Section 5.2. Building an Active Directory Structure
5.2. Building an Active Directory StructureTo get the best foundation for the rest of this chapter, much as we did in Chapter 4, let's actually build an Active Directory forest, tree, and domain. In this section, I'll walk through the process of creating a domain, promoting a domain controller, adding another domain controller to the domain, adding a second child domain, and then adding a few users and groups to the mix. 5.2.1. The First DomainThe first domain in an Active Directory setup is special for a few reasons. For one, the setup process for a new domain automatically adds the first domain controller to that domainthe machine on which you run the Active Directory Wizard becomes the first domain controller for the new domain. Second, this new domain becomes the root of the entire forest, meaning it has special powers over other domains you create within the forest, even if their names aren't the same. We'll go over that in a bit. To start the process, from the machine you want to become the first domain controller for the new domain, select Run from the Start menu, type DCPROMO, and click OK. The Active Directory Installation Wizard starts, as shown in Figure 5-2. Figure 5-2. Beginning Active Directory installation Click Next to continue and you'll see the Operating System Compatibility screen. This screen is simply informing you that Windows 95 clients and Windows NT clients running Service Pack 3 or earlier, by default, will be effectively locked out of participating in the domain and using resources within Active Directory. This is because of more stringent communications requirements in Windows Server 2003clients must electronically "sign" their transmissions to the server to make sure those transmissions aren't intercepted and modified on their way to the serverand Windows 95 doesn't have logic to perform this signing process. You can choose to relax these requirements later, but I don't recommend that. (It's 2006. It's definitely time to move to at least Windows 98, which can sign its communications with the Active Directory Client software.) Click Next to continue. The Domain Controller Type screen appears, as shown in Figure 5-3. Figure 5-3. Selecting a new domain controller installation You can create a new forest, a new domain tree, or a new domain by selecting the first option: Domain controller for a new domain. Select the second option to simply promote the current machine to domain controller status within an existing domain, something I'll walk through in just a bit. Click Next. The Create New Domain screen appears, as shown in Figure 5-4. Here, you can create a brand-new domain with the first option, a new child domain for an existing domain tree (such as main.jonathanhassell.com under an existing jonathanhassell.com domain), or a completely separate domain tree that is not a child to any other domain but that is located within the same forest. For this demonstration, select the first option, and click Next. The New Domain Name screen appears, as shown in Figure 5-5. On this screen, type the full DNS canonical name of the domain you're creating . In this example, I'll use the domain for the web site of this book, learning2003.com, as shown in the figure. Enter the name, and click Next to continue. The NetBIOS Domain Name screen appears. This is shown in Figure 5-6. Figure 5-4. Creating a new domain Figure 5-5. The New Domain Name screen The NetBIOS name allows down-level compatibility with Windows NT and Windows 9x clients. NetBIOS names are restricted to 15 characters or fewer and should consist of letters and integers only. The Active Directory Wizard selects a NetBIOS name from the full DNS name you selected in the previous step, simply taking the leftmost part of the name. You can change this if you want. This name is what your users will see when they are logging on to their machines, if they have chosen to look at the advanced options in the logon dialog box. Figure 5-6. Choosing a NetBIOS name
Click Next once you've chosen a NetBIOS name. The Database and Log Folders screen appears, prompting you to choose where you want the Active Directory database (recall that this is the NTDS.DIT file on all domain controllers' hard drives) and where you want the transaction log that keeps track of changes to the directory. This is shown in Figure 5-7. If possible, place the database on one drive and the log file on another drive. This ensures the best performance in production environments. You can use the Browse buttons to choose a location on the physical filesystem, or you can simply type a path into the boxes. Once you've finished choosing a location, click Next to continue. The Shared System Volume screen appears, as shown in Figure 5-8. The SYSVOL share is akin to NT 4.0-style NETLOGON shares, in that the contents of the share are replicated automatically to all domain controllers within a domain. SYSVOL contains user logon scripts, system policy files, default profiles, and other configuration-related files. The SYSVOL location must be on an NTFS volume. You can use the Browse button to choose a path, or you can type in a path. Click Next to continue. DNS health checks and configuration are next. If your DNS servers aren't fully healthy, you'll receive a screen such as that shown in Figure 5-9. Figure 5-7. Choosing a location for database and log files Figure 5-8. Choosing a location for the SYSVOL share Here, Active Directory is complaining that it can't contact DNS servers. If you encounter this screen, it's almost certainly because of one of the following problems: either (a) the DNS servers can't be found because they're unavailable or your current machine is not on the network; or (b) the DNS servers that were found during the check don't support dynamic updates. For more information on taking care of either of those problems, consult Chapter 4, which explains DNS in detail with an eye to Active Directory. Figure 5-9. A DNS system health check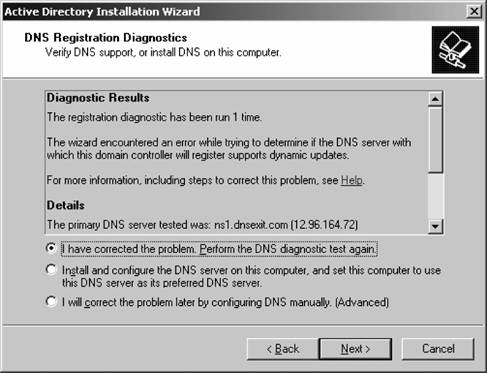 You have three options at this point: you can rerun the test if you've identified your specific problem and want to retest; you can instruct Active Directory to go ahead and install the DNS service on this computer, configure it correctly, and change this computer's LAN connection properties so that it points to itself for DNS services; or you can tell Active Directory, "To hell with DNS! Go ahead!" and proceed without having verified that DNS is installed and accessible. Let me offer a caution: do not use the second or third options. Take the time, armed with the information you learned in Chapter 4, to get DNS right before using DCPROMO to create a domain. You'll save yourself a lot of heartache, hassle, and time by ensuring DNS is as hard as a rock ahead of time. Why? For a few reasons. For one, your organization can often benefit from a solid DNS system even before Active Directory is rolled out. Second, Active Directory DNS systems can interfere with another DNS system you might have in place, and letting the wizard handle this part isn't smartyou need to evaluate your current environment and integrate DNS first before introducing Active Directory to the mix. Also, a solid, functionally efficient DNS system makes deploying additional domain controllers and creating new trees very efficient, as Active Directory "piggybacks" a lot of its internal functionality onto the DNS structure. Why would you want to trust to a wizard a system that is that fundamental to Active Directory? At any rate, once you're satisfied with your DNS structure and you want to proceed with the remainder of the Active Directory installation, click Next. The Permissions screen will appear, as seen in Figure 5-10. Figure 5-10. Determining default Active Directory client permissions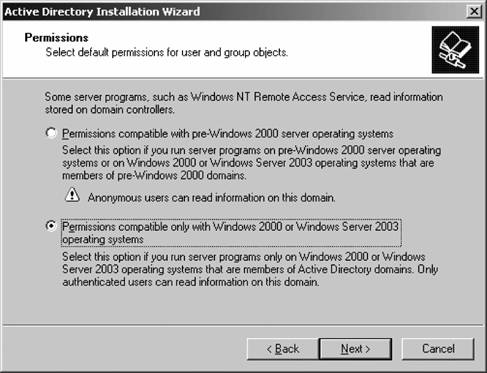 On this screen, you can choose the default permissions for new objects to either allow anonymous access for the purpose of reading information stored on a domain controller, or deny that access. As the screen says, the main culprit behind this choice is the Remote Access Service in NT. To make a long story short, for an NT-based RAS server (which could be only a member server) to figure out if an account has permission to dial into the network, it has to query a domain controller about the properties of the account. But because this hypothetical RAS server is only a member server, it doesn't have the necessary permissions to just ask about user properties that a domain controller does, so it needs another "back door" into the domain controller to find out about this permission. Hence, the ability to anonymously access a few details about user accounts on an NT domain controller. Of course, these days, this is a huge security hole, so please upgrade your NT RAS servers as soon as possible.
Make the appropriate choice, and then click Next. The Directory Services Restore Mode Administrator Password screen appears. This is shown in Figure 5-11. Figure 5-11. Setting the directory restore mode password On this screen you can choose the password that will be required of anyone attempting to access the Active Directory restore mode tools before Windows boots. Set this password to something that is secure and different from all your other administrator passwords, and then lock it away in a safe place. You probably won't need it very often. Once you've set the password, click Next.
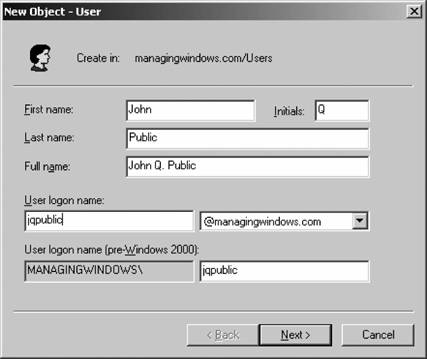
The Summary screen appears, as displayed in Figure 5-12. Figure 5-12. Summarizing Active Directory installation choices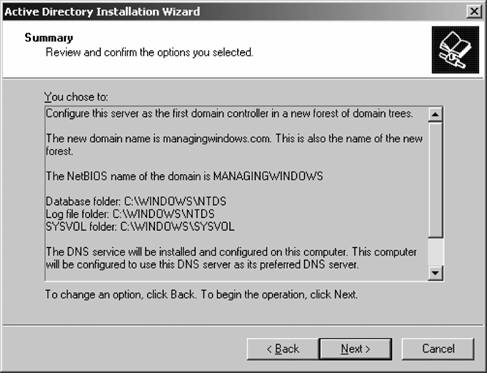 Ensure the choices you selected are the correct ones you wanted, and then click Next to begin the procedure to install Active Directory and promote the current machine to a domain controller within your new domain. The installation process will trundle along, until you receive the success notification pictured in Figure 5-13. Congratulations! You've built a new domain and promoted your machine to a domain controller. You'll need to restart your machine to continue. Figure 5-13. Successful Active Directory installation 5.2.2. Using Active Directory ToolsBefore we go any further, I'd like to discuss the three most common tools you will find yourself using as an Active Directory administrator. The first of these tools is Active Directory Users and Computers, the tool that allows you to create your Active Directory structure within a domain, add users and groups, adjust account properties, and generally administer the day-to-day operations of your directory. Figure 5-14 shows the default screen for Active Directory Users and Computers. Next, there's Active Directory Domains and Trusts , a utility you can use to create trusts between domains and to eventually raise the domain functional level to enable new features for Active Directory. Figure 5-15 shows the default screen for Active Directory Domains and Trusts. Finally, let's briefly glance at Active Directory Sites and Services , a graphical tool that allows you to design your Active Directory structure around how your business is geographically dispersed, making Active Directory replication traffic go across links that cost the least and are the fastest. You also can delineate how your organization's computers are addressed via outlining different subnets, thereby increasing the likelihood that clients will log on to domain controllers that are the closest distance to them. Figure 5-16 shows the default screen for Active Directory Sites and Services. We'll use each tool in time as we proceed through the remainder of this chapter. For now, let's move on. Figure 5-14. Active Directory Users and Computers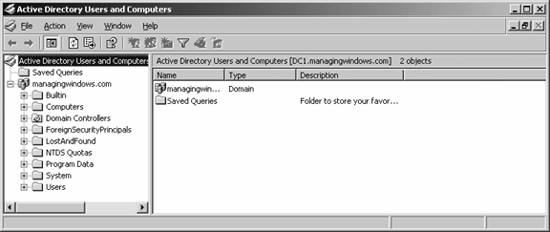 Figure 5-15. Active Directory Domains and Trusts Figure 5-16. Active Directory Sites and Services 5.2.3. Adding Another Domain Controller to a DomainPromoting another machine to domain controller status within an existing domain is even easier than promoting the first machine in a new domain. You can use the DCPROMO Wizard to do the job for you in this case, as well. To begin, start DCPROMO as before, and on the screen asking you what action you want to perform, select Additional domain controller for an existing domain, and click Next. The Network Credentials screen will appear, asking you to type in the username and password for a domain administrator account. Do so, and then click Next. Enter the full DNS canonical name of the domain for which you want this machine to become a domain controller, and then click Next. From there, proceed through the wizard starting from the Database and Log Files screen as indicated in the previous section. Once the wizard is finished and your machine has restarted, it is an official domain controller for your domain. 5.2.4. Adding Another DomainAdding a child domain is equally simple: you use DCPROMO and you tell it to create a new domain, but not a new tree. This will add a "subdomain" to the existing domain tree. Then the Network Credentials screen will appear, asking for a domain administrator account. After that, the Child Domain Installation screen will appear, as shown in Figure 5-17. Here, you can select to install a domain controller into a new domain. Click Next, and then you will be prompted to provide a name for the domain, as shown in Figure 5-18. Next, you need to tell Active Directory which domain you want to add on to, and then the name of the child domain to add on to the parent tree. You can use the Browse button to scroll around the directory or simply type the name in. In the second box, enter just the first portion of the new child domain's name. The box at the bottom will adjust automatically to show the full name of the new child domain. Now you can proceed through the wizard, as shown in the previous section. One note of interest, though: if the domain has a lot of information to replicate out to its new domain controller, this promotion process can take a long time. An option is available on the final screen of this wizard that allows you to finish replication later, and you might be tempted to take advantage of this option. Although it does decrease the amount of time it takes to bring a new domain controller in an existing domain online, I prefer to let replication happen immediately. The only instance in which I wouldn't want to do this is if I were bringing up a new domain controller in a branch office with a very slow connection to the home office. In that case, it's OK to wait until off hours and let the replication happen then. In all other cases, I recommend moving ahead with replication and simply waiting it out. Figure 5-17. Selecting to install a domain controller into a new domain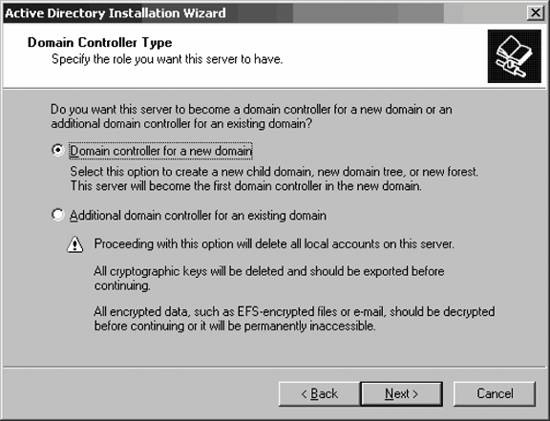 5.2.5. Managing Users and GroupsOf course, critical to a multiuser system are user accounts and groups, which you can create within Active Directory using the Active Directory Users and Computers tool, which we previewed two sections ago. (In this section I'll use the acronym ADUC to refer to this tool to save me from having to type out "Active Directory Users and Computers" over and over.) Within ADUC, you can create, change, and delete user accounts, manage groups and their members, and configure Group Policiesthe latter being a topic I will save for Chapter 6. 5.2.5.1. Creating users and groupsLet's look at creating users and groups within ADUC. It's a simple process to create a user or a group. First, you ought to decide on a username or group name. You can select almost any username or group name for a particular person or group in Windows Server 2003, but you must keep the following restrictions in mind: Figure 5-18. Providing a name for the new child domain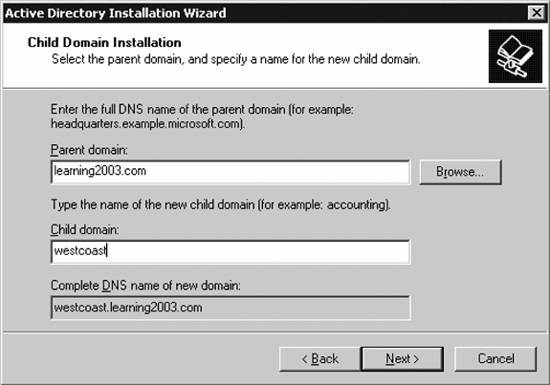
So, to create a user, follow these steps:
To create a new group, follow these steps:
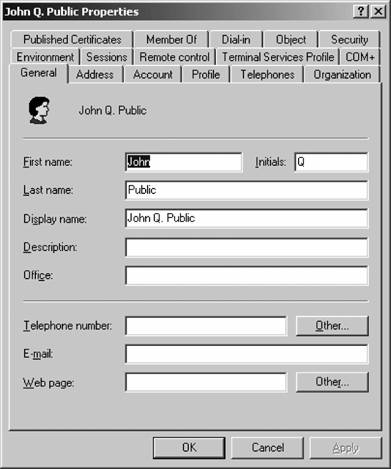
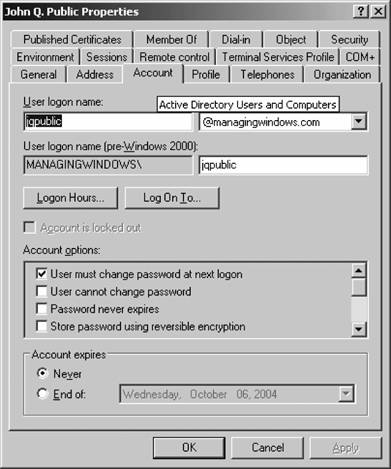
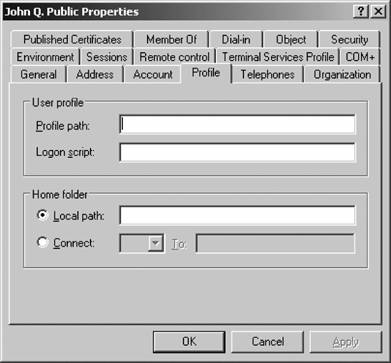
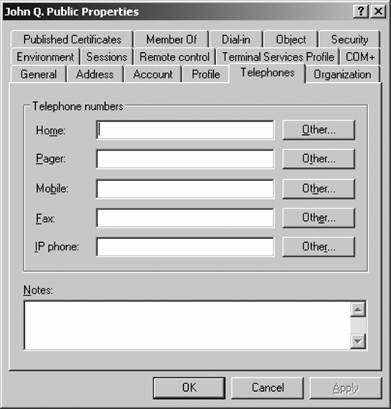
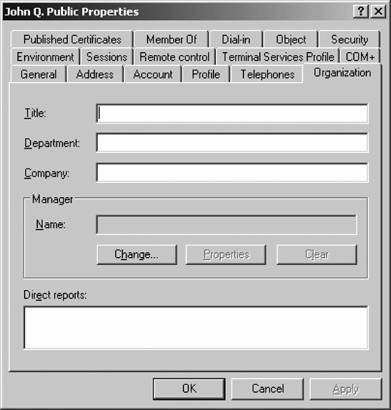
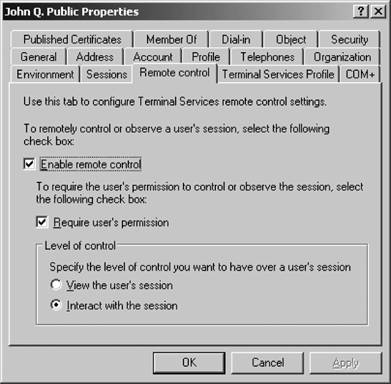
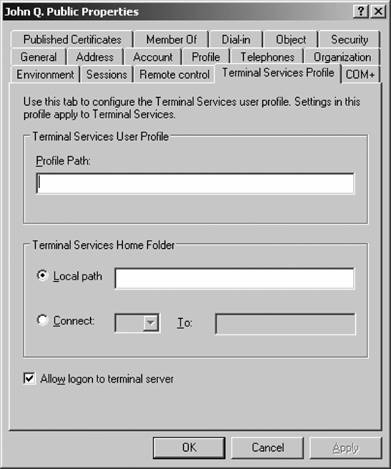
That's it! You've created a new group. Figure 5-20. Entering a new user's password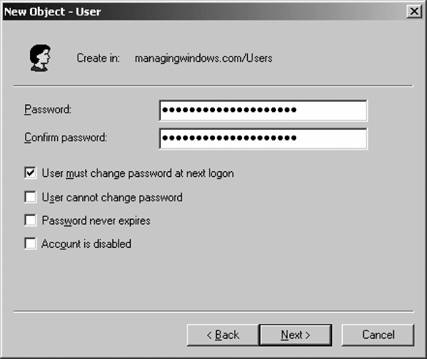 Figure 5-21. Creating a new group If you are creating a user, your work is not done yet. You need to configure several additional properties before the user account is ready for use. Right-click the new user within ADUC and select Properties from the context menu. Here's a rundown of each option on the properties sheet's various tabs:
5.2.5.2. Performing common administrative tasksYou can accomplish a couple of neat tricks using ADUC on multiple accounts at once, reducing some of the tedium involved in making repetitive changes. For one, you can select multiple accounts within ADUC by clicking one account and doing one of the following:
Figure 5-34. The Sessions tab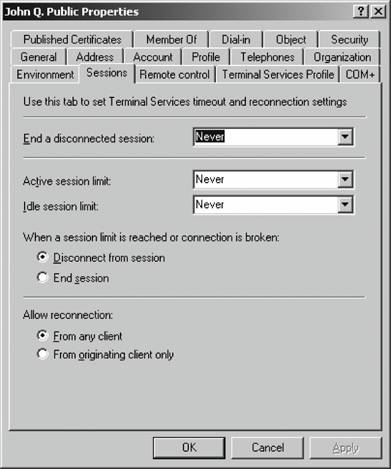 Then you can right-click the group of accounts and perform actions such as changing common properties or sending email. When you right-click multiple accounts and select Properties, the screen in Figure 5-38 appears. On this screen, you can make changes to multiple accounts at the same time. A subset of the options available on individual accounts is accessible, but such common tasks as changing the UPN suffix of an account, specifying that a user must change his or her password, or requiring a smart card for logon are easy to make with this screen. 5.2.5.3. Using LDAP to create usersLDAP is the foundation protocol for accessing and modifying the contents of Active Directory. You can use LDAP-style strings in conjunction with a couple of command-line tools to automate the creation of users and groups. First let's look at what makes an LDAP identifier. For instance, let's say my full name is Jonathan Hassell, and I'm in the container SBSUsers within the hasselltech.local domain. My LDAP name, therefore, is: Cn="Jonathan Hassell",cn=SBSUsers,dc=hasselltech,dc=local Figure 5-35. The General tab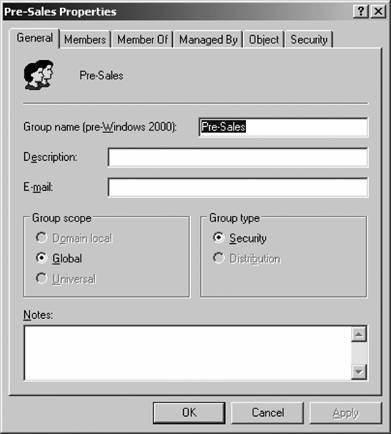 Figure 5-36. The Members tab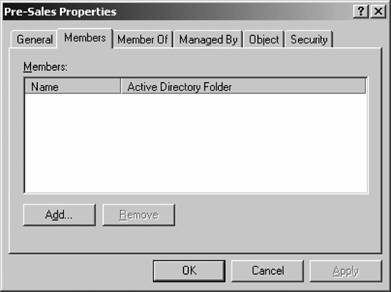 Figure 5-37. The Member Of tab Figure 5-38. Changing the properties of multiple accounts The abbreviation CN refers to the container, and DC refers to the components of a domain name. Likewise, Lisa Johnson in the Marketing container within the Charlotte container of enterprise.com would have an LDAP name of: Cn="Lisa Johnson",cn=Marketing,cn=Charlotte,dc=enterprise,dc=com Usernames in the directory are represented by a user principal name, or UPN. UPNs look like email addresses, and in some cases actually can be email addresses, but within the context of LDAP they serve to identify and select a specific user in the directory. So, if my username were jhassell, my UPN would be: jhassell@hasselltech.local And if Lisa Johnson's username were ljohnson, her UPN would be: ljohnson@hasselltech.local Now that we know how to specify some properties in LDAP, we can use the DSADD utility to create users from the command line. The advantage to using DSADD is that you can script these commands to automate the creation and provision of user accounts. DSADD adds a user to Active Directory . For example, to add a computer named JH-WXP-DSK to the Admin OU while authenticating as the domain administrator account, enter the following: dsadd computer CN=JH-WXP-DSK,OU=Admin,DC=hasselltech,dc=local -u administrator -p You will be prompted for a password. Here's another example: to add user sjohnson (for Scott Johnson, email address sjohnson@hasselltech.local with initial password "changeme") to the Sales OU and make him a member of the Presales group, use the following command: dsadd user cn=sjohnson,ou=sales,dc=hasselltech,dc=local -upn sjohnson@hasselltech.local -fn Scott -ln Johnson -display "Scott Johnson" -password changeme -email sjohnson@hasselltech.local -memberof cn=presales,ou=sales,dc=hasselltech,dc=local Again, you will be prompted for a password. You're getting the picture now. You also can add OUs with DSADD. To add an OU called support, use this command: dsadd ou cn=support,dc=hasselltech,dc=local 5.2.5.4. DelegationOne of the absolute best features within Active Directory is the ability to allow other users to take partial administrative control over a subset of your directorya process known as delegation. By delegating administrative authority, you can take some of the IT person's burden and place it elsewhere. For example, you might want to give one person in your department the power to reset passwords for other employees in a department. Or you might want to employ some part-time college students to staff a helpdesk and you want to give them the ability to create new users and to help other employees with lost passwords. You can accomplish this easily through Active Directory delegation. And there's even a wizard to help you do it, too. The entire process works something like this:
Let's get started. Within ADUC, select the organizational unit over which you want to delegate powers to others. Right-click it, and select Delegate Control from the pop-up context menu. The Delegation of Control Wizard appears. Click Next off the introductory screen, and the Users or Groups screen appears, as shown in Figure 5-39. Figure 5-39. The Users or Groups screen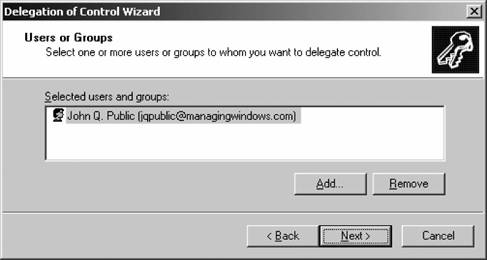 On this screen, click Add and identify the users or groups to which you want to have the powers assigned. Click Next when you've added the users, and the Tasks to Delegate screen appears, as shown in Figure 5-40. This screen lists the most common tasks you want to delegate, including such options as managing user accounts, resetting passwords, managing groups, and administering GP. For our example, let's select the second option (to reset user passwords), and click Next. Figure 5-40. The Tasks to Delegate screen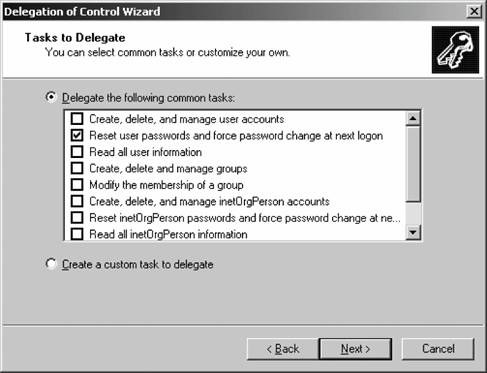 On the final screen of the wizard, you're asked to confirm your choices. Click Finish to do so, and the delegation is complete.
|
EAN: 2147483647
Pages: 171