Different Types of Hacks and How They Work
Most hacks seek an entry point to the system. The entry point could be reading the network packets or social engineering the person who has a password. The entry point is important because of its potential to expose the security leak. In this section I address social engineering, cracks in the system, and passive and active hacks. A passive hack attack is one in which nothing is changed or harmed on the system. Both of the previous examples, keystroke monitoring and replay attacks, are examples of passive attacks. The other type of hack is an active hack attack . During an active hack programs are changed and corrupted. An example of an active hack is changing the organization's Web pages. Social engineeringSocial engineering is the ability to gain access to systems by social interaction. The interaction may be formal or informal in nature. A renowned tactic is to call in as a senior officer's wife or secretary to the IT department and complain that a password isn't working. The next step is to convince the IT department to perform the reset password process. IT departments and customer service centers could be a weak link unless they strengthen their authentication process. Some centers have employed techniques like requesting a mother's maiden name and other weak passwords before they regenerate a password. Once this is done, they will only send the password by e-mail, which further weakens the process. Some of the biggest cracks into computers stem from people acquiring information in a social environment. Understanding an organization's systems can best be gained by being good friends with the people who install or maintain them.
A crack in the systemMonitoring a secure system might not do much good unless there is a crack in the security of the system. A crack is a way to break a system. Just like someone who wants to rob a house and not get caught, the hacker must establish a plan for entering the system, grabbing assets, and covering his or her tracks. The difference between robbing a house and grabbing resources from an organization is that a hacker can leave digital fingerprints that can be erased after the crime. There is still the risk of getting caught, so the hacker usually has a motivation worth getting into trouble for if he is ever caught. For example, if an organization advertises the distribution of new software that will make a lot of money, a hacker is likely to go after that resource. A hacker will case the place or, in other words, monitor the traffic going in and out of the organization for security vulnerabilities. The hacker might even attach a program to act as a listener, or sniffer , to discover security vulnerabilities. The sniffer can save the information to a log and send the information to the hacker's secure system. After the place looks safe and the hacker has sufficient knowledge to accomplish the hack, the hacker will perform the hack. The hack may involve further penetration into the system such as creating a backdoor (a login that bypasses security mechanisms), or grabbing a new program, or placing an e-mail monitoring device on a CIO's computer system. When the break in occurs, like any other professional, the hacker is going to have tools (in this case software tools) that are used to thwart security defenses. Some attacks are not planned. For example, a hacker may FTP into a company site and accidentally find the company's source code open to the world and take it. Granted, the company source should be protected, but if it is not someone is bound to take it. Other hackers may be a little more physical, such as stealing a laptop from the organization so that they can scan the hard disk; there are tools that can be used to scan the physical hard disk without login. They could then use the information found on the laptop. These resources could be bank account numbers, credit card numbers , passwords, computer programs, or anything else of value.
The passive hack attackAs I mentioned earlier, hacks are broken down into two modes of operation: the passive hack attack and the active hack attack . These hacks do not have to be done together or in any order. The passive hack is merely observing information without corrupting or changing the information. The passive hack includes:
Nothing may come of the information found in these scans . The hacker could be doing a scan to understand the organization's systems. Figure 2-1 shows how a passive hack may work. 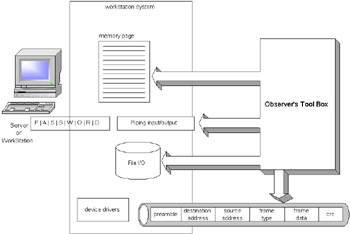 Figure 2-1: Passive hack attacks
The active hack attackThe purpose of the active hack attack is inherently different than the passive one; the active hack not only infiltrates but also corrupts the organization's systems for the hacker's use. The active hack may involve viruses, worms, backdoors, impersonators, and redirectors. An example of an active hack is a corrupted site or Web page. Another active attack is the denial of service attack . The denial of service attack prevents users from accessing system resources. For example, some servers will not allow users to fail a login more than a specified number of times, so a hacker will try to log in until a user's account is disabled and the user no longer has access to the server. Figure 2-2 demonstrates the active hack attack. 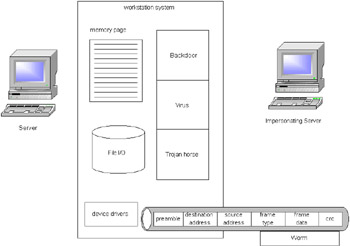 Figure 2-2: Active hack attacks
The motivation behind active and passive attacks is different. The passive attack is similar to spying to retrieve information. The active attack is motivated by the need to destroy the organization's computer. A disgruntled employee or a competing company could motivate the active attack. The passive attack hides the attack by not showing signs that anyone has been on the system. The active attack hides the attack by destroying enough of the system so that no digital fingerprints are left on the system. The active and passive attack can be used in combination to both read information and cover the tracks of the hacker. The passive attack, while not destroying the systems, can also do harm to the overall organization. The hacker who gets information from the passive attack can use it for insider trading, to publish derogatory information about the organization, or to publish the organization's trade secrets.
Java Security Solutions ISBN: 0764549286
EAN: 2147483647 Year: 2001
Pages: 222 Authors: Rich Helton, Johennie Helton
flylib.com © 2008-2017. If you may any questions please contact us: flylib@qtcs.net |