Debugging Tips
COM+ 1.0 logs access failures in two places: the system log and the application log. Activation failures are logged in the system log. When the failure is related to security reasons, the description reports some of the user details. Note that the event source is reported as DCOM, even though the component being activated is hosted in a COM+ 1.0 application, because it's the DCOM activation services that activate COM+ 1.0 components. Figure 7-17 shows an example.
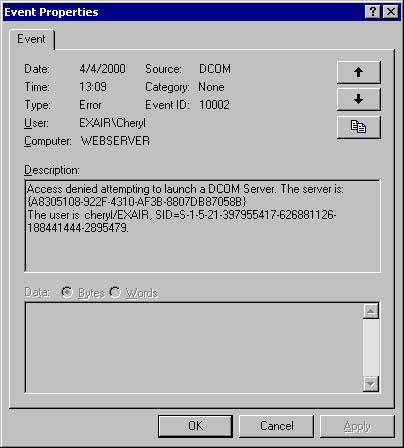
Figure 7-17. An activation failure event.
For failures on calls, COM+ 1.0 reports events in the application log. In this case, the event source is noted as COM+. The event description for the failed call includes the details described in Table 7-2.
Figure 7-18 shows an example of a call failure event recorded in the Windows 2000 event log.
Table 7-2. Call failure event details.
| Field name | Comments | ||||||||
|---|---|---|---|---|---|---|---|---|---|
| Application Id | The GUID (globally unique identifier) for the COM+ application hosting the targeted component. | ||||||||
| CLSID | The CLSID (class identifier) of the targeted component. | ||||||||
| IID | The IID (interface identifier) of the targeted interface. | ||||||||
| Method # | The method number (vtable slot) of the targeted method. | ||||||||
| Caller Information | Security information about the call. | ||||||||
| Svc | The authentication service used for the call. This is an integer identifying one of the following services:
| ||||||||
| Lvl | The authentication and protection level, as described in Table 7.1, which ranges from 0 (None) to 6 (Packet Privacy). | ||||||||
| Imp | The impersonation level: 1 (Identify), 2 (Impersonate), or 3 (Delegate). |
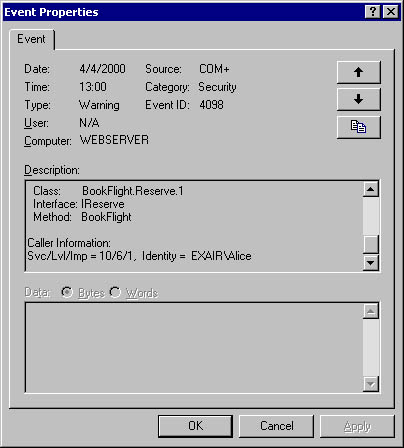
Figure 7-18. A call failure event in the Windows 2000 event log.
EAN: N/A
Pages: 138