Problems and Solutions
Now that you have an understanding of how to read Windows 2000 Security Event Logs and IIS logs, we'll turn to the main content of this chapter: common security issues, where to look to verify an issue, and how to resolve an issue. This section uses the work performed in Chapter 10, "Building a Secure Solution," as the example. Each problem looks at two categories of information: symptoms/evidence and causes/resolution.
Permission denied: 'CreateObject' When Launching a COM+ Component
In this scenario, the browser returns an error such as this:
Microsoft VBScript Runtime (0x800A0046) Permission denied: 'CreateObject' |
Figure 11-3 shows the entry that will appear in the event log on the server that attempted to instantiate the COM+ application.

Figure 11-3. The Windows 2000 system log entry showing a failed DCOM event.
The following error, somewhat similar to the error returned in the browser, will appear in the IIS logs:
2000-05-12 05:05:26 172.100.100.13 EXAIR\Squirt 172.100.100.12 80 GET /exairhr/Default.asp |15|800a0046|Permission_denied: _'CreateObject' 500 0 Mozilla/4.0+(compatible;+MSIE+5.01; +Windows+NT+5.0) |
Causes and resolution
The problem occurs when you have no roles defined on the COM+ application or when you have defined roles but the caller is not a member of one of the roles. The simple remedy is to assign roles to your application and add the calling user to one of those roles that can launch the application.
Permission denied: but COM+ Application Ball Spins
On the surface, this seems like a very weird error. There's no SQL Server activity, but we can tell the COM+ application is activated because the ball in the Component Services tool is spinning. Furthermore, no COM+ or DCOM errors appear in the audit logs. The only evidence you'll see if you're auditing for failed object access and you place an audit access control entry (ACE) on the COM+ object in question (DBQuery.dll in our example) is shown in Figure 11-4.

Figure 11-4. A Windows 2000 Security Log Entry showing a failed object access.
Causes and resolution
The DLL's access control list (ACL) is too restrictive and access was denied while COM+ attempted to load the DLL into the COM+ application. The COM+ ball is spinning because the COM+ application has started, but it hasn't loaded the DLL. The remedy is to loosen the ACL on the offending file so that the account can load the file. In this case, the account will be AppAccount because the COM+ application starts as this identity.
Login Failed for user '(NULL)'. Reason: Not associated with a trusted SQL Server connection
This error message will sometimes appear in the browser and in the SQL Server 7 log files, but the Web server and the COM+ application will be running correctly and reporting no error.
Causes and resolution
Something is causing SQL Server 7 to be unable to set up an authenticated connection with the client. This often occurs with sockets—a flaw in the SQL Server 7 socket network library prevents Kerberos mutual authentication from working correctly. You'll most likely see an error like this in the Windows 2000 Security Event Log, as shown in Figure 11-5, if you're auditing for failed Account Logon entries.

Figure 11-5. A Windows 2000 Security Event Log entry showing that the SQL Server 7 socket network library is failing Kerberos authentication.
You can rectify this problem in SQL Server 7 by disabling the socket network library and using the Named Pipes network library instead. Microsoft is aware of the problem and is working to rectify it. Note that SQL Server 2000 client network libraries do not suffer from this problem.
You can set network libraries in SQL Server by using the Server Network Utility included with SQL Server. You can perform a similar function at the COM+ component server (or any server performing data access with SQL Server) by using the Client Network Utility. Also, make sure you are not overriding the network provider in the Active Server Pages (ASP) page or COM+ component. For example, remove network=dbmssocn if you see it in the database connection string, because it overrides the database connection to use sockets.
Error: [DBNMPNTW] Access Denied. 80004005 Microsoft OLE-DB Provider for SQL Server.
This error appears in the browser; the error is a little insidious because no errors are written to any logs.
Causes and resolution
The most common security cause for the error is the IIS process handling the client request not being marked as running out of process or, if it is, not being marked as requesting delegation. Check that the Web application is running with High Protection (Isolated) mode and that the COM+ application handling the out-of-process IIS application is not starting up as IWAM_machinename but as AppAccount. Finally, check that the COM+ application is marked to use delegation rather than impersonation. Normally, the name of the application looks something like IIS-{Default Web Site//Root/ExAirHR}.
Error: Login failed for user 'EXAIR\Alice'. 80040E4D Microsoft OLE DB Provider for SQL Server
You see this error in the browser, but everything appears to be fine in IIS—there are no IIS errors and the COM+ application ball is spinning, showing that COM+ services have started to process the user's request.
The SQL Server logs will contain the following line:
2000-05-03 00:09:08.58 logon Login failed for user 'EXAIR\Alice'. |
Windows 2000 will show a similar error coming from SQL Server in the application log. Windows 2000 will also show that the user has successfully logged on to the computer, as shown in Figure 11-6, but a SQL Server trace will show the request failing, as shown in Figure 11-7.

Figure 11-6. A Windows 2000 Security Event Log entry showing the user successfully authenticated.
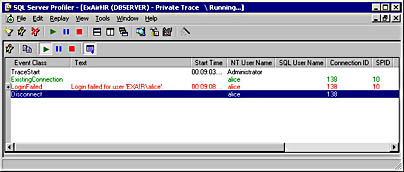
Figure 11-7. SQL Server trace showing EXAIR/Alice failing to access SQL Server.
Causes and resolution
This is common: you forgot to add the user as a valid logon to SQL Server, or you denied the user logon to the database server. The remedy is either to add the account as a SQL Server login or, if it exists, to allow the user to access the database server.
Error: Login failed for user 'EXAIR\AppAccount'. 80040E4D Microsoft OLE DB Provider for SQL Server
This is a slight twist on the previous error, but instead of the user account calling the Web application (for example, Alice), the error says that the COM+ process identity cannot access SQL Server.
Causes and resolution
We can almost guarantee that you'll come across this error at some stage. The error occurs when you forget to impersonate the client in the COM+ application. Call CoImpersonateClient before the database requests, and call CoRevertToSelf after the request is made.
Error: EXECUTE permission denied on object 'spGetCurrentUser', database 'ExAirHR', owner 'dbo'. 80040E09 Microsoft OLE DB Provider for SQL Server
You'll see this kind of error on many objects in SQL Server, especially tables and stored procedures.
Causes and resolution
In this case, a user does not have execute privilege to the spGetCurrentUser stored procedure. The remedy is simple: make sure the appropriate users have the appropriate privileges on the requested objects, such as stored procedures and tables. Figure 11-8 shows the Permissions dialog box on the spGetCurrentUser stored procedure. Permissions are a property of the object in question.
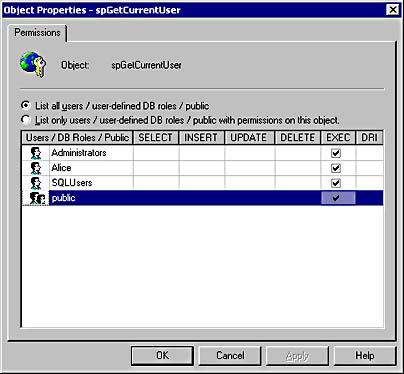
Figure 11-8. The Permissions dialog box on the spGetCurrentUser stored procedure.
Empty Client Certificate Dialog Box in Internet Explorer
You access a Web server that requires a client authentication certificate. However, when the dialog box is displayed to prompt you to choose a client authentication certificate, the dialog box is empty.
Causes and resolution
This is a common problem caused by one of two things: you have no client authentication certificates, or you have no client certificates trusted by the Web server. The second scenario is common if you've issued your clients' certificates by using Microsoft Certificate Services but IIS does not trust the root certificate of your certificate authority (CA).
Rectify this situation by opening the Certificate MMC snap-in and managing the Computer Account. You'll need to add the root CA certificate if it is not listed under the Trusted Root Certificate Authorities node. Also note that you can define a certificate trust list (CTL) in IIS that restricts the root CA certificates trusted by the Web server, so you'll need to check there too.
Using WFetchYou can use WFetch, included on the companion CD, to help solve the Empty Client Certificate Dialog Box problem. WFetch allows you to choose from a list of client authentication certificates: one has expired, one is valid and trusted, one has no revocation information, one is revoked, and the last has expired. By looking at the results sent back by the server, you can better determine the cause of the problem.
NOTE
A new feature in Microsoft Internet Explorer 5.5 does away with the empty dialog box problem altogether. If the new security zone option called Don't Prompt For Client Certificate Selection When No Certificates Or Only One Certificate Exists is enabled, the dialog box will not appear if no client authentication certificate exists; you'll see a Web server error instead. If one client certificate exists, that will be used automatically.
Username Reported by SQL Server Is Different from Username Returned by IIS
You've configured your Web server to use Basic authentication and user principal names (UPNs)—that is, you've set the default domain to '\'—such as major@explorationair.com rather than SAM-compatible names such as EXAIR\Major. However, when you delegate the client identity to SQL Server, SQL Server says the user account is a SAM-compatible name.
Causes and resolution
SQL Server always returns SAM-compatible names from SQL stored procedures such as SUSER_SNAME. However, you can translate a user or computer name to another name format by using a new function in Windows 2000 called TranslateName. We've included a sample application and its C++ source code, called TranslateName, on the companion CD—the application performs similar Active Directory lookups from the command line.
Prompted to Enter Credentials When Using DNS Name as Web Server Name
You access an IIS server that requires Windows Integrated authentication, and you are prompted to enter your credentials. However, if you access the same site by using its NetBIOS name, you are not prompted to enter them.
The IIS logs should show a 401 HTTP status code (unauthorized), and if you're logging the Win32 error code you'll see a 5 error (access denied). If you hit the escape key when the credentials dialog box appears, you'll see a 401.2 error in the browser.
Causes and resolution
Internet Explorer is behaving correctly. When you access a Web site by using a DNS name, Internet Explorer assumes the site is on the Internet. Because of this, the browser will not use your Windows credentials when the Web server sends a 401 status back to the browser; instead, it will prompt you to enter your credentials.
You can get around this by adding the Web server's DNS name to the list of intranet sites known to Internet Explorer:
- Open Internet Explorer.
- Select Internet Options from the Tools menu.
- Click the Security tab, and then click the Local Intranet option.
- Click Sites, and then click Advanced.
- Enter the DNS names of the Web sites on your intranet. Note that you can enter wildcards, as shown in Figure 11-9.

Figure 11-9. Configuring Internet Explorer 5 to allow DNS names on an intranet.
Security Alert While Using SSL/TLS
You access a Web site that requires SSL/TLS, but you see the Internet Explorer alert dialog box shown in Figure 11-10.

Figure 11-10. Internet Explorer 5 warning the user about an SSL/TLS certificate problem.
Causes and resolution
This error occurs in three situations: the name of the Web site you entered is the not the same as the name in the server certificate, the certificate has expired, or you don't trust the issuer of the server's certificate. The second and third scenarios are reasonably straightforward to resolve. The first issue, the name mismatch, is a little more complex because a computer can have many names. For example, it can have a DNS name (www.explorationair.com), a NetBIOS name (\\WebServer), and an IP address (172.100.100.13). Because of this, it's important that you choose the name that goes in the certificate to reflect the most common name used by your clients.
IMPORTANT
The current version of Pocket Internet Explorer does not support server certificates signed using SHA-1. By default, server certificates created by Microsoft Certificate Services use SHA-1. You should use MD5-based signatures instead (determined at Certificate Services installation time) if you use Pocket PC and SSL/TLS connections.
401.2 - Unauthorized Error When You Know You Have Access to the Resource
This is not a very common scenario: IIS is configured to use Windows Integrated authentication and you are a valid user—you must be, you just logged on to your workstation—but when using Internet Explorer you keep getting this error rather than being prompted to enter your credentials.
Causes and resolution
You probably have Internet Explorer configured to always use anonymous connections in the intranet zone. You can verify this by performing these steps:
- Open Internet Explorer.
- Choose Internet Options from the Tools menu.
- Click the Security tab, and then click the Local Intranet option.
- Click Custom Level, and scroll to the bottom of the Settings list box. If the dialog box looks like that shown in Figure 11-11, any form of authentication will fail. Click the Automatic Logon Only In Intranet Zone option button.

Figure 11-11. Internet Explorer 5 will use not authentication schemes as long as the Anonymous Logon option is checked.
401.3 - Unauthorized Error or Administrator Asked to Enter Username/Password
You're logged on to your desktop as an administrator, but each time you attempt to access a resource that has an ACL allowing administrators full control, you are prompted to enter your username, domain, and password or you get a 401.3 Access Denied By ACL On Resource error.
The main sources of forensics are the Windows 2000 logs and the IIS logs. If you're auditing for failed object access and place an audit ACE on the file in question, you'll see the entry shown in Figure 11-12. Note how the IUSR_machinename account is accessing the resource rather than the administrator.

Figure 11-12. A Windows 2000 Security Event Log entry showing a failed object access.
Now look at the following IIS log entry. Note first the lack of a user account—the "-" before the IP address indicates no user (in other words, an anonymous user). And note the two errors: 401 (HTTP not authorized) and 5 (Win32 access denied error).
2000-05-12 06:13:35 172.100.100.40 - 172.100.100.12 80 GET /ExAirHR/ - 401 5 Mozilla/4.0+(compatible;+MSIE+5.01; +Windows+NT+5.0) |
Causes and resolution
This is very common; you have anonymous access enabled in IIS and no other authentication scheme. Because of this, the administrator account is essentially lost. IIS uses the IUSR_machinename account instead, and this account does not have access to the resource. Rectify the problem by choosing another authentication scheme in IIS or changing the file ACL.
401.4 - Authorization Denied by Filter While Using Digest Authentication
A user attempts to log on to an IIS server configured to require Digest authentication using Internet Explorer 5. However, the user is prompted to enter credentials, and the user receives a 401.4 error. The Windows 2000 Security Event Log will show a logon failure (that is, Logon/Logoff event 529) for the account attempting to log on.
Causes and resolution
The user does not have a plaintext password set in Active Directory. Get the user to change the password while the option is set.
403.13 - Client Certificate Revoked When You Know the Client Certificate Is Not Revoked
You access a Web page that requires a client authentication certificate. However, you're told that the client authentication certificate is revoked, and you're certain the certificate has not been revoked.
Causes and resolution
There are two causes for this: either your client authentication certificate has indeed been revoked (regardless of what you think) or your certificate has a certificate revocation list distribution point (CDP) that IIS cannot reach. If IIS cannot reach the CDP, it assumes someone has attacked the CDP and issues the error.
Look at the client certificate—you can view the certificate by using the Internet Options option on the Tools menu, clicking the Content tab, and clicking the Certificates button—and see what the CDP is. From the Web server, ping the location of the CDP and see whether you can retrieve the certificate revocation list.
Figure 11-13 shows a CDP in a certificate issued by Microsoft Certificate Services. Note that two CDP access protocols are listed: LDAP (Lightweight Directory Access Protocol) and HTTP. If both of these fail to resolve, IIS will reject the client request.
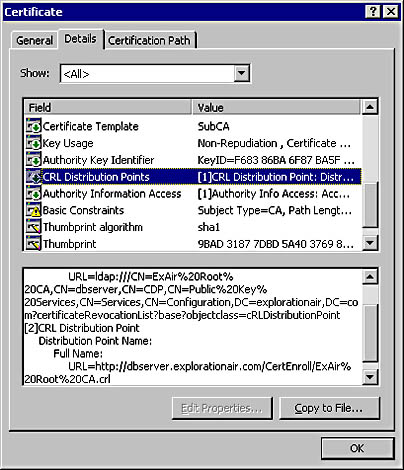
Figure 11-13. A certificate and its CDP.
NOTE
You can add different CDPs to certificates issued by Microsoft Certificates Services. Access this functionality by following these steps: open the Certification Authority snap-in, right-click the CA, select Properties from the context menu, click Policy Module, click Configure, and click X.509 Extensions.
403.15 - Forbidden: Client Access Licenses Exceeded
When connecting to IIS, you receive this error message. You also see the following in the Windows 2000 application log:
Event ID: 27 Source W3SVC Description: The server was unable to acquire a license for a SSL connection. |
Causes and resolution
Either the number of authenticated users connected to the Web server has exceeded the number of client access licenses (CALs) or the number of SSL/TLS connections has exceeded the number of CALs. Another possibility: if the License Logging Service is stopped, only 10 concurrent authenticated or SSL/TLS connections will be permitted.
You can rectify this situation by purchasing more CALs.
EAN: N/A
Pages: 138