Multiprocessor Systems
| < Day Day Up > |
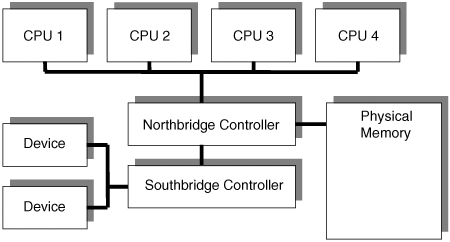
| Multiprocessor systems (sometimes known as Symmetric Multi-Processing [SMP] systems) and hyper-threaded systems come with their own unique set of problems. The major issue they pose for rootkit developers is synchronization. If you have written multi-threaded applications, you have already come to understand thread safety (we hope!), and what can happen if two threads access a data object at the same time. If you haven't, suffice it to say that if two different operations access the same data object at the same time, the data object will become corrupted. It's like having too many cooks in the kitchen! Multiple-processor systems are like multi-threaded environments in a way, because code can be executing on two or more CPUs at once. Chapter 7, Direct Kernel Object Manipulation, covers multiprocessor synchronization. The layout of a typical multiprocessor system is shown in Figure 3-8. As the figure illustrates, multiple CPUs share access to a single memory area, set of controllers, and group of devices. Figure 3-8. A typical multiprocessor bus layout. Some points to remember about multiprocessor systems: Every CPU Has its Own Interrupt Table. If you hook the interrupt table, remember to hook it for all the CPUs! If you don't, then your hook will only apply to a single CPU. This may be intentional if you don't need to have 100% control over an interrupt but this is rare.
|
| < Day Day Up > |
EAN: 2147483647
Pages: 111
- An Emerging Strategy for E-Business IT Governance
- Assessing Business-IT Alignment Maturity
- Linking the IT Balanced Scorecard to the Business Objectives at a Major Canadian Financial Group
- Measuring and Managing E-Business Initiatives Through the Balanced Scorecard
- Technical Issues Related to IT Governance Tactics: Product Metrics, Measurements and Process Control