Using the Group Policy Tools
Using the Group Policy Tools
The Group Policy tools in Windows contain a lot of improvements. The sections following this one describe each of these tools and how to use them. Some of these enhancements deserve special mention, though. First is Group Policy Update Tool (Gpupdate.exe). Group Policy refreshes policies every 90 minutes by default. In Windows 2000, if you changed a policy and wanted to see the results immediately, you had to use the commands secedit /refreshpolicy user_policy and secedit /refreshpolicy machine_policy. Gpupdate.exe replaces both of these commands in one command that's easy to use. You don't need to use this tool when updating the local GPO, though, because changes to the local GPO are instant.
Second is Resultant Set of Policy (RSoP). Windows includes new tools for seeing which policies the operating system is applying to the current user and computer and the location where they originated. One of the toughest parts of administering Group Policy on a large network is tracking down behaviors that result from combinations of GPOs that you didn't intend or didn't know were occurring. These tools help you track down these behaviors much faster than you could with Windows 2000, because they give you a snapshot of how the operating system is applying them and where they originated.
Gpresult
Group Policy Result Tool (Gpresult.exe) displays the effective policies and RSoP for the current user and computer. This section describes its command-line options.
Syntax
gpresult [/s Computer [/u Domain\User /p Password]] [/user TargetUserName] [/scope {user|computer}] [/v] [/z]
/s Computer | This specifies the name or IP address of a remote computer. (Don't use backslashes.) It defaults to the local computer. |
/u Domain\User | This runs the command with the account permissions of the user specified by User or Domain\User. The default is the permissions of the current console user. |
/p Password | This specifies the password of the user account that the /u option specifies. |
/user TargetUserName | This specifies the user name of the user for whom you want to display RSoP. |
/scope {user|computer} | This displays either user or computer results. Valid values for the /scope option are user or computer. If you omit the /scope option, Gpresult.exe displays both user and computer settings. |
/v | This specifies that the output will display verbose policy information. |
/z | This specifies that the output will display all available information about Group Policy. Because this option produces more information than the /v option does, redirect output to a text file when you use the parameter gpresult /z >c:\policy.txt. |
/? | This displays help. |
Examples
gpresult /user jerry /scope computer gpresult /s camelot /u honeycutt\administrator /p password /user jerry gpresult /s camelot /u honeycutt\administrator /p password /user jerry /z >c:\policy.txt
Gpupdate
Gpupdate.exe refreshes local and network policy settings, including registry-based settings. As I mentioned, this command replaces the obsolete command secedit /refreshpolicy.
Syntax
gpupdate [/target:{computer|user}] [/force] [/wait:value] [/logoff] [/boot] [/sync]/target: {computer|user} | This processes only the computer settings or the current user settings. By default, both the computer and user settings are processed. |
/force | This ignores all processing optimizations and reapplies all settings. |
/wait: value | This is the number of seconds that policy processing waits to finish. The default is 600 seconds. A value of 0 means “don't wait,” and a value of -1 means “wait forever.” |
/logoff | This logs the user off after the refresh has completed. This is required for those Group Policy client-side extensions, such as user Software Installation and Folder Redirection, that do not process on a background refresh cycle but do process when the user logs on. This option has no effect if there are no extensions called that require the user to log off. |
/boot | This restarts the computer after the refresh is finished. This is required for those Group Policy client-side extensions, such as computer Software Installation, that do not process on a background refresh cycle but that do process when the computer starts up. This option has no effect if there are no extensions called that require the computer to be restarted. |
/sync | This switch synchronously (in the background) applies the next boot or user logon policy. |
/? | This displays help. |
Examples
gpupdate gpupdate /target:computer gpupdate /force /wait:100 gpupdate /boot
Simulating Folder Redirection
IT professionals often ask me about Folder Redirection. Specifically, they want to know how to simulate this policy when they haven't yet deployed Active Directory. Active Directory is a requirement for this policy, after all.
Although you can't achieve automatic folder redirection without Active Directory, you can simulate it. Configure the key User Shell Folders to redirect My Documents and other folders to a network location. This key is in HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer and contains one value for each of the special folders that Windows supports. They are REG_EXPAND_SZ values, so you can use environment variables, such as %UserName% and %HomeShare%, in the path. This means that even on a Windows NT–based network, you can use redirected folders.
I suggest that you script this customization so that you can apply it uniformly. Chapter 4, “Hacking the Registry,” describes the key User Shell Folders in great detail, and it also contains a sample script that automatically redirects folders. In a business environment, be careful to test this customization prior to deploying it to a production environment. In particular, make sure it works with the permissions of the network share to which you're redirecting the folders.
Help and Support Center
Although Help and Support Center's RSoP report is of limited use to IT professionals because you can't use it remotely, users can run it on their own computers to check policy settings. This tool provides a user-friendly, printable report of most policies in effect for the computer and console user. Figure 7-7 shows a sample of this report. Here's how to use this tool in Windows XP:
Click Start, and then click Help And Support.
Under Pick A Task, click Use Tools To View Your Computer Information And Diagnose Problems.
Click Advanced System Information, and then click View Group Policy Settings Applied.
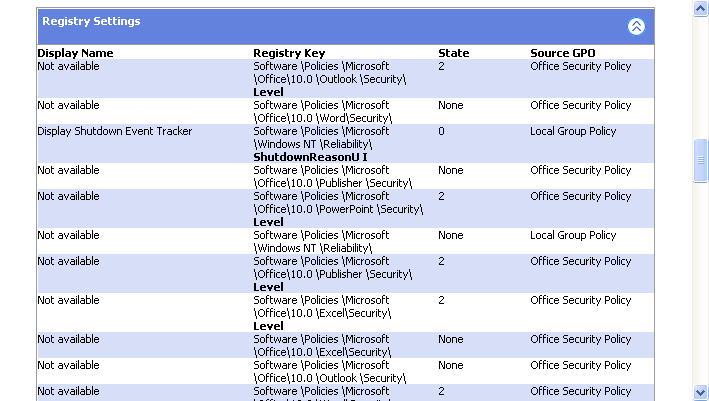
Figure 7-7 Help and Support Center's RSoP report contains the same type of information as Gpresult.exe contains, but it's more readable and more suitable for printing.
Resultant Set of Policy
Although Help and Support Center's RSoP report isn't suitable for use by IT professionals, the RSoP snap-in is suitable because you can use it to view RSoP data for remote computers. You use this tool to predict how policies work for a specific user or computer, as well as for entire groups of users and computers. Sometimes, GPOs applied at different levels in Active Directory conflict with each other. Tracking down these conflicting settings is difficult without a tool like this snap-in.
The RSoP snap-in checks Software Installation for applications associated with the user or computer. It reports all other policy settings, too, including registry-based policies, redirected folders, Internet Explorer maintenance, security settings, and scripts. You've already seen two tools that report RSoP data: Gpresult.exe and Help and Support Center (Windows XP only). The RSoP snap-in is almost as easy to use. (Your account must be in the computer's local Administrators group to use this tool.)
Click Start, Run, and type mmc.
Click File, Add/Remove Snap-In, and then in the Add/Remove Snap-in dialog box, click Add.
In the Add Standalone Snap-In dialog box, select Resultant Set Of Policy, click Add, and then click Close.
In the Add/Remove Snap-In dialog box, click OK.
Right-click Resultant Set of Policy, and then select Generate RSoP Data.
In Resultant Set of Policy Wizard, click Next, and then click Next again.
On the Computer Selection page, select Another Computer, type the name of the computer that you want to inspect, and then click Next.
On the User Selection page, select the user for whom you want to display RSoP data, and then click Next.
Click Next, and then click Finish to close the wizard.
To view the results, expand the username node in the console.
Figure 7-8 shows the results. In this example, you see the password policies applied to the computer. You also see the GPO that's the source for each setting.
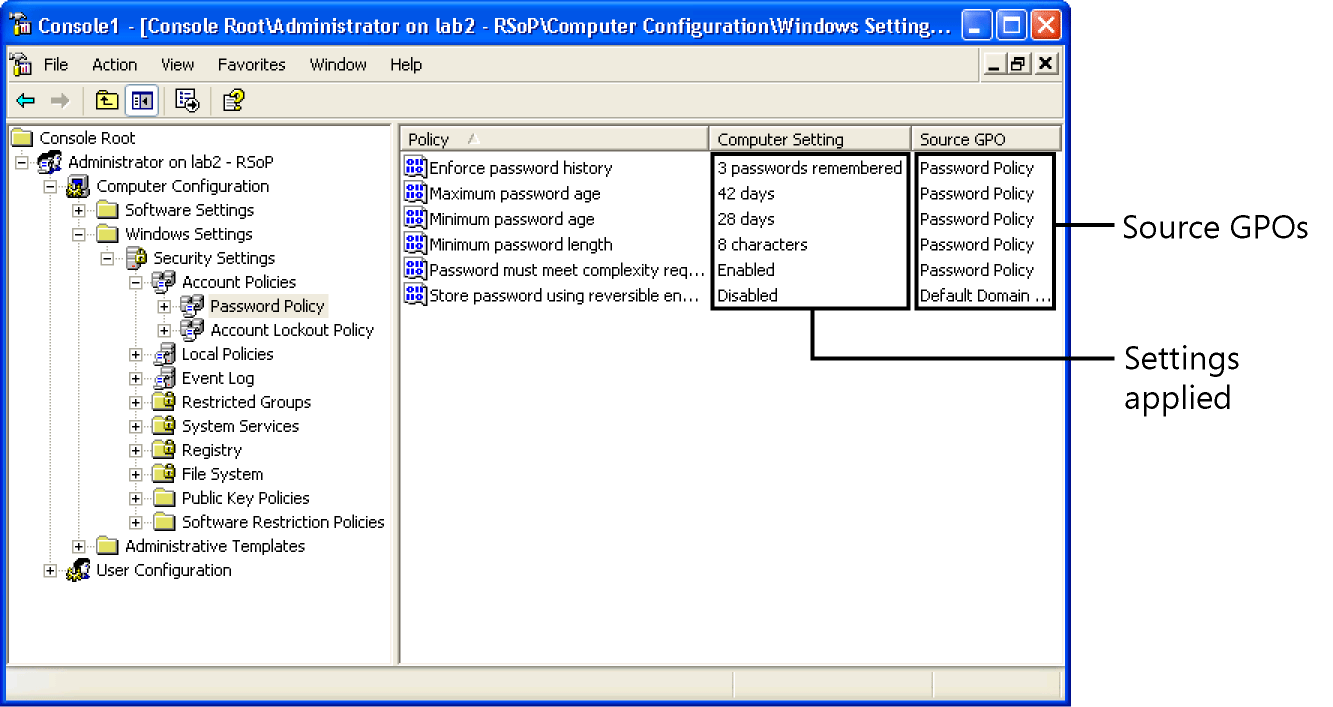
Figure 7-8 The RSoP snap-in is the best tool for figuring out the source of policy settings when multiple GPOs apply to a computer.
EAN: 2147483647
Pages: 186