6.5. Mail Server Configurations
| < Day Day Up > |
| So far we've discussed some of the attacks possible against mail servers and brought up a number of additional security-related issues. We've also introduced several methodologies to protect servers from attack and stem the flow of unwanted mail. That is, we've discussed what the problems are, and to some extent, what solutions exist. We now turn our attention to where you can put some of these solutions into effect. In order to examine specific "cases" of mail servers, we have to look at our infrastructure purely in the context of mail flow. We no longer care what a server is, only how it handles mail. Figure 6-3 shows four kinds of mail servers: the mail relay, the internal/external mail servers, and the null-client. Figure 6-3. Four classes of servers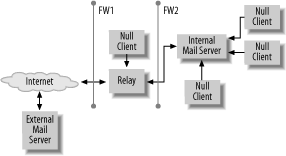 This is by no means the only possible mail architecture, merely one of the most commonly seen in small to medium sized companies with typical electronic messaging requirements. In particular, the flow of mail into and out of an organization may be handled by completely different sets of servers. There may be cases where flows need to be split so that inbound mail is processed by a different set of rules and restrictions than outbound mail. In most situations, however, single servers are capable of handling bidirectional flows. 6.5.1. Null ClientThe null client is a workstation or server that performs no local delivery and accepts no mail from outside the system. Any mail generated from the system is immediately sent to one preconfigured server. Most servers that do not handle mail for a living fall into the null client category. Workstations that do not perform local delivery may also be null clients. Virtually all desktop systems, whether they run Windows, Mac OS, or some kind of Unix, should be configured as null clients. Fortunately configuring null clients is simple:
No other mail "intelligence" is required for a null client. Generally, the configuration never changes throughout the life of the machine, even though the mail software will be periodically upgraded. 6.5.2. Internal Mail ServerThe internal mail server is a particularly complex system. It not only houses an MTA, which accepts mail from the mail relay and local null clients, it also performs local delivery and provides mail access. Finally, it's responsible for taking any mail not destined for the organization and passing it on to the mail relay. When configuring your internal mail server, keep in mind the following:
While this is not an exhaustive list of configuration possibilities on an internal mail server, you should give careful thought to each one. 6.5.3. Mail RelayA mail relay can provide an excellent strategic opportunity to the mail administrator. Figure 6-3 shows a mail architecture where every message entering and leaving the organization passes through this system. This is the ideal system to make early accept/reject decisions for incoming and outgoing mail.
When configuring your mail relay, refer to the first six bullets in the checklist for your internal mail server. They apply here also. In addition, consider the following:
While these options are not exhaustive, you should carefully evaluate each for your mail relay. 6.5.4. External Mail ServerNot all organizations have an "external mail server." This is the server that lets remote users send and receive mail directly without the use of a webmail gateway or VPN. Sometimes these servers are placed along side a mail relay in the perimeter network. Other organizations choose to place them outside of any firewalls. The external mail server should be configured just like an internal mail server. However, since these servers often need to relay mail for users from unknown networks, authenticated SMTP and encrypted sessions are mandatory. In addition, external mail servers sometimes perform all mail duties for an organization, especially for organizations whose business it is to provide mail access to customers. In these cases, they may be strategically important just like the mail relay. You should evaluate all the configuration guidelines recommended for a mail relay on these systems also. Now that we have covered problems and solutions in a general sense, it's time to get down to specifics. We now examine how to configure our mail servers to ensure they do what we need. To be able to answer these questions, let us first look at the relevant software. |
| < Day Day Up > |
EAN: 2147483647
Pages: 142
