Managing and Monitoring Remote Access
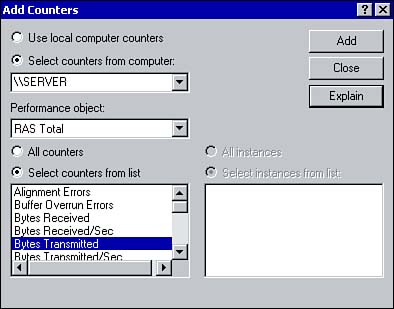
| As with all servers performing a specific role on a network, you should perform management and monitoring tasks to ensure the server is functioning as it should. The following section covers the function of an Internet Authentication Service (IAS) server and how it can simplify the administration of multiple RAS servers, as well as how to monitor a RAS server for performance. Managing Remote AccessSeveral management tasks have already been covered in this chapter, such as managing remote access through policies and managing IP address assignment using a DHCP server and the DHCP Relay Agent. However, one topic that has been mentioned but not discussed, which you may come across on the exam, is that of an IAS RADIUS server . As your networks increase in size, you may need to implement multiple remote access servers. To ease the administrative overhead of managing multiple RAS servers, you can implement Remote Authentication Dial-in User Service (RADIUS) to centralize the authentication of remote access clients and the storage of accounting information. Windows 2000 can be configured for RADIUS by installing the Internet Authentication Service (IAS) through the Add/Remove programs applet in the Control Panel. When configured for RADIUS, a remote access server will forward authentication requests from RAS clients to the IAS server. IAS provides the benefit of centralizing user authentication and centralizing the storage of auditing and accounting information collected from the RAS Servers. When RADIUS is implemented, the remote access server is configured as a RADIUS client. You can configure a RADIUS client when enabling routing and remote access. Any authentication requests to the remote access server by dial-up users is sent to the server running IAS. The server running IAS will provide authentication, auditing, and accounting services for RADIUS clients. Monitoring PerformanceThe performance of a remote access server can be monitored using System Monitor (found in the Performance console). Several counters are available for monitoring RAS (see Figure 4.13). Table 4.5 summarizes some of the available counters. Two performance objects are available for monitoring RAS: RAS Total and RAS Ports . Use RAS Total to monitor the RAS server and RAS Ports to monitor the status of individual ports. Figure 4.13. Remote access performance counters. Table 4.5. Performance Counters for Monitoring Remote Access
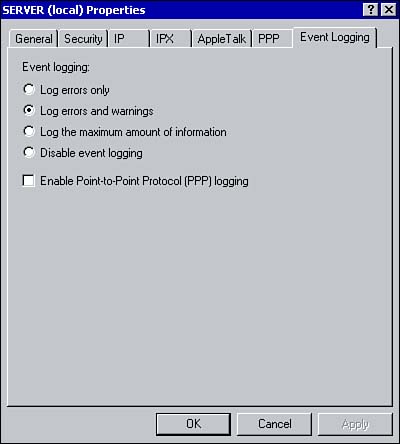
Another way in which you can monitor a RAS server is through logging. Using the Event Logging tab in the server's Properties dialog box, you can have information pertaining to Remote Access Service written to the System log. The logging of errors and warnings is enabled by default, as shown in Figure 4.14. From here you can disable logging, log errors only, or log detailed information. You can also enable PPP logging. Figure 4.14. Enabling remote access logging. |
EAN: 2147483647
Pages: 167