Intrusion Detection
| Although it is possible for human monitoring to identify real-time intrusion events within small, tightly controlled networks, it is more likely that a human administrator will monitor alerts and notifications generated by intrusion-detection systems (IDSs). These software and hardware agents can monitor network traffic for patterns that may indicate an attempt at intrusion, called an attack signature , or can monitor server-side logs for improper activity or unauthorized access.
Methods of Intrusion DetectionIntrusion detection may be managed by two basic methods: knowledge-based and behavior-based detection . Knowledge-based detection relies on the identification of known attack signatures and events that should never occur within a network. Behavior-based detection involves the use of established usage patterns and baseline operation to identify variations that may pinpoint unauthorized access attempts. Knowledge-Based IDSThe most common form of IDS detection involves knowledge-based identification of improper, unauthorized, or incorrect access and use of network resources. The identification of known attack signatures allows for few false alarmsa known attack pattern is almost always a good sign of a danger to the network. Because the signature identifies a known method of attack, you can use detailed planning to counter and recover from the attack. Internet Control Message Protocol (ICMP) abuse and port scans represent known attack signatures. The Ping utility uses ICMP and is often used as a probing utility prior to an attack or may be the attack itself. If a host is being bombarded with ICMP echo requests or other ICMP traffic, this behavior should set off the IDS. Port scans are a more devious form of attack/reconnaissance used to discover information about a system. Port scanning is not an attack but is often a precursor to such activity. Port scans can be sequential, starting with port 1 and scanning to port 65535, or random. A knowledge-based IDS should recognize either type of scan and send an alert. Knowledge-based IDS may also monitor for patterns of access that have been established as never being appropriate within the monitored network (for example, communications directed at common ports used by services, such as unauthorized FTP or Web servers running on local systems). Knowledge-based IDS has several limitations, including the following:
Behavior-Based IDSOne of the most common workstation-level compromise-detection methods involves a user noticing an unusual pattern of behavior, such as a continually operating hard drive or a significantly slowed level of performance. The ability to detect anomalies from normal patterns of operation makes it possible to identify new threats that may bypass knowledge-based IDS. Highly secure environments may use complex patterns of behavior analysis, in some cases, learning individual usage patterns of each user profile so that variations can be identified. Here are some common features of behavior-based IDS solutions:
Although more flexible than knowledge-based IDS, behavior-based detection has several limitations, including the following:
Intrusion-Detection SourcesWhether knowledge based or behavior based, intrusion detection relies in the capability to monitor activity, identify potential risks, and alert the appropriate responsible parties. Monitoring may be performed on the network itself or on a host system, based on the security needs mandated by business requirements. Network-Based IDSNetwork-based IDS solutions monitor all network traffic to identify signatures within the network packets that may indicate an attack. The types of signatures include the following:
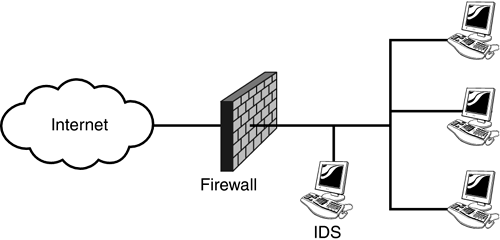
Figure 7.1 details a simplified network-based IDS solution monitoring traffic that passes through an organization's firewall to the systems within the protected network. Figure 7.1. An idealized example displaying a network-based IDS solution.
Table 7.1 details some of the strengths of network-based IDS solutions. Table 7.1. Strengths of Network-Based IDS
Host-Based IDSHost-based IDS solutions involve processes running on a host that monitor event and applications logs, port access, and other running processes in order to identify signatures or behaviors that indicate an attack or unauthorized access attempt. Some host-based IDS solutions involve the deployment of individual client applications on each host, which relay their findings to a central IDS server responsible for compiling the data to identify distributed trends. Table 7.2 details some of the strengths of host-based IDS solutions. Table 7.2. Strengths of Host-Based IDS
Layered Intrusion DetectionIn most network-deployment scenarios, a layered intrusion-detection approach is required to provide protection against all forms of attack. Through user training, host-based and network-based IDS solutions, and the hardening of services and systems to exclude known vulnerabilities, a unified solution to many developing security requirements can be formed . Honeypots and HoneynetsHoneypots are systems configured to simulate one or more services within an organization's network, and they are intentionally left exposed to network access as a means to attract would-be attackers . For instance, a honeypot can be used to identify the level of aggressive attention directed at a network should an administrator suspect an attack or potential attack. Honeypots are also used to study and learn from an attacker's common methods of attack. When an attacker accesses a honeypot system, her activities are logged and monitored by other processes so that the attacker's actions and methods may be later reviewed in detail. The honeypot system also serves to distract the attacker from valid network resources. This is important information that is used for legal action as well as to gain knowledge of method attacks that can be used in later attack situations. Honeynets are collections of honeypot systems interconnected to create functional-appearing networks that may be used to study an attacker's behavior within the network. Honeynets use specialized software agents that create normal-seeming network traffic. Honeynets and honeypots can be used to distract attackers from valid network content, to study the attacker's methods, and to provide an early warning of attack attempts that may later be waged against the more secured portions of the network. See www.honeynet.org for more information.
Incident HandlingWhen IDS solutions alert responsible parties of a successful or ongoing attack attempt, it is important to have previously documented plans for responding to incidents. Several forms of response can be derived from the analysis and identification of attack attempts, including the following:
Post-attack analysis of successful intrusions should be used to harden systems against further intrusion attempts that use the same methodology. Via honeypot systems, planning can be used to configure access restrictions as well as modify the network to make it appear less desirable to potential attackers. |
EAN: 2147483647
Pages: 162