Implementing Secure Access Between Private Networks
Implementing Secure Access Between Private NetworksAs networks throughout the world become more interconnected , network administrators are challenged with ensuring that data transferred across a network is secure. This is where the IP Security (IPSec) protocol comes into play and allows for authentication of hosts , data integrity, and data encryption. IPSec is used to protect data that is sent between hosts on a network, which can be remote access, VPN, LAN, or WAN. IPSec ensures that data cannot be viewed or modified by unauthorized users while being sent to its destination. Before data is sent between two hosts, the source computer encrypts the information. It is decrypted at the destination computer. IPSec provides the following benefits:
As you will see when you begin to configure IPSec, different levels of security can be implemented to meet varying needs. IPSec is implemented through IPSec policies. The policies are created and assigned to individual computers or groups of computers (or groups of users). The policies determine the level of security that will be used. IPSec consists of three components that work together to provide secure communications between hosts:
The following steps outline how the different components work together to provide secure communications:
In summary, before any data is transferred between two hosts, the security level must be negotiated. This negotiation includes agreeing on an authentication method, a hashing method, and an encryption method. Configuring IPSecYou can enable IPSec using the Local Security Policy snap-in. The following list describes the three default policies. You can enable any policy for the local computer by right-clicking the policy and choosing the Assign option.
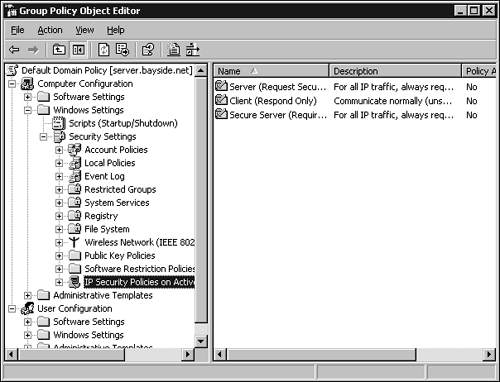
If you are running Active Directory, you can create an IPSec policy that is stored within Active Directory. To view the policies, open the Group Policy snap-in, shown in Figure 5.23. Figure 5.23. IPSec policies within the Group Policy snap-in. The three policies that exist by default are Client, Server Secure, and Server. (The process of creating new IPSec policies is outlined in the following section.) To assign an IPSec policy to Group Policy, right-click the policy and click the Assign option. Configuring IPSec for Transport ModeIPSec can be used in one of two modes: transport mode or tunnel mode . Tunnel mode is used for server-to-server or server-to-gateway configurations. The tunnel is the path a packet takes from the source computer to the destination computer. This way, any IP packets sent between the two hosts or between the two subnets, depending on the configuration, are secured. Two formats can be used with tunneling mode: ESP tunnel mode and AH tunnel mode. With Authentication Header (AH) tunnel mode, the data itself is not encrypted. It provides authentication and integrity, and it protects the data from modification, but it is still readable. With Encapsulating Security Payload (ESP) tunnel mode, authentication, integrity, and data encryption are provided.
To create a new IPSec policy, perform the following steps:
To configure an IPSec tunnel, perform the following steps:
Customizing IPSec Policies and RulesEach of the policies can be edited using the policy's Properties window. IPSec policies consist of several components, including the following:
From the General tab of an IPSec policy's Properties window, you can change the name and description for the policy and configure the interval at which the computer will check for policy updates. Using the Advanced button, you can configure the Key Exchange Settings.
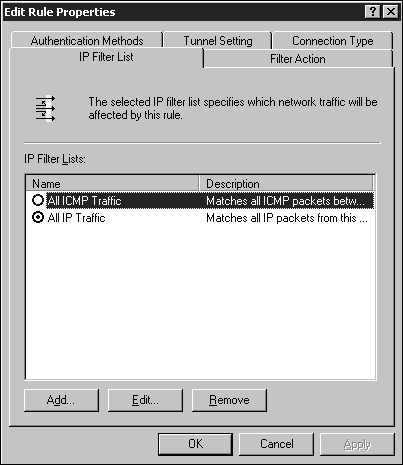
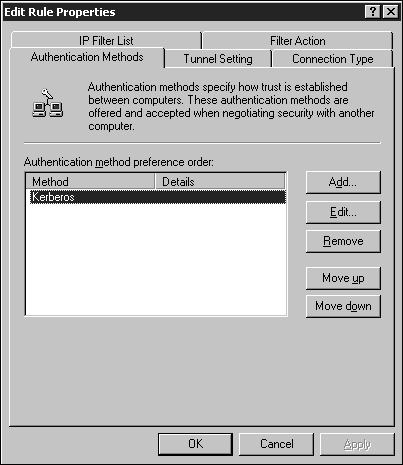
The Rules tab lists all of the rules that are configured for the policy. Other rules can be added by clicking the Add button; you can edit the existing rules using the Edit button. Clicking the Edit button brings up the Edit Rule Properties window (see Figure 5.24). Figure 5.24. Editing IPSec rules. The IP Filter List tab defines the type of traffic to which the rule will apply. The Filter Action tab defines whether the rule negotiates for secure traffic and how the traffic will be secured. Configuring the filter actions enables you to define the different security methods that can be negotiated. The security algorithms supported by IPSec include MD5 and SHA1. The encryption algorithms supported include DES and 3DES. The Authentication Methods tab enables you to configure the method used to establish trust between the two computers (see Figure 5.25). If multiple authentication methods are configured for a rule, you can change the order in which they are used. The authentication methods available include these:
Figure 5.25. Configuring IPSec authentication methods. The Connection Type tab enables you to define the types of connections to which the rule applies. This enables you to define different rules for different types of connections. Rules can be applied to local area connections, remote access connections, or all network connections. The Tunnel Setting tab enables you to specify a tunnel endpoint where communication will take place between two specific computers. You can edit the existing policies, or you can create and assign a new policy through the Group Policy snap-in. To create a new policy, right-click IP Security Policies on Active Directory within a Group Policy Object and select Create IP Security Policy. A wizard walks you through the process of creating the initial policy, which you can configure further using the Properties window for the new policy.
|
EAN: 2147483647
Pages: 118