2.6 Holiday Break-In
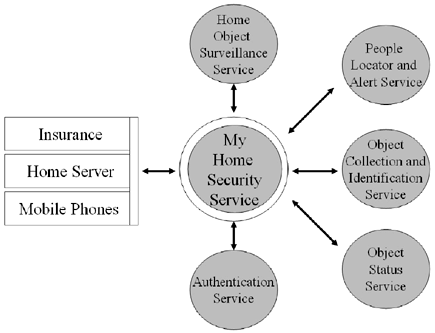
2.6.1 IntroductionDan and his family leave for a long-needed holiday. They plan to spend two weeks at the Cannes Film Festival. On the third day of their trip, burglars break into their home and steal most of their valuables, including their computer system, home theater system, silverware, and several pieces of priceless jewelry . During their raid, they also deliberately break several items in the home, including their cabinet of fine china and an antique curio holding Dan's wife's Lladro collection, the value of which the burglars do not realize. A neighbor notifies Dan at the hotel and the family cuts their trip short to return home and assess their losses. 2.6.2 The PresentUnfortunately, this scenario is all too common. Today, there are a few options to protect against such a scenario, but the biggest problem would be the assets in the home. Dan did what he could to prepare for such a scenario. A year before this burglary took place, Dan's neighbor suggested that he videotape the contents of his home for insurance purposes. Dan takes this a step further and describes each item he photographs to the best of his ability, including his idea of each item's approximate value. Dan stores the videotape in a safe deposit box at his bank. He also has a motion-sensor alarm system installed, which notifies a central alarm office when activated. The central office first telephones the home to determine whether the alarm was tripped accidentally or it's a real security breach. If they receive no answer within a few minutes, they then notify the police, who are dispatched to investigate. In this case, the police are notified within ten minutes of the break-in and arrive at Dan's house within twenty minutes. By this time, the burglars are long gone and the damage is done. Dan files his insurance claim using the videotape he created for reference. The problem is that the tape is over a year old, and many of the stolen items are not recorded. To compensate for items he may not remember, Dan claims several items that were not stolen, and fudges the age and approximate value of many of the known items. The insurance company settles his claim without incident and he is satisfied with the reimbursement. However, a month later, he discovers that his insurance premium is increased by fifteen percent as a result of both his claim and the continuous problem of insurance fraud that plagues the industry. 2.6.3 The FutureAs we have seen in this chapter, tomorrow's world will be much different. More things will have chips built into them that will enable them to communicate with other devices nearby, as well as with the Internet. These chips provide information such as the status of the object and its location. Instead of Dan's videotape, which contains ad hoc and unreliable descriptions of his home's contents and their value, every item in his home - including furniture, cupboards, even walls and artwork, in addition to electronic devices - will register itself into an electronic catalog. The system will check each item's status and record the appropriate information, including exact descriptions of each item's age, condition, and value. Some items, such as the priceless jewelry, will be keyed in manually because they will not contain chips to identify themselves . But high-quality photographs will accompany all items, facilitating claim procedures and assessments. After an online registration, all of this information will transfer over a WLAN into a database on the home server, which in turn is linked to the insurance company over the Internet, as well as a replacement service that will monitor the status of each item and process replacements should that status change. Before Dan leaves for his vacation, he tells his alarm system to automatically notify the police if triggered. The system thus knows that Dan isn't home without him having to disclose this sensitive information to another human being. Once Dan activates the service, the objects with chips built in begin to monitor their own status and that of neighboring objects. An XML description is used to communicate the status of each object. Either at regular intervals or in real time, changes in the status are filtered through the database and reported to the replacement service, the insurance company, and to Dan. When the break-in occurs, the police are dispatched immediately and arrive at the home within five minutes. Dan is automatically notified via his cell phone that a burglary has been reported and that the status of stolen and broken items has changed. The police aren't in time to prevent the burglary, but the thieves only manage to get away with Dan's stereo equipment and some jewelry, and in their scramble to get out of the house, they topple the curio housing the Lladro collection. As soon as the pieces shatter, the replacement service is notified and replacement pieces are processed immediately. They use an XML description to report the shipping status of each piece. Within a half- hour , the police use a GPS system to track the chips in Dan's stereo equipment. A van is pulled over minutes later, the burglars are arrested, and the equipment is returned. Dan is reimbursed for the jewelry and the Lladro collection. He claims that his receiver was broken during the burglary, but what he doesn't know is that his son broke the receiver just before they left for their holiday. The database informs the insurance company that the receiver was in fact broken before the burglary took place, so he is not reimbursed accordingly . A month later, Dan discovers that his insurance premium has been lowered by two percent because of the efficiency of the system he has in place. 2.6.4 SummaryThis implementation combines several of the me-centric features that we've seen already in this chapter, with several advantages to these features easily recognized in this scenario. In the present situation, items in the home are too diverse to be treated by a single system such that we will see in the future. Although many household devices today have chips built in, they lack an Internet connection or even a local connection to exchange information. No system knows about the existence of any others, and there is no central system that knows about all the items in the home. To realize such a service, it would be necessary to create an online service where homeowners can register all the items they have in the house. There are several problems with this approach. First, there is no standard way to describe the objects. Either one builds a catalogue of all products that have been built and sold over the last hundred years , or one lets the homeowners describe their goods themselves. With the catalogue, one could be sure that every item is described in a very precise way, but the catalogue would be too big to be handled by the homeowners. Every category would contain thousands of different items, and often the owner does not know how to describe the item best. The other option of free text does not really help either, because it makes it difficult to find a suitable replacement. Probably the best way would be to create generic categories (such as cabinet), define some attributes (such as size, material, and color ), and add a free text field where additional information can be entered to make sure that the item is described as clearly as possible. This still means lots of work without immediate reward, and is still not always accurate. To make it work, the system could focus only on consumer electronics and household devices. This means that the television set, the DVD player, the stereo, and the refrigerator would be registered at the service. These devices are easy to register because they have code names and numbers and are all standardized. Having their model names and numbers will not only make sure that a certain product is correctly described, but also the age and the approximate cost for the object. This makes it easier to find an equivalent replacement. It also helps insurance companies to evaluate the damage. The number of objects to be entered into the system will be probably be pretty lowaround tenmeaning that the effort is manageable and will ensure that many people will participate. However, the majority of household items would remain unprotected . Additionally, a change in each item's status would be impossible to monitor. We would still rely on unreliable user descriptions of broken or stolen items. Using today's technologies it is possible to implement the basic idea of this scenario, but due to the complexity of it, we doubt that there is a business plan to support the effort. It would not be possible to implement the technology with reasonable costs. Too many unknowns are in the project to make it reality. From an infrastructure point of view, the future scenario does not require much upgrade of today's networks. In-house communication can be based on WLAN, an agent will make sure that all affected parties are notified, and stolen items will be tracked via GPS. To make this service work, it would be necessary for every object in the house to be scanned into the catalog in some way. It will be impracticable for the next few years to introduce chips to all objects, but putting a bar code on each object would work. In this case, broken items would be re-scanned for replacement purposes. Soon, though, we can expect to buy furniture and other items that include a small chip that can transmit the existence and state of each object back to a central service hub automatically. In fact, each item in the home would have its own agent that would work on behalf of that item and make sure that everything is in order with it. The central service hub would know when to repair or replace the item. The service's ecosystem, shown in Figure 2.7, shows the required infrastructure services and the application services for the different parties involved. Figure 2.7. Home Security Ecosystem Another advantage to this system is that insurance fraud would be virtually eliminated. Because items report their own status to a central system, insurance customers will no longer be able to make inflated or even false claims, thus keeping insurance premiums for all customers at reasonable levels. Likewise, customers can rest easy knowing that accurate information is recorded for all of their valuables, so insurance companies cannot underestimate the value of any given item. Finally, stolen goods are easily tracked, not only ensuring their return to their rightful owners , but also increasing the likelihood that thieves will be caught red-handed. |
EAN: 2147483647
Pages: 88