Chapter 8: Checking Out Security Distros
One of the great things about Knoppix is that it's a general-purpose distro. You can do a gazillion different things with it, and that's one of its strengths. However, there's also something to be said for specialization, and the distros in this chapter are single-minded about one thing: security. Each of these distros focuses solely on security, but that doesn't mean they're all the same. Granted, there is a lot of overlap here (each distro has Nmap and SSH, for instance), but each distro also has a different focus and a unique set of tools.
In the same way that Knoppix is free, making it worth your while to try out, each of these distros is free for the download. Grab ‘em, burn ‘em, and boot ‘em — you have no excuse!
Inspecting Auditor
When you first boot Auditor, you're going to be blown away by the amazingly well-structured K menu. The folks behind Auditor have done a simply incredible job organizing the various tools they provide so that everything is easy to find and presented in a logical fashion. Figure 8-1 shows an example of Auditor menus.
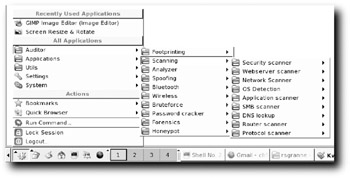
Figure 8-1: Now that is good menuing!
As you can see, everything is broken down into the major tasks you'd want in a distro focused on security checking, which is Auditor's goal. It wants to be the Live CD you use when you need to check out a network or machine to figure out what's going on. In particular, it has a lot of good scanning tools, especially wireless scanning tools, and 64 million entries in word lists that you can use for brute-force password cracking. Best of all, the main developer — a guy named Max Moser — seems to work hard to keep Auditor up-to-date, with regular changes and tweaks. He details his progress at http://new.remote-exploit.org/index.php/Auditor_devlog. Bookmark that page and view it often to see what's new and different.
| Note | If you find that you like Auditor and want to help the developers out, you can give them money by visiting their Website and clicking the Make a Donation button. |
To acquire Auditor, head over to the project's home page, http://new.remoteexploit.org/index.php/Auditor_main; scroll down to the Downloads section; and click the link for the list of download mirrors. Download the zipped ISO (about 525MB) from one of the sites, unzip it, burn the ISO, boot with it, and you're ready to go.
Following are three tips that will come in handy when you start to use the feature-packed Auditor distro:
-
How to not run Konsole as root: When you open a terminal in Auditor, it always opens as root. Generally this is fine with Auditor because most of the useful command-line tools you need should be run as root anyway. However, if you mount your local drive to write data to it, you may want to take safeguards. To become a nonroot user in Konsole, just type su knoppix and press Enter. You're now running without root privileges; to become root again, enter exit and press Enter.
-
Why won't your wireless card work? If you want to get online wirelessly, and especially if you want to use the cool wireless security tools that Auditor provides, you're going to need a supported wireless card. Auditor supplies a list of recommended wireless cards (both WiFi and Bluetooth) at http://new.remote-exploit.org/index.php/Auditor_FAQ; a longer list of devices known to work, including laptops, USB wireless adapters, PCMCIA wireless adapters, mini-PCI wireless cards (the ubiquitous Intel Centrino falls into this category), Bluetooth adapters, and even GPS devices can be found at http://new.remote-exploit.org/index.php/Auditor_dev_list1.
-
So that you don't go crazy … If you want to view the files on your system using a GUI, don't bother selecting the Home icon on the panel because it doesn't work. This should be fixed, it is hoped by the time you're reading this book, but if it isn't, here's what to do: Instead of the Home icon, select the Konqueror icon, and then click the Home icon on the toolbar. Bang! Konqueror goes into file manager mode, and you can browse your files.
There are many, many tools on the Auditor distro, so you really must play with it at length, spending some time trying out all the myriad software options. The following sections describe a few of those tools, just to whet your appetite.
Scanning Your Web Servers with Nikto
Nowadays it seems like everyone is running a Website; unfortunately, it also seems like another Website gets broken into and defaced just about every day. It's important to try to prevent embarrassing and potentially dangerous Website hacks, and Nikto helps do the job. Nikto is a constantly updated open-source tool that, as its Website describes, tests for "over 3,200 potentially dangerous files/CGIs, versions on over 625 servers, and version-specific problems on over 230 servers." Run it against your Web server, and you may just find holes about which you knew nothing.
| Caution | Do not run Nikto against any ol' server that you feel like scanning because you could be the subject of an unpleasant visit from the authorities. Instead, confine it to Websites and servers that are under your control. When in doubt, ask first. |
To start Nikto, from the K menu select Auditor → Scanning → Webserver scanning → Nikto. Konsole opens, and the various options available for Nikto appear. Take a look through them if you're interested, but to get started, just enter the following in the terminal, substituting your Website's domain name for http://www.webserver.com.
# nikto -h http://www.webserver.com
I used a Lucent Orinoco Gold (yes, I know it's ancient, but it's my Old Faithful because it works with virtually any Linux distro), and although Auditor saw the card, I didn't get an IP address automatically. I first ran ifconfig to find out which device Auditor thought my Orinoco was. Once I saw that it was eth0, I ran pump -i eth0 to ask my router to assign the card an IP address using DHCP. After another ifconfig command to ensure that yes, I was now 192.168.0.102, I was ready to go. If you can't get online with your wireless card, and you know that Auditor supports it, try that sequence of commands and see whether that fixes your problem.
Be patient as you let Nikto do its work. It'll take some time, but you eventually get some interesting results. For instance, here's what came back from one scanned Web:
- Nikto 1.32/1.23 - www.cirt.net + Target IP: [IP address redacted] + Target Hostname: [Domain name redacted] + Target Port: 80 + Start Time: Fri Apr 28 04:52:05 2005 ---------------------------------------------------------------------- - Scan is dependent on "Server" string which can be faked, use -g to override + Server: Apache/1.3.33 (Darwin) PHP/5.0.1 mod_ssl/2.8.22 OpenSSL/0.9.7b + /robots.txt - contains 7 'disallow' (added to mutation filelists) (GET). + Allowed HTTP Methods: GET, HEAD, POST, PUT, DELETE, CONNECT, OPTIONS, PATCH, PROPFIND, PROPPATCH, MKCOL, COPY, MOVE, LOCK, UNLOCK, TRACE + HTTP method 'PUT' method may allow + HTTP method 'CONNECT' may allow server + HTTP method 'DELETE' may allow clients + HTTP method 'PROPFIND' may indicate to get directory listings if indexing is allowed but a default page exists. + HTTP method 'PROPPATCH' may indicate + HTTP method 'TRACE' is typically only disabled. + Apache/1.3.33 appears to be outdated (current is at least Apache/2.0.47). Apache 1.3.28 is still maintained and considered secure. + OpenSSL/0.9.7b appears to be outdated (current is at least 0.9.7c) (may depend on server version) + 2.8.22 OpenSSL/0.9.7b - TelCondex Simpleserver 2.13.31027 Build 3289 and below allow directory traversal with '/.../' + mod_ssl/2.8.2 - mod_ssl 2.8.7 and lower are vulnerable to a remote buffer overflow which may allow a remote shell (difficult to exploit). CAN-2002-0082. + /~root - Enumeration of users is possible by requesting ~username (responds with Forbidden for realusers, not found for non-existent users) (GET).
There's a lot more than this. Consider it just a taste of all the great info you can get with nikto. For more pointers on using Nikto, be sure to read man nikto and visit the project's home page at http://cirt.net/code/nikto.shtml.
This story really happened, and it explains just how you can use various tools that come with Auditor to sniff packets on a wireless network, potentially to devastating consequences. I was at my buddy Ben's house, using his wireless network and writing the portion of this chapter about Auditor. Ben and his fiancée were talking in his office and looking at Ben's computer screen. Ben's machine was also wirelessly connected to the Net.
From the dining room, I asked, "Hey, Ben! Mind if I eavesdrop on what you're doing for my book?" He gave his assent, and so I started by firing up Mailsnarf, part of the excellent dsniff package, opening the K menu, and selecting Auditor → Analyzer → Applications → Mailsnarf. A Konsole window opened, and in it I typed the following command:
# mailsnarf -i eth0 . "tcp"
I used eth0 with the -i (interface) because I knew that Auditor had assigned that device ID to my wireless card by running the ifconfig command. "tcp" tells dsniff what kind of traffic to sniff, using the same terminology that tcpdump and ethereal use. Finally, the . (period) in the command looks for all emails going by; if I wanted to limit Mailsnarf's activity to certain emails, I could use a search word or phase instead, like this:
# mailsnarf -i eth0 password "tcp"
After a few minutes, the following email popped up in Konsole (I redacted the domain names for privacy's sake):
From mailsnarf Sat Apr 30 00:40:41 2005 Return-Path: <Jans@DOMAIN.com> Delivered-To: jans-DOMAIN:com-Ben@DOMAIN.com X-Envelope-To: ben@DOMAIN.com Received: (qmail 6440 invoked from network); 30 Apr 2005 00:39:19 -0000 Received: from relay03.pair.com (209.68.5.17) by chanas.pair.com with SMTP; 30 Apr 2005 00:39:19 -0000 Received: (qmail 91563 invoked from network); 30 Apr 2005 00:39:18 - 0000 Received: from unknown (HELO ?192.168.1.3?) (unknown) by unknown with SMTP; 30 Apr 2005 00:39:18 -0000 X-pair-Authenticated: 69.155.165.22 Mime-Version: 1.0 (Apple Message framework v622) Content-Transfer-Encoding: 7bit Message-Id: <79fa9de385e470b11d6f0d585d388caf@DOMAIN.com> Content-Type: text/plain; charset=US-ASCII; format=flowed To: Ben Jones <Ben@DOMAIN.com> From: Jans Carton <Jans@DOMAIN.com> Subject: Wedding plans Date: Fri, 29 Apr 2005 19:39:17 -0500 X-Mailer: Apple Mail (2.622) Ben, I forgot when your wedding is (sorry!) Can you tell me the date again? Thanks. Jans
Well, that explained what Ben and his fiancée were doing on Ben's computer: looking at wedding stuff. I thought I'd use URLsnarf to see what Websites they were checking out. I opened the K menu and selected Auditor → Analyzer → Applications → URLsnarf. Another Konsole window opened, and I entered the following command:
# urlsnarf -i eth0 . tcp
In a few seconds, the URLs accessed by my friends began to stream by, including the following:
192.168.1.107 - - [30/Apr/2005:00:07:12 -0400] "GET http://www.modestapparelchristianclothinglydiaofpurpledressescustom sewing.com/wedding_dresses_topaz_backview.jpg HTTP/1.1" - - "http://www.modestapparelchristianclothinglydiaofpurpledressescustom sewing.com/wedding_dresses.htm" "Mozilla/5.0 (Windows; U; Windows NT 5.1; en-US; rv:1.7.7) Gecko/20050414 Firefox/1.0.3" 192.168.1.107 - - [30/Apr/2005:00:07:12 -0400] "GET http://www.modestapparelchristianclothinglydiaofpurpledressescustom sewing.com/wedding_dresses_melissa.jpg HTTP/1.1" - - "http://www.modestapparelchristianclothinglydiaofpurpledressescustom sewing.com/wedding_dresses.htm" "Mozilla/5.0 (Windows; U; WindowsNT 5.1; en-US; rv:1.7.7) Gecko/20050414 Firefox/1.0.3" 192.168.1.107 - - [30/Apr/2005:00:07:12 -0400] "GET http://www.modestapparelchristianclothinglydiaofpurpledressescustom sewing.com/wedding_dresses_melissa_small.jpg HTTP/1.1" - - "http://www.modestapparelchristianclothinglydiaofpurpledressescustom sewing.com/wedding_dresses.htm" "Mozilla/5.0 (Windows; U; Windows NT 5.1; en-US; rv:1.7.7) Gecko/20050414 Firefox/1.0.3" 192.168.1.107 - - [30/Apr/2005:00:07:12 -0400] "GET http://www.modestapparelchristianclothinglydiaofpurpledressescustomsewi ng.com/favicon.ico HTTP/1.1" - - "-" "Mozilla/5.0 (Windows; U; Windows NT 5.1; en-US; rv:1.7.7) Gecko/20050414 Firefox/1.0.3"
Now, before you ask, the engaged couple were not intending to head to the Website with the longest URL I've ever seen — http://www.modestapparelchristianclothinglydiaofpurpledressescustomsewing.com — but instead stumbled across it after a Google search. They found the site interesting, and began to surf around. I heard them exclaim at several of the dresses they saw, so I thought I'd view just what was inspiring their noise. I fired up Driftnet by opening the K menu and selecting Auditor → Analyzer → Applications → Driftnet. A command-line window opened, and I entered the following:
# driftnet -i eth0
Another window opened, and in it began to shoot by the images Ben and his fiancée were seeing on his computer, as the following figure shows.
Driftnet in action, showing a variety of wedding dresses.
Driftnet's display window doesn't include a scrollbar, so if a picture zooms past, you can't scroll up to see it. Fortunately, Driftnet wants to save the pictures that it captures, in addition to displaying them to you, but there's a problem: The default directory you're in when the Driftnet Konsole window opens is /root, which is actually in your RAM and will fill up quickly. If you really want to save the images Driftnet sees, tell the program to use another directory (on your hard drive or a USB flash drive) by using the following command:
# driftnet -i eth0 -d /mnt/hda2/driftnet_pix
I quietly left Ben and Tracy at the computer, happily planning their wedding. (Congratulations, you two!)
Remember, Ben and Tracy knew that I was watching them the whole time, so this little story isn't as creepy as it might seem. They actually found it kind of funny yet worrisome that their wireless Internet access was so wide open. Your average wireless coffeehouse is just as wide open, and virtually none of the patrons realizes it.
| Note | To learn more about Mailsnarf, try man mailsnarf; for URLsnarf, try — you guessed it! — man urlsnarf. Both tools are part of the dsniff suite, and a visit to the dsniff home page provides a bit more info, but not much: http://monkey.org/~dugsong/dsniff. A longer look at dsniff can be found at http://ouah.org/dsniffintr.htm. Definitely look into dsniff — I only covered a fraction of what it ca |
For more on Driftnet, a separate tool from dsniff, use man driftnet or driftnet -h, and be sure to visit the home page, at http://ex-parrot.com/~chris/driftnet/.
Detecting and Sniffing Wireless Networks with Kismet
Ever wonder how you could discover a wireless network? Enter Kismet.
To start Kismet, open the K menu and select Auditor → Wireless → Scanner/Analyzer → Kismet tools → GKismet (gkismet is a GTK GUI for Kismet). Choose a data directory, in which Kismet will store the packet database it's going to create. Select a folder on your hard drive if you can (make sure you can write to it), or point at a mounted USB flash drive. When you're asked about a file prefix, leave the default in place and click OK.
Gkismet opens, and it immediately detects any wireless networks in the area. Figure 8-2 shows quite a few — the gkismet user is probably near an apartment building.
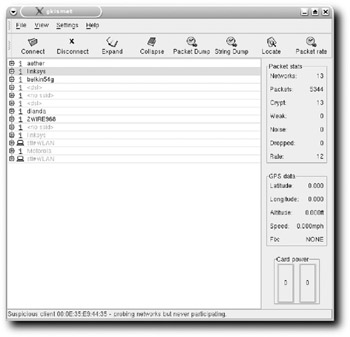
Figure 8-2: Gkismet has found quite a number of wireless networks near me.
Kismet is such a rich tool that it could easily be the subject of its own book. The Locate button, for example, actually maps the physical location of each Wireless Access Point (WAP) it discovers, if you have a working GPS device installed. This capability obviously makes Kismet perfect for wardriving.
Expand one of the nodes (see Figure 8-3), and you find a wealth of detail about that WAP.
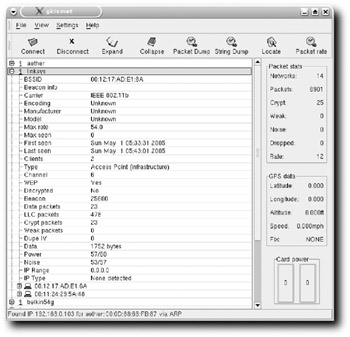
Figure 8-3: You can find out a lot about a Wireless Access Point using Kismet.
There is an almost infinite list of things you can do with Kismet. It's one of those tools that you really need to learn how to use if you want to become a wireless security master. One of the coolest things about Auditor is that is makes it easy to start learning how to use this wonderfully powerful software.
| Note | Kismetapos;s Website (http://kismetwireless.net/) is a gold mine of useful information about this software. If you have any questions about Kismet, start there. Of course, man kismet doesn't hur |
| Tip | Auditor is unique among the distros examined in this chapter in that it has been reviewed, and many of those reviews contain interesting and useful tidbits of information. In particular, read "Product Review: Moser Informatik Auditor Security Collection (Auditor)" at http://www.tomsnetworking.com/Reviews-154-ProdID-AUDITOR.php, WindowsITPro's "The Auditor Security Collection," at http://windowsitpro.com/Windows/Articles/ArticleID/44648/pg/1/1.html, and TheSecure.Net blog, which has posts discussing Auditor at http://thesecure.net/blog/archives/2004_05.html (be sure to scroll down and read all the posts about Auditor and some of the other Live CDs discussed in this chapter). And here's a final tip: I didn't have space here, but if you start playing with Auditor, make sure you check out hotspotter. |
EAN: 2147483647
Pages: 118