Exploring SSH and Its Descendants
As discussed earlier, FTP is insecure because it doesn't protect your traffic during authentication or transmission of data. The same problem is inherent in Telnet, which is used to log in to other machines and run commands. First described in RFC 854 in May 1983 (and still available at http://www.ietf.org/rfc/rfc854.txt), Telnet is another of those protocols that were never built with security in mind. My advice? Never use Telnet. Avoid it completely, because it is simply too dangerous and unsafe. Instead, use SSH.
SSH (secure shell) was first written by Tatu Ylönen of Finland in 1995 as a replacement for Telnet (as well as rlogin and rsh, two other incredibly insecure programs), although the version you're now using with Knoppix is quite separate from Ylönen's now proprietary implementation. SSH is really an amazing program, one that should be a centerpiece of your Knoppix toolkit. With SSH, you can connect to other machines and run commands, transfer files securely, and much more. It's one of those programs about which you can always learn something new.
Ensuring SSH Is On for Secure Connections
In order for you or others to connect to your Knoppix machine via SSH, you need to enable the SSH daemon. Klaus and the other Knoppix developers have made this drop-dead simple: Just open the Knoppix menu and select Services → Start SSH Server. You'll be prompted to assign a password to the user knoppix, so go ahead and enter a good one (you won't see what you're typing as a security measure). After Knoppix accepts your password, press Enter to close the window. The SSH daemon is now running and capable of accepting logins from the user knoppix.
To enable new SSH users, simply add new system users using the adduser command on the command line, or with KUser, available at K → System → KUser. Enter the root password (from the Knoppix menu select Root Shell, enter passwd, and then type a new password for root), go to User → Add, and give your new user access. Once someone is a system user, she can SSH into your computer and get to work.
Using SSH
To SSH into another box, just open up Konsole (the Terminal Program icon on the panel), type ssh username@machine , and press Enter. For example, if I were user scott on machine http://work.wiley.com, you could enter sshscott@work.wiley.com. SSH prompts you for a password; type it in, press Enter, and you're in.
If you don't know how to use the command line, you're pretty much stuck at this point. On the other hand, if you know how to navigate using cd and related commands, and how to run programs and work with data using terminal-based editors such as vi, this is your playground.
Using SFTP
If you have to transfer files back and forth, use SFTP instead of FTP, for no other reason than security. Unlike FTP, which sends your name, password, and all data in the clear so that anyone grabbing traffic (which is discussed in Chapter 6) can listen in, SFTP travels over SSH to encrypt everything, which is what you want.
You can use SFTP on the command line if you'd like. If you know your command-line FTP commands, you'll be right at home, because virtually everything is the same. To connect using the command line, just type sftp username@machine in Konsole and press Enter (using the example from the preceding section, you'd enter sftp scott@work.wiley.com). Put in a password when you're prompted, and you're ready to go. If you need to brush up on the commands you can use, try entering help and take a gander at the resulting list.
If you'd prefer to use a GUI — which can definitely be easier in many situations — then you're back to your good friend Konqueror, which does SFTP as well as FTP. Everything is exactly the same, except that you use sftp:// instead of ftp:// in the Location bar. This does not mean that you can just change the ftp to sftp for any old site and have things work. In fact, that fails the vast majority of the time because most servers that use FTP do not necessarily use SFTP.
So how would you use Konqueror to connect to a server that supports SFTP? Open Konqueror, put your server's address (something like sftp://work.sftpserver.com) in the Location bar, and press Enter. You should next see a warning dialog similar to the one shown in Figure 3-4.
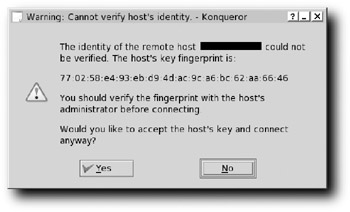 Figure 3-4: You have to accept a machine's key the first time you connect to it.
Figure 3-4: You have to accept a machine's key the first time you connect to it.
Remember that all traffic sent over SSH is encrypted. To make the encryption possible, keys are exchanged between your computer and the server to which you're connecting. This warning is SSH's way of telling you that it has no way of knowing if the server's key is valid, so it's asking you to validate the key for it. If you know that the key is valid — if, in other words, you're positive that you're not the victim of a man-in-the-middle attack — go ahead and click Yes to add the key to the list found at ~/.ssh/known_hosts (if the key changes on the server because the OS is reinstalled, for instance, you'll need to find the appropriate line in known_hosts, delete it, and reconnect to the server to re-accept and re-enter the key).
After the key is added, you're prompted for a username and password. Go ahead and enter it, and a few seconds later you should see the contents of the SFTP server.
| Note | Want to know more about man-in-the-middle attacks? Check out Wikipedia's article on the subject, at http://en.wikipedia.org/wiki/Man_in_the_middle_attack. |
Download and upload files with SFTP in the same way you do so with FTP: just drag and drop, or right-click and choose Copy To. If this is an SFTP site you plan to use several times while you're running Knoppix, go ahead and bookmark it for easy access later.
Be safe: Whenever you have a choice, use SFTP instead of FTP.
| Note | I use SFTP even at home on my own internal network, partly because I'm paranoid, and partly because I'm so used it now that it's just automatic. It's a good idea to develop the same habit. |
Using SCP
If you're a command-line junkie and you're in a hurry, SCP (secure copy) is a great way to quickly copy a file from one machine to another using SSH. SCP basically follows this pattern: scp user@host1:file1 user@host2:file2. You can leave out the user@host,however, if one of the files you're working with is local, as you'll see in a moment.
For example, suppose you want to use scp to copy me.jpg from the directory you're currently in to your Website on another machine (called work.wiley.com). Type the following on the command line and press Enter:
$ scp me.jpg username@work.wiley.com:/var/www/mywebsite/images
You'll be prompted for a password, and, a moment later, me.jpg will be available on your Website for viewers around the world.
You've got several JPEGs you want to transfer? Simple!
$ scp *.jpg username@work.wiley.com:/var/www/mywebsite/images
To copy all the JPEGs on your server to your current machine, but to a different directory than your current one, type this:
$ scp username@work.wily.com:/var/www/mywebsite/images ~/pix/website
scp can come in quite handy when you want to securely copy files between machines. However, it gets tiresome having to type scp commands if you have a lot of different things to move around. When that happens, you may want to use SFTP, or turn to protocols such as SMB or NFS.
| Note | Only the basics of SCP are covered here. To learn more, man scp is quite helpful, or search Google for "scp tutorial." |
EAN: 2147483647
Pages: 118