Java Security Models
The Java platform has two main goals for security: One is to provide a secure platform on which to run Java-enabled applications, and the other is to provide security tools and services to enable secure applications. The Java platform security at first used the sandbox model, a collection of safe resources that unauthorized code could access, and now it has evolved into a policy-based security model. The sandbox modelThe sandbox model refers to the original security model provided by the Java platform. It provided a very restricted environment to run untrusted code. The basic idea was that downloaded code, such as an applet, was not trusted and, therefore, should not access vital resources (such as the file system). Local code, however, was trusted and had full access to system resources. Figure 26-1 shows the original sandbox model. 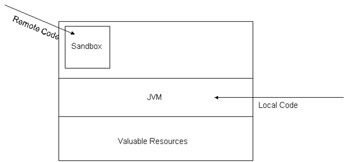 Figure 26-1: The original sandbox model This model was very restrictive so the JDK 1.1 introduced the concept of signed applets . Applets are digitally signed to obtain extra permissions outside of the sandbox. Programs that are not digitally signed continue to be restricted by the original sandbox model. Java 1.1, however, gave unrestricted access to system resources to signed applets. It was an all-or-nothing type of access.
The Extended Java Sandbox is the default model for digitally signed applets. Under the Extended Java Sandbox, digitally signed Java code is allowed to read and write to a specified directory. In that directory, no executables can run and other Java programs cannot gain access to other network services. Next, in JDK 1.2, the Java Protected Domains Security model gives fine-grain control and selectively grants access to network resources. Under this model, administrators can tailor security policies to match security requirements. For instance, the administrator may grant read access to some files in a directory to all users and write access to managers, all based on the resource being accessed and the identity of the user . The concept of domains is important and is a base for system security. A domain is a group of permissions that are provided to Java code. These permissions are based on the program's origin and its digital signature. The problem with protected domains is that the policy file needs to be modified by the end user, and this requirement is impractical . Security in J2SDK v 1.4The J2SDK v 1.4 has enhanced its security; you may want to look at the http://java.sun.com/security/index.html site for more information. That site includes documentation, user guides, and articles specific to Java security. Now the J2SDK provides a security model that is policy-based, which is easily configurable and provides fine-grained access control. The policy guards a resource and specifies which permissions are available. Unless permission is granted to code to access a protected resource, the code cannot access it. This access control can be specified for all Java code such as applications, beans, and applets. There is no longer a built-in concept that all local code is trusted. Here is a brief summary of the security changes included in the J2SDK v 1.4:
J2EE securityThe J2EE server enforces security at two levels: authentication and authorization. Authentication is the process by which a user proves his or her identity. Recall that you define roles and permissions to access resources. In addition, the deployer maps the roles to principals. The details of how the EJB server provides authentication is vendor-specific. Some may use the underlying operating system services and others may use some type of Public Key Infrastructure (PKI). Also, the way principal delegation is performed is provider-specific. Recall that the principal of the requestor for a resource is normally propagated. Therefore, the roles and permissions need to be set accordingly . For instance, some beans should be allowed to call other beans that the user may not have access to. This is very similar to the doPrivileged() method in java.security.AccessController .
JAAS is Java's default security model to grant permissions based on where the code comes from. Authorization is the process to establish whether the requestor to a resource has the proper rights or permissions to access it. Using JAAS, authorization can be accomplished declaratively and programmatically.
Policy fileAs mentioned earlier, Java 2 security is policy-based and uses the java.policy file to specify the security policies that control the resources the application (or applet) can access. In the policy reference implementation, the policy can be specified within one or more policy configuration files. Recall that these files contain a list of entries that map the permissions allowed for code from specific sources. Also, the policy configuration file may contain a keystore entry to look up the public keys of the signers in the grant entries.
Java Security Solutions ISBN: 0764549286
EAN: 2147483647 Year: 2001
Pages: 222 Authors: Rich Helton, Johennie Helton
flylib.com © 2008-2017. If you may any questions please contact us: flylib@qtcs.net |