Digest Authentication
|
|
Digest authentication is available if you are using Active Directory accounts, and although it has some associated security risks, it is a more secure means of authentication than Basic authentication. Digest authentication is not intended to be a complete answer to security on the web; it is designed only to avoid the problems associate with Basic authentication. In addition to Active Directory, Digest authentication requires use of HTTP 1.1, so it will work only with newer browsers that support that protocol.
Digest authentication requires that the domain controller keep a plaintext copy of each password, so it can check that password against the hash sent by the client. Therein lies the security risk. Having plaintext passwords stored anywhere is a security risk, so if you choose this form of authentication, you will need to make sure that the domain controller is secure from intrusion, or passwords can be compromised. The upside to using Digest authentication is that the password is not sent across the network in plaintext, unlike with Basic authentication.
Here's how Digest authentication works:
-
The server sends the client a note that Digest authentication is required for this resource.
-
The server also sends the client a 'nonce,' some randomly generated information to include in the authentication hash. This information helps prevent replay attacks.
-
The client adds this information to its username/password combo and performs a one-way hash on it using the MD5 hashing algorithm.
-
The client sends the hash to the server. It also sends the nonce in clear text.
-
The server takes the nonce data, combines it with the local plaintext copy of the username/password combo, and performs a one-way hash on it using the MD5 hashing algorithm.
-
This hash is compared to the one received, and if they match, the authentication is accepted.
Advanced Digest Authentication
Advanced Digest authentication is exactly like Digest authentication with one important difference: In Digest authentication, passwords are stored on the domain controller as an MD5 hash, rather than as clear text. This prevents anyone from figuring out the password. Advanced Digest authentication is supported in HTTP 1.1, so any HTTP 1.1-compliant browser should work. Advanced Digest authentication is a better choice than Digest authentication because of the extra security provided.
Advanced Digest authentication has the following requirements:
-
You must be running Active Directory.
-
Both the IIS server and a domain controller must be running WS03.
-
The clients using Advanced Digest authentication must be running at least IE 5.
-
The user account must be in an Active Directory domain that is trusted to the IIS server (or the same domain).
Note If the domain controller and the IIS server are not both running WS03, IIS will automatically fall back to using regular Digest authentication.
Enabling Advanced Digest Authentication
Advanced Digest authentication is enabled in the metabase, and you can apply it at any level in the W3SVC. (W3SVC is the name the Web Server Service goes by in the Metabase.) This metabase setting is inheritable by all child levels. The metabase property for Advanced Digest authentication is UseDigestSSP. Here's how to enable it:
-
Open the MetaBase.xml file in Notepad (assuming edit-while-running).
-
Go to the level at which you want to enable Advanced Digest authentication.
-
Type in UseDigestSSP='TRUE', as shown in Figure 7-1.
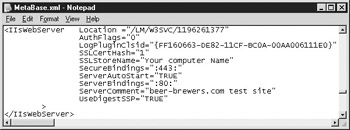
Figure 7-1: Metabase file with UseDigestSSP -
Save and close the file.
-
Open the IIS MMC, and open the Authentication Methods window for the level at which you want to enable Advanced Digest authentication. To do this, right-click a node in the left pane of the MMC and select Properties. Then open the Directory Security tab and click the Edit button.
-
Put a check in the checkbox for Digest Authentication For Windows Domain Servers.
-
Type in the Realm, or click the Select button to choose the Realm. In Advanced Digest authentication, the realm is important and needs to match the domain or realm that will authenticate the clients.
-
Click OK.
-
Click OK again.
Following is the process that the client and server go through when using Advanced Digest authentication:
-
The server sends the client a note that Digest authentication is required for this resource (Digest and Advanced Digest use the same protocol).
-
The server also sends the realm name.
-
The client then takes the username and password, combines them with the name of the realm, and creates an MD5 hash. It then submits a request for the resource to the server, sending the MD5 hash in the header of the HTTP request.
-
The IIS server sends this hash to the domain controller for verification.
-
The domain controller verifies this hash against the hash stored in Active Directory. If they match, the domain controller sends the IIS server an acknowledgment.
|
|
EAN: 2147483647
Pages: 193