| Security Monitor has the flexibility to create your own custom script and integrate that with the Security Monitor. This section examines one of those scripts for e-mail notification. The discussion of this case study is based on the following Cisco document: http://www.cisco.com/en/US/products/sw/secursw/ps2113/products_configuration_example09186a00801fc770.shtml#foursensor Security Monitor has the ability to send e-mail notifications when an Event Rule is triggered. The built-in variables that can be used within the e-mail notification for each event do not include things such as the Signature ID, the source and destination of the alert, and so forth. This document provides instructions for configuring Security Monitor to include these variables (and many more) within the e-mail notification message. Follow the procedure outlined in the next section to configure e-mail notifications. Configuration Steps Configuration steps for e-mail notification with additional details on the e-mail involve writing Perl scripts to retrieve additional information and defining event rules for defining the triggering criteria. Follow this procedure to accomplish this task: Step 1. | Copy and paste the script into a Notepad file from the link that follow, name it emailalert.pl (if you want, you can give it a different name), and save it into the $BASE\CSCOpx\MDC\etc\ids\scripts directory on the VPN/Security Management Solution (VMS) server.
http://www.cisco.com/en/US/products/sw/secursw/ps2113/products_configuration_example09186a00801fc770.shtml#foursensor
This allows you to select it later in the process when you define an event rule. The script contains comments explaining each portion and any required input.
| Step 2. | Edit the emailalert.pl file with Notepad to modify the $EmailRcpt variable (near the top of the file) to be the e-mail address of the person who is to receive the alerts.
| Step 3. | Define an Event Rule within Security Monitor to call a new Perl script. To do this, from the main Security Monitor page, select Configuration > Event Rules and add a new rule.
| Step 4. | On the Specify the Event Filter screen, add the filters that you want to trigger the e-mail alert (in the sample that follows an e-mail will be sent for any high severity alert) as shown in Figure 22-4.
Figure 22-4. Event Filter Screen 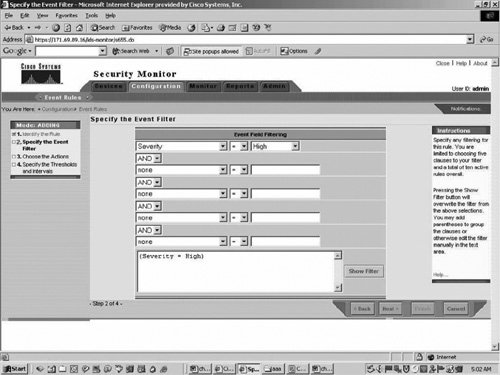
| | | Step 5. | On the Choose the Action screen, check the box to execute a script and select the script name from the drop-down box.
| Step 6. | In the Arguments section, enter "${Query}" as shown in Figure 22-5. Note that this must be entered exactly as it is here, including the double-quotes. It is also case sensitive.
Figure 22-5. Event Filter on the Choose the Action Screen 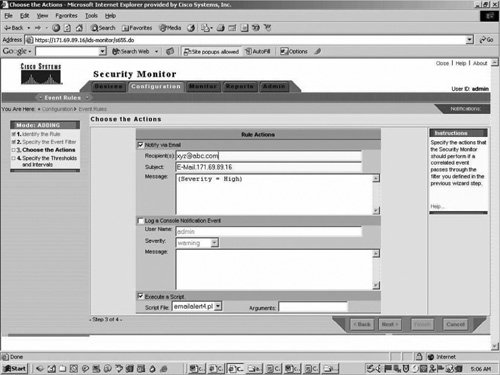
| Step 7. | At this point, when an alert, as defined in your event filters (in this example, a high severity alert) is received, the script called emailalert.pl is called with an argument of ${Query} which contains additional information about the alert. The script parses out all the separate fields and uses a program called blat to send an e-mail to the e-mail recipient as defined in step 2.
| Step 8. | Install blat with the command: blat -install <SMTP server address> <source email address>. Once blat is installed, you are finished with the configuration steps.
|
Note Blat is a freeware e-mail program used on Windows systems to send e-mails from batch files or Perl scripts. It is included as part of the VMS installation in the $BASE\CSCOpx\bin directory. To verify your path settings, open a command prompt window on the VMS server and type blat. If you receive the File not found error, either copy the blat.exe file into the winnt\system32 directory, or find it and open it from the directory in which it is located.
Troubleshoot E-mail Notification Follow these steps to troubleshoot the e-mail notification issue: Step 1. | Be sure your SMTP mail server is configured correctly. You can use the following commands in the command prompt of the Security Monitor server to verify that the SMTP server is working correctly:
telnet <mail server> 25 helo <your domain name> mail from: notifier.<server name>@yourdomainname.com rcpt to: <your email address> data (High Severity alert) .
If your mail server is working correctly, you should receive this e-mail. It is important to note that you need to set your SMTP server to allow non-authenticated connections (i.e., no username/password has to be provided to submit e-mail).
| Step 2. | Next, check that blat is working properly by running the following from a command prompt: blat <filename> -t <customer's email> -s "Test message" where <filename> is the full path to any text file on the VMS system. If the user to whom the e-mail script is directed receives this file in the body of an e-mail, then you know that blat is working.
| Step 3. | If no e-mail is received after an alert is triggered, try running the Perl script from a command prompt window. This highlights any Perl or path type issues. To do this, open a command prompt and enter the commands shown in Example 22-5.
Example 22-5. Commands Needed If No E-Mail Notification Is Received > cd Program Files/CSCOpx/MDC/etc/ids/scripts > emailalert.pl ${Query}
|
| Step 4. | You might receive the following Sybase error:
C:\Program Files\CSCOpx\MDC\etc\ids\scripts>emailalert.pl ${Query} ERROR: An Exception has occurred : SybaseESql::prepareSql: PREPARE Syntax error near 'Query'
This is because the ${Query} parameter you are passing does not actually contain information, which is not the case when it is passed from the Security Monitor.
| Step 5. | Other than seeing this error, the script should run correctly and send an e-mail. Any alert parameters within the e-mail body will be blank. If you receive any Perl or path errors, they need to be fixed before an e-mail is sent.
| | | Step 6. | If blat is working correctly from command prompt, the next step is to verify whether the IDS_Analyzer daemon and IDS_Notifier daemons are running. If either one is not running, start these daemons.
| Step 7. | If you still have problems, generate an Audit Log Report for both IDS_Analyzer and IDS_Notifier. The IDS_Analyzer daemon will report when it submits a notification request, and the IDS_Notifier daemon will report success or failure messages when it receives the request. If any error messages display, correct the problem based on the message. Otherwise, go to the next step.
| Step 8. | If everything is working up to Step 6, then your event rule might not be getting triggered. This could be because of misconfiguration in the event rule. For example, if you have an event rule such as "SEVERITY = HIGH AND SEVERITY = MEDIUM", this rule will never trigger because a particular event will have only one severity and so it will not match any of the events. To get this working, either define one severity or change the "AND" to "OR." Then the rule will trigger on seeing both Medium and High Alarms.
|
|

