Programmatic Security
|
| < Free Open Study > |
|
Every aspect of the application security model that can be implemented via declarative security should be as declarative security allows the deployer to change or alter policy according to the deployment situation. In some cases, however, programmatic security must be used. To use programmatic security, we will need to become familiar with three specific methods of the HttpServletRequest interface.
public java.lang.String getRemoteUser()
If the user has been authenticated, this method returns the name of the user, otherwise it returns null.
public boolean isUserInRole(java.lang.String role)
If the user has been authenticated, this method can be called to determine if a specific role has been mapped to the user.
public java.security.Principal getUserPrincipal()
This method returns a java.security.Principal object associated with the authenticated user. If no object is associated with the user it returns null.
As an example we'll create another servlet under the wroxapp1 application:
import javax.servlet.*; import javax.servlet.http.*; import java.io.*; public class SupersOnly extends HttpServlet { public void doGet(HttpServletRequest request, HttpServletResponse response) throws IOException, ServletException { PrintWriter out = response.getWriter();
We call getRemoteUser() to obtain the authenticated user name. We only print the welcome message if the user has been authenticated, and indeed has a role of supervisor:
String user = request.getRemoteUser(); out.println("<html><head><style>"); out.println("body {background-color:#FFFFFF;color:#000000;" + "font-family:verdana;font-size:10pt;}"); out.println("</style></head>"); if (user != null) { if (request.isUserInRole("supervisor")) { out.println("<body><h3>Welcome, " + user + ", you are a supervisor!</h3>"); } else { out.println("<body><h3>Sorry, " + user + ", but only supervisors can see the message.</h3>"); } out.println("</body>"); } out.println("</html>"); } }
Before trying this servlet, we need to make a servlet definition and a security constraint modification to the deployment descriptor of our application:
<?xml version="1.0" encoding="ISO-8859-1"?> <!DOCTYPE web-app PUBLIC "-//Sun Microsystems, Inc.//DTD Web Application 2.3//EN" "http://java.sun.com/dtd/web-app_2_3.dtd"> <web-app> <servlet> <servlet-name>trivial</servlet-name> <servlet-class>TrivialServlet1</servlet-class> </servlet> <servlet> <servlet-name>supercheck</servlet-name> <servlet-class>SupersOnly</servlet-class> </servlet> <security-constraint> <web-resource-collection> <web-resource-name>Protected Servlet</web-resource-name> <url-pattern>/servlet/*</url-pattern> </web-resource-collection> <auth-constraint> <role-name>supervisor</role-name> <role-name>worker</role-name> </auth-constraint> </security-constraint> <login-config> <auth-method>BASIC</auth-method> <realm-name>Wrox Supervisors Only</realm-name> </login-config> </web-app>
Restart Tomcat and navigate to http://localhost:8080/wroxapp1/servlet/supercheck. Login with "kim" and "efg789". You should see the following screen:
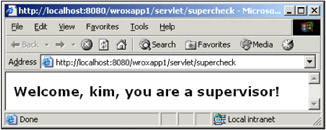
Restart your browser, and try again. This time, authenticate with "jane" and "abc123". Since jane is not a supervisor, we get the following message:
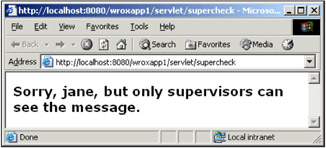
|
| < Free Open Study > |
|
EAN: 2147483647
Pages: 130