Security Zones
Security zones, introduced in Internet Explorer 4, are an easy way to administer security because they allow you to gather security settings into easy-to-manage groups. The security settings are enforced when you browse Web sites. The main tenet behind security zones is that some Web pages need to be handled with specific security restrictions depending on their host Web site, thereby matching security restrictions with Web page origin. In essence, zones are a form of security policy that is enforced when you browse certain classes of Web sites.
Another goal of zones is to reduce the number of times a user is prompted to make a security decision. If a user is asked to make numerous yes-no decisions, often the user will end up repeatedly hitting Yes out of frustration without really reflecting on the question being asked.
The security settings that can be assigned to the various zones are as follows:
- Low Only the most trusted sites should run at this level because it performs the fewest security checks and rarely warns the user by providing a prompt.
- Medium-Low This level is more secure than Low—unsigned active content is not downloaded—but it includes few prompts.
- Medium This level is more secure than Medium-Low, and it includes more prompts, including prompts before potentially unsafe content is downloaded.
- High This is the most secure but least functional (from the perspective of the person browsing the Web) level. Cookies are disabled, and many prompts are provided for the user.
- Custom This level allows complete control over every security aspect, including ActiveX controls, cookies, file downloading, Java support, scripting language support, and authentication.
The zones and their default security settings included in Internet Explorer 5 are described in Table 4-1. For most users, the default security settings should be safe enough without sacrificing functionality.
Table 4-1. Internet Explorer zones and their default security level settings.
| Zone | Comments |
|---|---|
| Local Intranet | Any computer on a corporate intranet is in the Local Intranet zone. A corporate intranet computer is defined as any site that does not require access via a proxy site or that has no period in its URL (for example, http://merlin) or in its Universal Naming Convention (UNC) pathname (\\merlin\data). The default security level for Local Intranet is Medium-Low. |
| Trusted Sites | This zone includes sites explicitly trusted by the user in other words, sites you believe to be benign and contain no content capable of damaging your system or invading your privacy. For example, if you trust your own corporate Web site, you might add it to the Trusted Sites zone. For extra safety, you can also require that all Web sites in this zone have an SSL/TLS connection. By default, no Web sites are included in this zone and the security level is Low. |
| Restricted Sites | This zone is the opposite of Trusted Sites. You should add sites you don t trust but might need access to and sites that could possibly damage your computer to this zone. By default, the zone has no sites and its security level is High. |
| My Computer | As the name implies, this zone s only member is your computer. You cannot configure this zone in Internet Explorer, but you can do so with the Internet Explorer Administration Kit (IEAK). Refer to the next section for information on the IEAK. |
| Internet | This zone includes all sites that are not on your intranet and not listed in any other zone, and it does not include your local computer. The default security level for this zone is Medium. |
The Internet Explorer Administration Kit
The IEAK is an administration tool for Internet Explorer that allows administrators to determine how Internet Explorer is configured. Some of the security features that can be enabled with the IEAK include the following:
- Administrator specification of what ActiveX controls are allowed to run on user's machines
- Choosing which software publishers to trust
- Automatic digital signing (using Authenticode) of controls
- Presetting and lockdown of the following security settings:
- Security zone settings
- Policy lockout—prevents users from changing a particular policy for a particular zone
- Domain lockout—prevents user from changing domain mapping (or site) to another zone
- Prepopulating and enforcing trusted certification authorities
- Locking down proxy settings
- Using content ratings through the Platform for Internet Content Selection (PICS)
You can find out more about the IEAK at http://www.microsoft.com/ie/ieak.
Zones and the Dotless-IP Address DilemmaIf your knowledge of TCP/IP addressing is excellent, you might be aware that an IP address can appear either as dotted notation, such as 158.23.111.15, or as a number with no dots. For example, the IP address 158.23.111.15 would be represented by the number 2652335887. Because no period appears in the address in this form, you might think that Internet Explorer would consider the site an intranet site.
If this were the case, it would create an interesting security vulnerability: a Web site could trick your browser into visiting a part of the site with malicious content by using an address format (such as http://2652335887) associated with intranets. Then the browser would run the content with fewer security measures. However, this is not the case in Internet Explorer 5. When browsing to a Web site with an address composed completely of numbers, the browser considers the Web site to be in the Internet security zone, even if the site is an intranet site.
You can calculate a dotless-IP address by taking a dotted-IP address—that is, an address in the form a.b.c.d—and using this formula:
Dotless-IP = (a x 16777216) + (b x 65536) + (c x 256) + d
So that you are not vulnerable to this kind of attack, make sure you update your browser if you are running Internet Explorer 4.0 or 4.01—the benefits of Internet Explorer 5.0 greatly outweigh the time it takes to perform the upgrade. Also, refer to Knowledge Base article Q168617, "Update Available for Dotless IP Address Security Issue," for more information on this matter.
Security Zones in Other Tools
Other Internet tools can use zones because support for zones is built into the URL Moniker dynamic-link library (DLL) called URLMon.dll, not the core Internet Explorer engine. (You can find more information about functionality in URLMon on the MSDN CDs or at http://msdn.microsoft.com.) For example, Microsoft Outlook 2000 uses zones to determine whether to run script and active content in HTML-formatted messages. You access these settings in Outlook 2000 like so:
- Open Outlook 2000.
- Choose Options from the Tools menu.
- Click the Security tab.
You can now set the zone, as shown in Figure 4-3, in which e-mail will be opened; it's highly recommended that you choose the Restricted Sites zone. When you open an e-mail with dynamic content embedded in HTML-formatted text, the HTML will execute as though it came from a distrusted Web site.
More information about security zones can be found in Knowledge Base article Q174360, "How to Use Security Zones in Internet Explorer," at http://support.microsoft.com/support/kb/articles/Q174/3/60.ASP.
Securing E-Mail Containing HTMLIt's very easy to send e-mail from a bogus source because many SMTP servers do not authenticate the sender first. For example, an attacker could send a fake e-mail to you from your manager. It's a common prank! A knowledgeable user will know to look at the SMTP headers to see that the user was not authenticated, but most e-mail readers hide the headers from you by default.
This can be an issue for e-mail readers that use HTML-formatted text. You might decide to trust e-mail from a specific location (because of your zones configuration), but an attacker could spoof a trusted address and send you a malicious HTML-based e-mail message that is a security threat to your system.
A way around this is to use digitally signed e-mail using technologies such as S/MIME (Secure/Multipurpose Internet Mail Extensions), which Microsoft Outlook 2000 supports. When you digitally sign an e-mail message, users can verify that the message was not tampered with and thus that the message came from you and not an imposter.
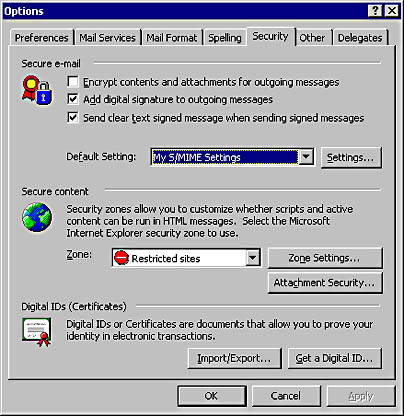
Figure 4-3. Setting zones in Outlook 2000.
EAN: N/A
Pages: 138