indicate which is the open one, but also indicate the closed one with the closed symbol, differentiating them so people know the difference.
-
Observe that old hiker motto “Take only pictures, leave only footprints” and adapt it as your own. Thus, stumblers should “Take only SSIDs, leave only tire marks.” Leaving tire marks by not loitering and moving on is better than leaving a log entry by doing something stupid.
Statistics from WorldWide WarDrive 1
When all was said and done, over a hundred WarDrivers participated in the first WorldWide WarDrive. Twenty-two areas were represented in six countries on two continents (North America and Europe). There were eight categories of statistics generated. I compiled and generated all of the statistics by hand, as shown in Table 8.1.
| CATEGORY | TOTAL | PERCENT |
|---|---|---|
| TOTAL APs FOUND | 9374 | 100 |
| WEP Enabled | 2825 | 30.13 |
| No WEP Enabled | 6549 | 69.86 |
| Default SSID | 2768 | 29.53 |
| Default SSID and No WEP | 2497 | 26.64 |
| Unique SSIDs | 3672 | 39.17 |
| Most Common SSID | 1778 | 18.97 |
| Second Most Common SSID | 623 | 6.65 |
WorldWide WarDrive 2
Almost immediately after the first WorldWide WarDrive, I started getting e-mails from people wanting to know when the next one would take place. Most of these were from people that heard about the first one from media stories after it had ended and wanted to participate in future drives. Renderman contacted me and asked if it would be possible to have another WorldWide WarDrive before the weather got too bad in Canada and parts of the U.S. I decided that it would be worthwhile to have another WorldWide WarDrive before the end of the year to capitalize on the interest that had been generated from the first one while it was still fresh in people’s minds.
Organization
After checking the calendar, I chose October 26th through November 2nd, 2002 for the dates of the second WorldWide WarDrive (WWWD2). Before announcing the dates for the WWWD2, I knew that I could avoid some of the problems of the first one by clearly stating the goals of the event up-front. I decided that the easiest way to do this would be to put a Frequently Asked Questions (FAQ) section up on the WorldWide WarDrive Web site (www.worldwidewardrive.org/faq.html). I ended up putting the FAQ on the front page of the Web site, right under the announcement of the WWWD2 dates, until after the WWWD2 was over.
The FAQ was a good idea. It allowed me to address many of the issues that people didn’t understand. The first two FAQ items address what the WWWD is and what the goals are.
-
What is the WorldWide WarDrive? The WorldWide WarDrive is an effort by security professionals and hobbyists to generate awareness of the need by individual users and companies to secure their access points.
-
The goal of the WorldWide WarDrive (or WWWD) is to provide a statistical analysis of the many access points that are currently deployed.
-
What do you hope to accomplish? We feel that many end users are not aware that the factory or “default” settings on access points do not take any security measures into account. By providing these statistics, we hope that end users will become aware of the need to take simple measures to secure their access points.
As soon as the dates were announced on the Web site and the FAQ had been put up, I e-mailed the announcement to the WarDriving and Kismet mailing lists. Then I posted the announcement on the NetStumbler Forums, the Kismet Forums, and the DefCon Forums. That was the extent of the “promotion” done for the WWWD2. There was no general press release sent out, as I wanted to avoid any inaccurate and sensationalist stories being released.
I sent a general e-mail out to the organizers letting them know that I would accept their data from October 26th until November 9th, 2002 but that only data sets containing data collected between October 26th and November 2nd would be counted. This gave organizers a week to combine the data from their areas before sending it to me. Again, the organizers would need to send me their combined data by e-mail so that I could combine it into the master file for statistical analysis. I also sent this information to the mailing lists and posted it on the FAQ. This was so that people who did not participate in an organized drive but still wanted to submit their data would have the opportunity to do so.
Once the dates were announced and people started planning their drives, I needed to address the issue of maximizing the results of the WarDrive. I decided that rather than drive Baltimore again, I would organize Annapolis, the state capitol of Maryland. I got in touch with ffrf, one of the participants from the first WWWD in Baltimore and asked for his help with this problem. He developed a program that would take income data from the latest census and generate color-coded maps to note the income levels for a specific area using MapBlast (www.ffrf.net/maps/annapolis-small-mb-overlay-labels.png).
Converting the Data
Since not all of the WarDrivers were using NetStumbler (which makes it very easy to convert data to wi-scan format with extensions), we needed to get the organizers a standardized way to convert Kismet data to the proper format. Tim McGuffin and ffrf had combined their efforts and developed a conversion program that would allow the organizers to convert data. I provided this program to the organizers so that they could easily convert the data before they sent it to me.
#!/usr/bin/perl ## Medic's kismet to extended wi-scan converter ## Current as of: August 26, 2002 $csvfilename = $ARGV[0]; $cwgdfilename = $ARGV[1]; if (!defined $csvfilename) {print "USAGE:./convert.pl CSVFILE CWGDFILE\ nYou are missing the CSV File\n"; exit} if (!defined $cwgdfilename) {die "USAGE:./convert.pl CSVFILENAME CWGDFILE\nYou are missing the CWGD File\n";exit} open(CSVFILE,$csvfilename) or die "Can't open CSV file"; while (<CSVFILE>) { chomp; next if /^$/; next if /^#/; @temp = split(";"); # for $x (0 .. 20){ # $csvarray[$csvcount][$x] = $temp[$x]; # } #HASH $temp[3] = lc($temp[3]); $ssidhash{$temp[3]} = $temp[2]; $networktypehash{$temp[3]} = $temp[1]; $channelhash{$temp[3]} = $temp[5]; $wephash{$temp[3]} = $temp[7]; #/HASH $csvcount++ } print "# \$Creator: Kismet to wi-scan 0.6 by Medic\n"; print "# \$Format: wi-scan\n"; print "# Latitude\tLongitude\t( SSID )\tType\t( BSSID )\tTime (GMT)\t[SNR Sig Noise ]\t# ( Name )\tFlags\tChannelbits\tBcnIntvl\n"; print "# \$DateGMT:\n"; open(CWGDFILE,$cwgdfilename) or die "Can't open CWGD file"; while (<CWGDFILE>) { chomp; next if /^$/; next if /^#/; @cwgdarray = split(/\t/); if ($cwgdarray[0] ne "00:00:00:00:00:00") { $bssid =lc($cwgdarray[0]); $latitude = $cwgdarray[2]; $longitude = $cwgdarray[3]; $findtime = $cwgdarray[10]; $signal = $cwgdarray[8]; $noise = $cwgdarray[9]; $snr = $signal - $noise; $bcnintvl = 100; GetInfo($bssid); FixChannel(); FixNetwork(); FixDate(); FixFlags(); FixCoords(); print "$latitude\t$longitude\t( $ssid )\t$networktype\t( $bssid )\t$findtime (GMT)\t[ $snr $signal $noise ]\t# ( )\t$flags\t$channelbits\t$bcnintvl\n"; } } sub FixCoords{ if ($latitude =~ /^\-/i){ @templat = split(/\-/i,$latitude); $latitude = @templat[1]; $latitude = "S " . $latitude; } else { $latitude = "N " . $latitude; } if ($longitude =~ /^\-/i){ @templon = split(/\-/i,$longitude); $longitude = @templon[1]; $longitude = "W " . $longitude; } else { $longitude = "E " .$longitude; } } sub FixFlags{ $wepbit = "0"; $ntypebit = "0"; if ($wep eq "Yes") {$wepbit = "1"} if ($networktype eq "BBS") {$ntypebit = "1"} else {$ntypebit = "2"} $flags = "00" . $wepbit . $ntypebit; } sub FixDate{ @junk = split(" ",$findtime); $findtime = $junk[3]; } sub FixNetwork{ if ($networktype eq "infrastructure" or $networktype eq "probe") {$networktype = "BBS"} else {$networktype = "Ad-hoc"} } sub FixChannel{ $channelbits = "0000"; if ($channel eq "00") {$channelbits = "0001"} if ($channel eq "01") {$channelbits = "0002"} if ($channel eq "02") {$channelbits = "0004"} if ($channel eq "03") {$channelbits = "0008"} if ($channel eq "04") {$channelbits = "0010"} if ($channel eq "05") {$channelbits = "0020"} if ($channel eq "06") {$channelbits = "0040"} if ($channel eq "07") {$channelbits = "0080"} if ($channel eq "08") {$channelbits = "0100"} if ($channel eq "09") {$channelbits = "0200"} if ($channel eq "10") {$channelbits = "0400"} if ($channel eq "11") {$channelbits = "0800"} } sub GetInfo($bssid) { # $y = 0; # for $y (0 .. $#csvarray){ # if ($bssid eq lc($csvarray[$y][3])) { # $ssid = $csvarray[$y][2]; # $networktype = $csvarray[$y][1]; # $channel = $csvarray[$y][5]; # $wep = $csvarray[$y][7]; # } # $y++; # } #HASH $ssid = $ssidhash{$bssid}; $networktype = $networktypehash{$bssid}; $channel = $channelhash{$bssid}; $wep = $wephash{$bssid}; #/HASH }
Lessons Learned
The second WorldWide WarDrive was probably the most trying of all of them. Attempting to put a second WorldWide WarDrive together so quickly after the first was a mistake. I still had not developed an automated way to generate the statistics and getting the results together was difficult. The initial press reaction was also quite negative. The amount of press that was generated for the WWWD2 was quite a bit larger than the first. By the time the results were released, the number of positive stories and negative stories had evened out quite a bit. That was encouraging, but I still felt that the press did not understand my goal with the project and realized that something would have to be done to address that before another WWWD could take place.
There were a lot of people interested in organizing their areas and if anyone contacted me with an e-mail address or Web page stating that they wanted to do some organizing, I posted their information. There were some cases where I didn’t check their contact page before posting it on the organizer site (www.worldwidewardrive.org/wwwd2/organizers.html). Two problems resulted from this:
-
Some people volunteered to organize but because I didn’t query them at all, I didn’t realize that they were not trustworthy. There were several people that signed up as area organizers for the WWWD2 that never submitted their data. In fact, most of these people ignored my repeated e-mails asking for their data so I don’t know if people participated but their data was never submitted, or if the organizer never got together with other drivers.
-
More disturbing, one wireless security company tried to generate business by using their corporate Web page as the organizer site. Their page had only been listed on the organizer site for two days before I checked it out and removed it. I knew that I would have to specifically address this issue before another WorldWide WarDrive could take place.
Statistics from the WorldWide WarDrive 2
Despite the problems, I still consider the WWWD2 a success. Over 200 people participated (twice as many as the first WWWD) in 32 areas, representing seven countries on four continents. I dropped the statistic for Unique SSIDs from the analysis for two reasons. First, because I was still generating the statistics manually and there were so many more access points found than the first WWWD, it was just not feasible. Second, I had received feedback that the Unique SSID statistic wasn’t very useful. Table 8.2 reflects this.
| CATEGORY | TOTAL | PERCENT |
|---|---|---|
| TOTAL APs FOUND | 24958 | 100 |
| WEP Enabled | 6970 | 27.92 |
| No WEP Enabled | 17988 | 72.07 |
| Default SSID | 8802 | 35.27 |
| Default SSID and No WEP | 7847 | 31.44 |
| Most Common SSID | 531 | 21.28 |
| Second Most Common SSID | 2048 | 8.21 |
WorldWide WarDrive 3
Almost immediately after WWWD2, I started getting e-mails asking about the next WorldWide WarDrive. I still hadn’t recovered from the second at this point and wasn’t even sure if there would even be a third. I either ignored these e-mails or replied letting people know that when the dates for the next one were decided they would be announced on the WarDriving and Kismet mailing lists, and on the NetStumbler, DefCon, and Kismet forums. I decided to take a few months and not think about the WWWD. By the time 2003 had rolled around, I had received enough inquiries that I realized the event had to go on. I am glad that it did, because the third WorldWide WarDrive (WWWD3) was, without a doubt, the most successful.
Organization
The first two WorldWide WarDrives had showed me a lot about how not to do things. Before I announced the WWWD3, I wanted to address some of these problems rather than just repeat them. Most of the problems with the first WWWD were addressed in some way during the organization of the WWWD2, but the WWWD2 revealed a whole new set of issues that needed to be taken care of; most of these were more serious than those from the first WWWD. With the WWWD3, I undertook the greatest planning, preparation, and organization of any WWWD to date. I wanted the event to both run smoothly and get the message out to the right people at the right time.
The first thing I needed to do was standardize the data upload process. I contacted ffrf again and asked if he would be willing to write a Web-based application that would allow for automated upload of the data from either individuals or the coordinators. I needed something that would accept only NetStumbler .ns1 files. I also wanted the data quarantined so that uploaded data would not be accessible by the public. I didn’t want someone to be able to access and download the .ns1 files from the server. This is because it has never been my objective to post or make public individual .ns1’s or data on individual access points but rather give a snapshot of the wireless networks deployed at the time of the event. Since this was a relatively easy application to write, ffrf agreed and provided me with the following PHP script:
<html> <head> <? ////////////////////////////////////////// ////////////////////////////////////////// //CONFIGURATION $upload_dir = "/usr/home/chris/wwwd3/"; $admin_email_addy = "roamer@worldwidewardrive.org"; ////////////////////////////////////////// ////////////////////////////////////////// function isValidEmail($address, $checkMX = false) { $valid_tlds = array("arpa", "biz", "com", "edu", "gov", "int", "mil", "net", "org", "ad", "ae", "af", "ag", "ai", "al", "am", "an", "ao", "aq", "ar", "as", "at", "au", "aw", "az", "ba", "bb", "bd", "be", "bf", "bg", "bh", "bi", "bj", "bm", "bn", "bo", "br", "bs", "bt", "bv", "bw", "by", "bz", "ca", "cc", "cf", "cd", "cg", "ch", "ci", "ck", "cl", "cm", "cn", "co", "cr", "cs", "cu", "cv", "cx", "cy", "cz", "de", "dj", "dk", "dm", "do", "dz", "ec", "ee", "eg", "eh", "er", "es", "et", "fi", "fj", "fk", "fm", "fo", "fr", "fx", "ga", "gb", "gd", "ge", "gf", "gh", "gi", "gl", "gm", "gn", "gp", "gq", "gr", "gs", "gt", "gu", "gw", "gy", "hk", "hm", "hn", "hr", "ht", "hu", "id", "ie", "il", "in", "io", "iq", "ir", "is", "it", "jm", "jo", "jp", "ke", "kg", "kh", "ki", "km", "kn", "kp", "kr", "kw", "ky", "kz", "la", "lb", "lc", "li", "lk", "lr", "ls", "lt", "lu", "lv", "ly", "ma", "mc", "md", "mg", "mh", "mk", "ml", "mm", "mn", "mo", "mp", "mq", "mr", "ms", "mt", "mu", "mv", "mw", "mx", "my", "mz", "na", "nc", "ne", "nf", "ng", "ni", "nl", "no", "np", "nr", "nt", "nu", "nz", "om", "pa", "pe", "pf", "pg", "ph", "pk", "pl", "pm", "pn", "pr", "pt", "pw", "py", "qa", "re", "ro", "ru", "rw", "sa", "sb", "sc", "sd", "se", "sg", "sh", "si", "sj", "sk", "sl", "sm", "sn", "so", "sr", "st", "su", "sv", "sy", "sz", "tc", "td", "tf", "tg", "th", "tj", "tk", "tm", "tn", "to", "tp", "tr", "tt", "tv", "tw", "tz", "ua", "ug", "uk", "um", "us", "uy", "uz", "va", "vc", "ve", "vg", "vi", "vn", "vu", "wf", "ws", "ye", "yt", "yu", "za", "zm", "zr", "zw"); // Rough email address validation using POSIX-style regular expressions if (!eregi("^[a-z0-9_]+@[a-z0-9\-]{2,}\.[a-z0-9\-\.]{2,}$", $address)) return false; else $address = strtolower($address); // Explode the address on name and domain parts $name_domain = explode("@", $address); // There can be only one ;-) I mean... the "@" symbol if (count($name_domain) != 2) return false; // Check the domain parts $domain_parts = explode(".", $name_domain[1]); if (count($domain_parts) < 2) return false; // Check the TLD ($domain_parts[count($domain_parts) - 1]) if (!in_array($domain_parts[count($domain_parts) - 1], $valid_tlds)) return false; // Searche DNS for MX records corresponding to the hostname ($name_domain[0]) if ($checkMX && !getmxrr($name_domain[0], $mxhosts)) return false; return true; } function make_clean($value) { // if ( preg_match( ‘/[^a-zA-Z0-9\/_.-]/', $page_param ) ) { $legal_chars = "%[^0-9a-zA-Z ]%"; //allow letters, numbers & space $new_value = preg_replace($legal_chars,"",$value); //replace with "" return $new_value; } function make_clean_email($value) { // $legal_chars = "%[^0-9a-zA-Z ]%"; //allow letters, numbers & space // $new_value = preg_replace($legal_chars,"",$value); //replace with "" $new_value = str_replace(‘@', ‘-', $value); return $new_value; } if (($_FILES[‘img1'] != "") && ($_POST[‘handle'] != "") && (isValidEmail($_POST[‘email']))) { $today = date("y.m.d.G.i.s"); //Year.Month.Day.Hour.Minute.Second $user_handle = make_clean($_POST[‘handle']); $user_email = $_POST[‘email']; $user_conf = $_POST[‘conf']; $user_addr = $_SERVER[‘REMOTE_ADDR']; $user_filesize = $_FILES[‘img1'][‘size']; $friendlyemail = make_clean_email($_POST[‘email']); $prettyfilename = $today."_".$user_handle."_".$friendlyemail.".ns1"; $finalfilename = $upload_dir.$today."_".$user_handle."_".$friendlyemail.".ns1"; ?> <title>WWWD 3 :: Upload Form</title> <body> <? echo $user_filesize;?> bytes received..<p> <? //5374654e $handle = fopen ($_FILES[‘img1'][‘tmp_name'], "rb"); $contents = fread ($handle, 4); fclose ($handle); if (bin2hex($contents) == "4e657453") { ?> Valid .NS1 file detected..<p> <p> <? copy($_FILES[‘img1'][‘tmp_name'], $finalfilename) or die("Couldn't copy the file!"); $newdate = date ("F dS Y h:i:s A"); if ($user_conf) { ?>Sending email confirmation..<p><? $subject = "WWWD3 submission confirmation"; $ emailbody = "This email confirms that we have received your WWWD3 data:\n\n Name: $user_handle\n Email: $user_email\n File Size: $user_filesize\n Time: $newdate\n\n"; mail($user_email, $subject, $emailbody, "From: roamer@worldwidewardrive.org\r\n"); } else { ?>Email confirmation not selected.. skipping<p><? } $subject = "WWWD3 SUBMIT: $user_handle from $user_addr"; $emailbody = "A new submission has been received:\n\n Name: $user_handle\n Email: $user_email\n Sent confirmation email: $user_conf\n From IP: $user_addr\n File Name: $prettyfilename \n File Size: $user_filesize\n Time: $newdate\n\n"; //Send email to admin mail($admin_email_addy, $subject, $emailbody, "From: roamer@worldwidewardrive.org\r\n"); ?> <b>Thanks for participating in the third WorldWide Wardrive!</b> <? } else { ?> <b>Invalid .NS1 file detected. Please go back and check that the file that you are uploading is a NetStumbler .NS1 file.</b> <p> <? } //var_dump($_POST); //var_dump($_FILES); } else { die("Form is missing information. Please go back and enter a name, valid email address, and file."); } ?> </body> </html> With the upload script generated, I no longer needed to be concerned with getting hundreds of attachment filled e-mails from the individuals and organizers that participated. Now I needed to make sure that there was a standardized way to get the data into NetStumbler .ns1 format. In the past, I had just taken the wi-scan dumps and imported them into NetStumbler, then saved them off to .ns1. Since I now wanted all data in .ns1 format from the start, I needed an easier way for participants to get this done. Luckily, the Church of WiFi (CoWF), had been working on a project to do just this. The project, called WarGlue, was a cross platform suite of WarDriving tools designed to give WarDrivers several different utilities to manipulate their logs.
blackwave, Converge, and ffrf were the primary authors of these tools. I contacted them and let them know what I was planning for WWWD3 and asked when they would have the WarGlue suite ready. They essentially asked me when I would need it. I still had one piece of the puzzle to take care of before I could announce the dates, but I told them I was shooting for March 31st for the WWWD3 announcement and that I hoped to do a joint announcement with them to announce the WWWD3 and release WarGlue to the world. We decided this would work and I began work on the final piece.
Because the security community and the press had unfortunately not understood the goals of the first two WorldWide WarDrives, I wanted to try to explain it to them in a more effective way. I decided the best way to accomplish this would be to hold a presentation at a security conference, and intended to present the information at DefCon 11. Unfortunately, the Call for Papers (CFP) for DefCon 11 had not opened yet. I contacted The Dark Tangent, the primary organizer and founder of DefCon, directly and pitched my idea. I wanted to give a presentation entitled “The WorldWide WarDrive: The Myths, the Misconceptions, the Truth, the Future” at DefCon 11. This presentation would detail all of the goals of the project, the history of the project, the issues and problems I had run into to date. I would also reveal the complete statistical analysis and results of the WWWD3 for the first time. The Dark Tangent was impressed with the idea and agreed to give me a speaker slot at DefCon. I truly appreciated him doing this long before the official CFP went out. With the major pieces of the organization puzzle in place, I could go forward with the announcement on March 31st, 2003.
I chose June 28th through July 5th, 2003 for the dates of the WWWD3. This gave me time to generate the statistics and add them into the presentation before DefCon 11, which took place August 1st through 3rd, 2003. With the dates decided, I got back in touch with the CoWF and asked them to write up their portion of the announcement, to be jointly released on March 31st, 2003.
With our target dates decided, we needed to move forward with getting the programs generated. The CoWF needed to get WarGlue ready for release. The primary component of WarGlue that would be needed for the WorldWide WarDrive was WarKizniz. WarKizniz is a program that would take Kismet data and convert it into NetStumbler .ns1 format. As promised, the CoWF delivered WarGlue on time. The entire suite is available for download at www.michiganwireless.org/tools/. WarKizniz allowed participants to do the data conversion on their end and upload it using the automated upload script.
Before I could release the announcement, I needed to address the issue of organizers. I did not want organizers that didn’t agree with the goals of the project. I also didn’t want companies that would use the guise of the WWWD to attempt to generate business for their company. I created the following statement that I required anyone who wanted to organize an area to read and accept prior to being listed on the organizers page, as shown in Figure 8.2.

Figure 8.2: The WorldWide WarDrive Organizer Agreement
Once the dates were announced, organizers started getting their areas lined up. I realized right away that this was going to be a bigger event than the two previous WorldWide WarDrives. I knew that I had to address the statistical generation issue. It had taken me nearly 12 hours to compile the statistics and generate the maps from the WWWD2. If it turned out this one was bigger, as I expected, I knew that I would not be able to generate the statistics by hand. I had to create the statistical generation program. Because I had the code from the DefCon 10 WarDriving contest, which actually provided a lot of the functionality for parsing the data sets that I would need, I used it as a guide and created the statistical generation program. I wrote the main command-line interface and blackwave updated it to allow for some additional functionality.
#!/usr/bin/perl ###################################### ##9:33 PM 8/30/2003 #CoWFSG - Church of WiFi Stat Generator # cowfsg-cli.pl written and maintained by #roamer@worldwidewardrive.org ## can be downloaded from #http://www.michiganwireless.org/tools//statgen/ ###################################### # 9:34 PM 8/30/2003 # parameters updated: blackwave ###################################### my $ioflag = -1; if ($#ARGV==-1) { die "usage: cowfsg-cli.pl [-file | -screen | -both] input(wiscan) output(ascii)\n"; } elsif ($#ARGV==0) { $ioflag = $#ARGV; } elsif ($#ARGV==1) { $ioflag = $#ARGV; } elsif ($#ARGV==2) { $ioflag = $#ARGV; } else { die "usage: cowfsg-cli.pl [-file | -screen | -both] input(wiscan) output(ascii)\n"; } my $outflag = 3; #default if ($ARGV[0] eq ‘-screen') { $outflag = 0; } elsif ($ARGV[0] eq ‘-file') { $outflag = 1; } elsif ($ARGV[0] eq ‘-both') { $outflag = 2; } if (($outflag != 3) && ($ioflag < 1)) { die "error: check usage: not enough arguments... \n"; } if (($outflag >1) && ($ioflag < 2)) { die "error: check usage: not enough arguments... \n"; } $indexStart=0; if ($ioflag >=1) { $indexStart=1; } # list of default SSIDs, this list differs from netstumbler's local $default_list = "^101\$". "|^WLAN\$". "|^Default SSID\$". "|^Wavelan\$". "|^tsunami\$". "|^WaveLAN Network". "|^Apple Network [0-9a-f]+". "|^Air[Pp]ort Network [0-9a-f]+". "|^default\$". "|^ANY\$". "|^any\$". "|^linksys\$". "|^Wireless\$". "|^2\$". "|^BRIDGE\$". "|^Compaq\$". "|^xlan\$". "|^intel\$". "|^comcomcom\$"; # get the input and output from command line get_data($ARGV[$indexStart]); if (($outflag == 1) || ($outflag == 2)) { write_file($ARGV[$indexStart+1]); } if (($outflag ==0) || ($outflag ==2)) { write_screen(); } #process the input file sub get_data { $infile=$ARGV[$indexStart]; chomp $infile; open (SUMMARY, $infile) || (die "unable to open input file $infile\n"); while (<SUMMARY>) { my @data; local ($lat, $lon, $ssid, $mac, $flag) = 0; local $has_wep = 0; local $has_default_ssid = 0; chomp; my $line = $_; next if /^$/; # skip blank lines next if /^#/; # skip comment lines @data = split(/\t/); next if $#data < 9; # skip short lines # extract lat & lon $lat = $data[0]; $lon = $data[1]; #extract MAC address $data[4] =~ m/([0-9a-f][0-9a-f]:[0-9a-f][0-9a-f]:[0-9a-f][0-9a-f]:[0-9a-f][0-9a-f]:[0-9a-f][0-9a-f]:[0-9a-f][0-9a-f])/; $mac = $1; next unless defined $mac; # skip bad mac lines $mac =~ tr/a-z/A-Z/; # extract SSID $data[2] =~ /\(\s+(.*)\s+\)/; $ssid = $1; $has_default_ssid = 1 if ($ssid =~ /$default_list/); # extract flag for testing for WEP usage. if ( defined $data[8]) { $flag = hex $data[8]; } else { $flag = 0; } $has_wep = 1 if ($flag &0x0010); # convert lat and lon to signed decimal if ($lon =~ /^[EW]/i ) { @data=split(/\s/,$lon); $lon=$data[1]; $lon *= -1 if $data[0] =~ /W/i; @data=split(/\s/,$lat); $lat=$data[1]; $lat *= -1 if $data[0] =~ /S/i; } # skip AP with out a location (lat = 0) next unless ($lat != 0.0); # record each MAC once... unless (defined $known_macs{$mac}) { $known_macs{$mac} = $line ; $allaps{$mac}++; $aps++; $ssids{$ssid}++; $total_wep++ if $has_wep; $total_default_ssid++ if $has_default_ssid; $total_open++ if ( $has_default_ssid == 1 && $has_wep == 0); $total_no_wep=$aps-$total_wep; $total_percent=100; $wep_percent=$total_wep/$aps*100; $no_wep_percent=$total_no_wep/$aps*100; $def_ssid_percent=$total_default_ssid/$aps*100; $open_percent=$total_open/$aps*100; } next; } close(SUMMARY); #process the output file sub write_file { $outfile=$ARGV[$indexStart+1]; chomp $outfile; open (STATS, ">$outfile") || die ("unable to open output file $outfile"); # print the results to the output file print STATS "Total APs found= $aps $total_percent% \n"; print STATS "APs with WEP enabled= $total_wep "; printf STATS ("%.2f",$wep_percent); print STATS "% \n"; print STATS "APs without WEP enabled= $total_no_wep "; printf STATS ("%.2f",$no_wep_percent); print STATS "% \n"; print STATS "APs with a Default SSID= $total_default_ssid "; printf STATS ("%.2f",$def_ssid_percent); print STATS "% \n"; print STATS "APs with a Default SSID and no WEP enabled= $total_open "; printf STATS ("%.2f",$open_percent); print STATS "%\n"; close (STATS); } #process the output sub write_screen { # print the results to the output file print STDOUT "Total APs found= $aps $total_percent% \n"; print STDOUT "APs with WEP enabled= $total_wep "; printf STDOUT ("%.2f",$wep_percent); print STDOUT "% \n"; print STDOUT "APs without WEP enabled= $total_no_wep "; printf STDOUT ("%.2f",$no_wep_percent); print STDOUT "% \n"; print STDOUT "APs with a Default SSID= $total_default_ssid "; printf STDOUT ("%.2f",$def_ssid_percent); print STDOUT "% \n"; print STDOUT "APs with a Default SSID and no WEP enabled= $total_open "; printf STDOUT ("%.2f",$open_percent); print STDOUT "%\n"; } } Additionally we thought it would be good to have a graphical user interface (GUI) for people that wanted to use one. blackwave created the GUI and both programs were released on the Church of WiFi Web site (www.churchofwifi.org/statgen).
#!/usr/bin/perl -w ###################################### ##5:53 PM 8/30/2003 #CoWFSG - Church of WiFi Stat Generator # cowfsg-gui.pl v 1.0 ## filename: cowfsg-gui.pl #created and maintained by #blackwave@hushmail.com ## using perl/Tk #for use with #cowfsg-cli.pl written and maintained by #roamer@worldwidewardrive.org ## both can be downloaded from #http://www.michiganwireless.org/tools//statgen/ ###################################### use Tk; use File::Copy; my $mw = new MainWindow(-title => ‘CoWFSG - Church of WiFi Stat Generator'); $mw->geometry(‘500x400'); my $mb = $mw->Menu(-type => ‘menubar'); $mw->configure(-menu => $mb); my $fm = $mb->cascade(-label => ‘~File', -tearoff => 0); $fm->command(-label => ‘Open ...', -command => sub {&bfd($mw)}); $fm->command(-label => ‘Save As ...', -command => sub {&sad($mw)}); $fm->command(-label => ‘Exit ...', -command => sub {exit}); my $am = $mb->cascade( -label => ‘~About', -tearoff => 0); $am->command(-label => ‘About ...', -command => sub {&ad($mw)}); my $image = $mw->Photo(-file => "CoWF-logo.gif"); $mw->Button(-text => ‘Exit', -command => sub {&bfd($mw)}, -image => $image)->pack; ad(); my $rtd = $mw->Scrolled("Text")->pack(); $rtd->insert(‘end',"Hint: You need to open a file - click Something"); rmtmpf(); MainLoop; sub bfd { my $w = $_[0]; my $types; my $wsf; my $rsout='cowfsg_gui_output_asc'; my @types =(["wi-scan files", [qw/.*/]],); $wsf = $w->getOpenFile(-filetypes => \@types); if ($wsf ne "") { my $rstr = qx(perl cowfsg-cli.pl -file $wsf $rsout); system($rstr); #my $rtd = $mw->Scrolled("Text")->pack(); $rtd->delete("1.0", "end"); open(FH, $rsout) || die "Could not open file $rsout"; while (<FH>) { $rtd->insert(‘end', $_); } close(FH); } } #save as drop down sub sad { my $w = $_[0]; my $types; my $wsvf; my $rsout='cowfsg_gui_output_asc'; my $rsav= ‘cowfsg-default-saved.txt'; my @types =(["wi-scan files", [qw/.*/]],); $wsvf = $w->getSaveFile(-filetypes => \@types, -initialfile => $rsav); copy("$rsout","$wsvf"); rmtmpf(); } # about drop down sub ad { my $atr='CoWFSG - Church of WiFi Stat Generator written and maintained by blackwave@hushmail.com http://www.michiganwireless.org/tools//statgen/'; $mw->Label(-textvariable => \$atr, -relief => 'ridge', -wraplength => 500)->pack(-side => 'bottom', -fill => 'x'); } #clean up if required sub rmtmpf { my $rsout='cowfsg_gui_output_asc'; unlink $rsout; } # NMEA! # End of File. At this point, the work had been done. I set up an e-mail alias (media@worldwidewardrive.org) designed specifically to handle requests from the media. Although I was slightly more accessible to the media, I still didn’t do a lot of interviews. This is because most of the media requests came in between the end of the WWWD3 and DefCon 11. Most of the media requests wanted the results and I had promised that they would be released to the world for the first time at DefCon 11 during my presentation. I kept my promise and not even the primary organizers, blackwave, Converge, ffrf, and Renderman were given access to the results. I did reserve a front row seat for them at my presentation though and made sure to point out all of the hard work that they had put into the WWWD from its inception to the present.
Lessons Learned
Overall, I was very happy with the WWWD3. I was amazed by both the level of participation and the commitment that others have to this project. Agent Green, in addition to coordinating the WWWD3 for the entire state of Massachusetts, contacted me about selling WWWD3 t-shirts. He was willing to foot the bill for the shirts and would sell them from his Web site. I told him to go ahead with it. One thing that some people didn’t seem to understand about the WWWD3 t-shirt was that when you have a small run of shirts like this, it is very cost ineffective. Agent Green sold them for $20, including shipping. People immediately started complaining that we were trying to make money off of sales from the shirts. This was simply not true. Agent Green covered the costs to make the shirts. He received all proceeds from the sales, but also lost quite a bit of money on the shirts. I should have put this information on the Web page when I first announced that the shirts were for sale, but I didn’t. I think this led to some of the confusion about the potential profit from the shirts. Amazingly, even though he lost money, Agent Green still plans to make shirts for the WWWD4 and offer them for sale.
On that same note, Maui, the organizer from Korea, contacted me and asked if I would mind if he had some WorldWide WarDrive coins made. These are the same type of commemorative coins that United States Military units present to unit members to show their appreciation (see Figure 8.3). Once again, Maui wanted to pay for these out of his own pocket and provide them to me for distribution. I told him to go ahead with it. I am not sure what the production of the coins cost, but I am sure they were very expensive and they look great. We agreed that these coins would never be sold and would only be available to those individuals that had contributed to the WorldWide WarDrive in a major way. These individuals would be given a coin to show appreciation for their hard work.
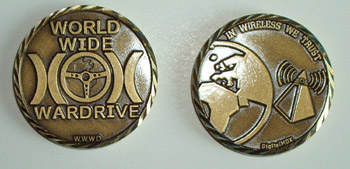
Figure 8.3: The WorldWide WarDrive Coin
Since so much time had passed between the second and third WorldWide WarDrives, I had the opportunity to sit back and see how the event was perceived. More importantly, I had the opportunity to realize how much more effective this event is if the time is taken to organize it properly and plan the event several months in advance. There had been talk of doing the WWWD once every three months. Because of the success of the WWWD3, this idea was completely scrapped. Once a year is the right frequency for the WWWD.
Statistics from the WorldWide WarDrive 3
There is no doubt that the third WorldWide WarDrive was the most successful. Over 300 people participated in 52 areas, representing 11 countries on four continents Additionally, data was submitted from Australia without GPS coordinates and wasn’t included in the statistics. The Most Common SSID and Second Most Common SSID were not calculated this time around. This is because for the third straight time the most common was Linksys and the second most common was Default. This statistic wasn’t providing any real, valuable information. See Table 8.3.
| CATEGORY | TOTAL | PERCENT |
|---|---|---|
| TOTAL APs FOUND | 88122 | 100 |
| WEP Enabled | 28427 | 27.92 |
| No WEP Enabled | 59695 | 72.07 |
| Default SSID | 24525 | 35.27 |
| Default SSID and No WEP | 21822 | 31.44 |
The DefCon 11 WarDriving Contest
The last organized WarDrive that I will discuss is the DefCon 11 WarDriving Contest. The DefCon 10 contest was a complete success. Even with the problems that we encountered, the majority of the contestants said they had a good time and wanted to do it again. The DefCon 11 contest was in many ways more successful than its predecessor, but in many ways more trying. Unlike the previous year, where the entire contest was planned in a few weeks, we began planning early in the year. Some basic brainstorming actually began in late 2002, with the bulk of the planning being done in early 2003. We decided to have the contest planned out and ready to go by April, 2003. This would give us three to four months to deal with any issues that popped up between the contest announcement, and the actual start of DefCon.
The staff for the DefCon 11 contest was very similar to the staff from the previous year. Only one change was made. Rather than have Pete Shipley score the contest, we asked Converge to be the official scorer, and Pete would handle the press inquiries that the contest generated.
Incorporating the Lessons Learned from the DefCon 10 WarDriving Contest
We knew that the prize situation from the previous year was not acceptable. I approached Black Beetle and The Dark Tangent in March and requested that DefCon kick in prizes for the contest. I wanted the DefCon leather jackets that Capture the Flag and Hacker Jeopardy winners get. Because this was only the second year of the contest, they decided that was too big a prize. They did, however, agree to provide the coveted black badge again as well as a limited edition DefCon hooded fleece that was not available for purchase by general contest attendees. We also decided that only the contest winners would receive a prize as opposed to the DefCon 10 contest where the top five teams received prizes. We wanted the winners to be more exclusive than the previous year.
Because of the problems experienced at DefCon 10 with the wireless network, I decided that the data server had to be on the wired network. My thought was that with the data server on the wired network, each contestant could use a wired Ethernet port and upload their data. As you will see later, this didn’t work out exactly as I had planned, but the server was placed on the wired network.
I was embarrassed by our contest sign from DefCon 10. In early May, I contacted Black Beetle and asked if we could get a sign with the contest logo printed up that matched the glossy speaker area signs that DefCon prints up. Black Beetle was great about making sure our sign was prepared. By the time the contest had rolled around, the contest logo (see Figure 8.4) was very familiar to the contestants and the sign was easy for them to spot so they would know where to check in and complete the contest registration forms.

Figure 8.4: The DefCon 11 WarDriving Contest Logo
I loved the way we allowed the rules to be loosely interpreted. This was an element of the contest that I wanted to make sure we kept in place. The rest of the contest staff agreed with me and the only new rule that was added was the “Shmoo Rule” stating that only ground transportation could be used for the contest.
We spent most of our time addressing the sign-up process, and found ourselves completely overwhelmed at DefCon 10 trying to get the teams together. To make things easier, we decided to start the sign-up process at the end of March, 2003 and have an online only sign-up process.
Keeping It New and Different
We knew that it would not be fun to just go out and WarDrive Las Vegas again. In order for the contest to be successful a second year, there had to be a new element to it. To accomplish this, Russ came up with the idea of a tournament-style contest. This time, the contest would encompass two WarDriving days instead of just one. There would be a total of 12 teams, with a maximum of five contestants allowed to participate in each. Based on the results of the first day of WarDriving, only the top six teams would be allowed to advance to the final round and compete for the championship.
We also contacted some selected sponsors and asked them to contribute money to the event. Since the prizes were only going to the overall winning team, we wanted all of the contestants to have a souvenir from the contest. For the first time, we asked the contestants to pay a five-dollar entry fee. We supplemented this entry fee with the money from the sponsors and gave every participant three things that only WarDriving contestants could get. The first was a bumper sticker with the contest logo on it. They also received a dog tag with the contest logo on one side and the DefCon logo on the other, along with a dog tag silencer. They also got a long-sleeve t-shirt with the contest logo on the front, the DefCon logo on the back, and the “WarDriving is not a crime” logo down one sleeve. The contestants were more than happy to pay the five-dollar entry fee and the contest items were a big hit.
Running the Contest
Once we started allowing people to sign up for the contest, the slots on all 12 teams quickly began to fill up. In order to complete their registration for the contest, they needed to do two things. First, I would e-mail them the liability disclaimer (this was the same disclaimer that we had them physically sign the year before; see Figure 8.1). They were required to reply to that stating that they accepted the terms of the disclaimer. Then, once on site, each contestant was required to check in with the contest staff and pay their five-dollar entry fee. At that time, we would give them their shirt, dog tag (see Figure 8.5), and bumper sticker. The 12 teams were full by the end of May, and we opened up a standby list. This was a list of people that would fill slots that were not claimed by someone who had signed up online.

Figure 8.5: The DefCon 11 WarDriving Contest Dog Tag
The contest was two days of driving. The first day, Friday, was a two-hour drive. When contestants checked in with the contest staff, we gave them their username/password combination so that they could upload their data when they were finished driving. We also notified them of the geographical boundaries for the first stage of the contest. This was different from the previous year when we used anonymous FTP for the data upload. For the first day, all 12 teams would participate. Only access points found on Paradise Road in Las Vegas and east of Paradise would be counted. The top six teams would qualify for round two, a three-hour drive on Saturday that would take place on Paradise Road and west.
The first day’s drive went smoothly, but once again we ran into problems with the data uploads. Although the data server was on the wired network as promised, DefCon did not offer any wired connections for attendees at DefCon 11. All network access was wireless. Because of this, we ran into many of the same problems from the year before. Contestants had a hard time getting a connection because of the number of rogue access points that were in range posing as DefCon access points. At one point, I ran NetStumbler and there were over a hundred rogue access points in range of the Alexis Park Hotel. We quickly got the word out to contestants that they could provide us their data on floppy, CD-ROM, or USB disk drive. About half of the contestants were able to successfully log in and upload their data. The others were forced to physically give us their data.
On the morning of the first drive, we discovered a bug in the conversion program that contestants needed to convert their kismet data to wi-scan with extensions. The bug was essentially that if an access point had an SSID that started with parentheses, the conversion script would crash. Since we were unable to get the updated script to the contestants quickly enough, we allowed them to upload their unconverted data from the drive so that Converge could do the conversion with the patched script. We repeated this for day two just so things would be consistent for the contestants.
After the first drive, members of The Lords of Wireless team contacted me and asked what exactly I meant by “Paradise Road and west.” I told them that it meant exactly that. Anything west of Paradise Road would be counted. They explained that they wanted to send one of their team members to Los Angeles, California and have him start his drive there. I told them that if they provided me with proof such as gas receipts, restaurant receipts, and so forth that showed he had left Las Vegas on Saturday morning and drove during the allotted three hours only, I would accept their data. They agreed and sent one of their team members to Los Angeles the next morning. This was an excellent strategy because all of the access points he found in Los Angeles would have been “unique.” This means that each of the access points found there would have been worth a minimum of six points; one for an access point and five more because it was unique. He did provide me with the proof that I had asked for, unfortunately, he didn’t get the data to us in a readable format, and so those results didn’t get counted.
In the end, it didn’t matter since The Lords of Wireless won the contest even without the Los Angeles data. They barely edged out last year’s champion, Team WirelessCon, as shown in Table 8.4.
| Place | Team | AP | WEP | SSID | Unique | Total |
|---|---|---|---|---|---|---|
| 1 | Lords of Wireless | 2219 | 612 | 748 | 1264 | 7883 |
| 2 | Team WirelessCon | 1983 | 625 | 604 | 737 | 6048 |
The complete results of the DefCon 11 WarDriving Contest are available at www.defcon.org/html/defcon-11/defcon-11-postcon.html.
Lessons Learned
Despite our best efforts, the DefCon 11 WarDriving Contest still had some problems that need to be addressed for future contests. First, this was the last year that a simple WarDrive of Las Vegas could be done. Even though there are more wireless networks being deployed every day, driving the same city over and over again is not going to be enjoyable for the contestants. This has to be addressed for the DefCon 12 WarDriving Contest.
The loose interpretation of the rules has been successful in that it is always fun to see the ideas people will come up with to meet the letter of the law while violating the spirit. Even though the Lords of Wireless data from Los Angeles was not counted because of formatting problems, a lot of the contestants did not feel that it was fair to allow this data. These contestants were very vocal about this and it put a damper on the contest for some of the organizers. In addition to the “Shmoo Rule” from DefCon 10, future contests will have the “WiGLE Rule.” The WiGLE rule states that only data from the state of Nevada will be counted. It is named the WiGLE Rule because the Lords of Wireless team was comprised of several members of the WiGLE mapping Web site (www.wigle.net).
The data dump continued to be an issue. Once again, many contestants had a hard time connecting to the data server. The DefCon WarDriving contest staff has come up with a plan to address this issue. For future contests, an area will be set aside for the data dump to take place. Each contestant will need to connect to a switch that we will provide via a wired connection. In addition, each contestant will be required to upload their data to this server. The data server will also be connected directly to this switch, thus bypassing the DefCon network completely.
Finally, the data format issue was once again a problem. The bug that was discovered in the WarGlue software the morning of the contest threw the data dump into disarray. This is the second year in a row that the wi-scan with extensions format has caused problems for Kismet users. Future contests will not rely on this format. Contestants will be required to submit their data in NetStumbler .ns1 format. They will be able to use the WarKizniz conversion script to convert any Kismet logs to NetStumbler .ns1 format. Requiring contestants to use this format opens up several options to the scoring staff. NetStumbler makes it easy to convert the data to a flat text dump, wi-scan format, or wi-scan with extensions. Using the NetStumbler format was also very successful for the WorldWide WarDrive 3, so now this format has a proven track record of success.
|
| < Day Day Up > |
|
EAN: 2147483647
Pages: 125
- Chapter VIII Personalization Systems and Their Deployment as Web Site Interface Design Decisions
- Chapter X Converting Browsers to Buyers: Key Considerations in Designing Business-to-Consumer Web Sites
- Chapter XIII Shopping Agent Web Sites: A Comparative Shopping Environment
- Chapter XVI Turning Web Surfers into Loyal Customers: Cognitive Lock-In Through Interface Design and Web Site Usability
- Chapter XVII Internet Markets and E-Loyalty